Interpol Arrests 260 Online Fraud Suspects in Africa
Interpol and African security forces arrested 260 suspects in online romance scam and sextortion, with victims losing nearly US$2.8 million.https://www.olamnews.com/world/africa/2669/interpol-arrests-260-online-fraud-africa/
🚨 Two 17-year-old Dutch teenagers arrested on espionage charges tied to Russia.
⚠️ Contacted on Telegram by pro-Russian hackers
⚠️ One caught with a wi-fi sniffer near Europol & Canadian embassy
⚠️ Espionage investigation ongoing
Cases like this show how youth can be pulled into nation-state cyber ops.
💬 How should governments handle underage suspects in espionage cases?
Follow @technadu for more real-time threat intelligence and cyber updates.
#Infosec #Cybersecurity #Russia #Espionage #Netherlands #Cybercrime #ThreatIntel
https://www.ad-hoc-news.de/boerse/ueberblick/europa-im-visier-raffinierter-phishing-attacken/68225610 #Cybercrime #Phishing #ProgressiveWebApps #PWA
🌍 INTERPOL’s Operation Contender 3.0 resulted in 260 arrests across 14 African nations.
Targets:
❤️ Romance scams
⚠️ Sextortion
💻 1,235 devices seized
💸 $2.8M in victim losses
This highlights the value of international partnerships in disrupting cyber-enabled crime.
💬 What more can be done to stop cross-border cybercrime networks?
🔔 Follow TechNadu for smart infosec analysis.
#CyberSecurity #Interpol #RomanceScams #Sextortion #Cybercrime #InfoSec #FraudPrevention #DigitalSafety
EFCC Raises Alarms Over Planned Protest To Take Up Arms Against Its Operatives ~ OsazuwaAkonedo
EFCC Raises Alarms Over Planned Protest To Take Up Arms Against Its Operatives ~ OsazuwaAkonedo #Cybercrime #Fraud #news #Nigeria #Ola #Olukoyede #Protest...
Alright team, it's been a pretty busy 24 hours in the cyber world! We've got a heap of critical zero-day exploits, some nasty new malware variants, significant data breaches, and a few interesting policy updates to chew on. Let's dive in:
GoAnywhere MFT Zero-Day Under Active Exploitation ⚠️
- A critical deserialisation vulnerability (CVE-2025-10035) in Fortra GoAnywhere MFT software, with a CVSS score of 10.0, has been actively exploited as a zero-day since at least September 10th, a week before public disclosure.
- Attackers are chaining an authentication bypass with the deserialisation flaw to achieve remote code execution (RCE), create backdoor admin accounts, and deploy secondary payloads like SimpleHelp and custom implants.
- Organisations using GoAnywhere MFT must immediately patch to versions 7.8.4 or 7.6.3, inspect logs for 'SignedObject.getObject' errors, and consider removing public internet exposure for the Admin Console.
📰 The Hacker News | https://thehackernews.com/2025/09/fortra-goanywhere-cvss-10-flaw.html
💻 Bleeping Computer | https://www.bleepingcomputer.com/news/security/maximum-severity-goanywhere-mft-flaw-exploited-as-zero-day/
Cisco Firewall Zero-Days Actively Exploited by State-Sponsored Actor 🚨
- UK NCSC and US CISA have issued urgent warnings and directives regarding active exploitation of Cisco ASA and FTD firewall vulnerabilities (CVE-2025-20333, CVE-2025-20362) by a sophisticated state-sponsored actor, UAT4356 (aka Storm-1849), linked to the ArcaneDoor campaign.
- The threat actors are deploying previously undocumented malware, RayInitiator (a persistent GRUB bootkit) and LINE VIPER (a user-mode shellcode loader), to maintain persistence, execute commands, exfiltrate data, and bypass VPN authentication.
- Federal agencies have a 24-hour deadline to patch and investigate, while all organisations are urged to update to fixed versions, remove end-of-life ASA devices, and check for ROMMON modifications on older ASA 5500-X series lacking Secure Boot.
🕵️ The Register | https://go.theregister.com/feed/www.theregister.com/2025/09/26/cisco_firewall_flaws/
🤫 CyberScoop | https://cyberscoop.com/cisa-emergency-directive-timeline-investigation/
📰 The Hacker News | https://thehackernews.com/2025/09/cisco-asa-firewall-zero-day-exploits.html
Volvo North America and Ohio County Hit by Ransomware 💸
- Volvo North America confirmed employee data, including names and Social Security numbers, was stolen in an August ransomware attack on its HR system provider, Miljödata, by the DataCarry group.
- The Miljödata breach, affecting 1.5 million people across Sweden, impacted numerous organisations beyond Volvo, including Swedish airline SAS and over 200 municipalities, with data types varying per victim.
- Separately, Union County, Ohio, disclosed a May ransomware attack that exfiltrated sensitive data for over 45,000 residents and employees, including SSNs, financial info, and medical records, though no ransomware group has publicly claimed responsibility.
🕵️ The Register | https://go.theregister.com/feed/www.theregister.com/2025/09/26/volvo_north_america_confirms_staff/
🗞️ The Record | https://therecord.media/ohio-ransomware-attack-impacts-45000/
Salesforce Faces Lawsuits Over Salesloft Breach ⚖️
- Salesforce is facing multiple class-action lawsuits alleging inadequate security after a cyberattack on its third-party IT supplier, Salesloft, led to the exposure of customer data.
- Attackers stole OAuth tokens from Salesloft's Drift app via a GitHub breach in March 2025, which were then used to access Salesforce data, impacting millions of individuals from various Salesforce customers like TransUnion and Farmers Insurance.
- While Salesforce maintains its own platform was not compromised, the lawsuits claim the company failed to implement sufficient cybersecurity procedures, causing victims to face risks of identity theft and fraud.
🕵️ The Register | https://go.theregister.com/feed/www.theregister.com/2025/09/26/salesforce_class_actions/
Evolving XCSSET macOS Malware Targets Developers 🍎
- A new variant of the XCSSET macOS malware has been observed in limited attacks, continuing its trend of infecting Xcode projects to spread and execute malicious payloads on developer machines.
- The updated malware includes enhanced capabilities such as targeting Firefox browser data using a modified HackBrowserData tool, a new clipboard hijacker for cryptocurrency addresses, and stealthier persistence via LaunchDaemon entries and fake System Settings.app files.
- Developers are urged to scrutinise Xcode projects from external sources, keep macOS updated, and use endpoint security tools to detect suspicious activity, as XCSSET's resilience and expanded modules pose a persistent threat to the Apple developer ecosystem.
📰 The Hacker News | https://thehackernews.com/2025/09/new-macos-xcsset-variant-targets-firefox-with-clipper-and-persistence-module.html
🕵️ The Register | https://go.theregister.com/feed/www.theregister.com/2025/09/26/microsoft_xcsset_macos/
💻 Bleeping Computer | https://www.bleepingcomputer.com/news/security/microsoft-warns-of-new-xcsset-macos-malware-variant-targeting-xcode-devs/
LockBit 5.0: A New Cross-Platform Ransomware Threat 🛡️
- Trend Micro warns that LockBit 5.0 is "significantly more dangerous" than previous versions, now capable of simultaneously targeting Windows, Linux, and VMware ESXi environments with enhanced evasion and obfuscation.
- The new variant features DLL reflection and aggressive anti-analysis packing for Windows, command-line directives for Linux, and VM encryption capabilities for ESXi, making it a comprehensive threat to enterprise stacks.
- Despite law enforcement disruptions earlier this year, LockBit's resurgence with version 5.0 and a refreshed affiliate program underscores the need for comprehensive cross-platform defences, especially for virtualisation infrastructure, as recovery is further complicated by its ability to terminate security processes and delete backups.
🕵️ The Register | https://go.theregister.com/feed/www.theregister.com/2025/09/26/lockbits_new_variant_is_most/
Salesforce Agentforce Vulnerable to Prompt Injection 🤖
- Security researchers demonstrated a "ForcedLeak" attack on Salesforce's Agentforce AI platform, using indirect prompt injection and an expired, re-registered trusted domain to exfiltrate sensitive CRM lead data.
- The vulnerability stemmed from a DNS misconfiguration and the Web-to-Lead feature, allowing attackers to embed malicious instructions in a description field with a large character limit, tricking the AI agent into querying and sending data to an attacker-controlled server.
- Salesforce has patched the flaw by enforcing trusted URL allow-lists for Agentforce and Einstein Generative AI agents, highlighting the critical need for proactive AI security and governance to prevent similar "trust boundary confusion" attacks.
🕵️ The Register | https://go.theregister.com/feed/www.theregister.com/2025/09/26/salesforce_agentforce_forceleak_attack/
Global Cybercrime Crackdowns and Espionage Arrests 🌍
- Interpol's coordinated operation in Africa led to 260 arrests across multiple countries, targeting transnational criminal networks running romance and sextortion scams via social media, with victims losing an estimated $2.8 million.
- The crackdown highlights a sharp rise in digital-enabled crimes across Africa and challenges faced by law enforcement due to legal framework gaps and resource shortages, underscoring the need for enhanced international cooperation.
- Separately, two 17-year-old Dutch teenagers were arrested on suspicion of espionage for pro-Russian hackers, allegedly tasked with using a "wifi-sniffer" near sensitive buildings in The Hague, following a tip from the Dutch signals intelligence agency.
🗞️ The Record | https://therecord.media/africa-cyber-fraud-crackdown-ghana-senegal-cote-divoire-angola-interpol
🗞️ The Record | https://therecord.media/teens-arrested-netherlands-reportedly-suspected-cyber-espionage-russia
UK Fines Robo-Callers for Targeting Vulnerable Individuals 📞
- The UK's ICO fined two British companies, Green Spark Energy and Home Improvement Marketing, a combined £550,000 for making illegal automated marketing calls to elderly and vulnerable people from offshore call centres.
- These companies used "robo call technology" (avatar software) with pre-recorded messages to pose as "local energy advisors," employing scare tactics about loft insulation to book appointments and sell products.
- The ICO urges the public to recognise signs of robo-calls, such as pauses before responses or limited flexibility in conversation, to help them investigate and take enforcement action against such predatory marketing practices.
🕵️ The Register | https://go.theregister.com/feed/www.theregister.com/2025/09/26/brits_warned_as_illegal_robocallers/
US Cyber Threat-Sharing Law Faces Sunset Amidst Government Shutdown Threat 🏛️
- The US Cybersecurity Information Sharing Act (CISA) of 2015 is set to lapse on October 1st, coinciding with a potential federal government shutdown, threatening a critical component of US cybersecurity policy.
- Supporters view CISA as the "backbone" of national cyber defence, facilitating vital threat intelligence sharing between government and businesses, preventing billions in losses, and fostering a culture of mutual aid.
- Detractors, including privacy advocates, have long criticised CISA for its perceived privacy invasions and insufficient protections for personal information, despite mandates for scrubbing unrelated PII from shared data.
🕵️ The Register | https://go.theregister.com/feed/www.theregister.com/2025/09/26/government_shutdown_cisa_law/
Microsoft Edge to Block Malicious Sideloaded Extensions 🔒
- Microsoft Edge is introducing a new security feature in November to detect and revoke malicious sideloaded extensions, aiming to protect users from threats not distributed through official channels.
- While developers can sideload extensions for testing, this feature addresses the risk of threat actors tricking users into installing dangerous third-party extensions that bypass official malware scans.
- This update is part of Microsoft's ongoing efforts to enhance Edge's security, which also includes updates to the Publish API for developers, warnings for performance-impacting extensions, an AI-powered scareware blocker, and HTTPS-First Mode.
💻 Bleeping Computer | https://www.bleepingcomputer.com/news/security/microsoft-edge-to-block-malicious-sideloaded-extensions/
#CyberSecurity #ThreatIntelligence #Ransomware #ZeroDay #Vulnerability #APT #Malware #SupplyChainAttack #DataBreach #AI #PromptInjection #InfoSec #Cybercrime #Policy #Privacy #IncidentResponse
#CoOp says it lost $107 million after #ScatteredSpider attack

Co-op says it lost $107 million after Scattered Spider attack
The Co-operative Group in the U.K. released its interim financial results report for the first half of 2025 with a massive loss in operating profit of £80 million ($107 million) due to the cyberattack it suffered last April.
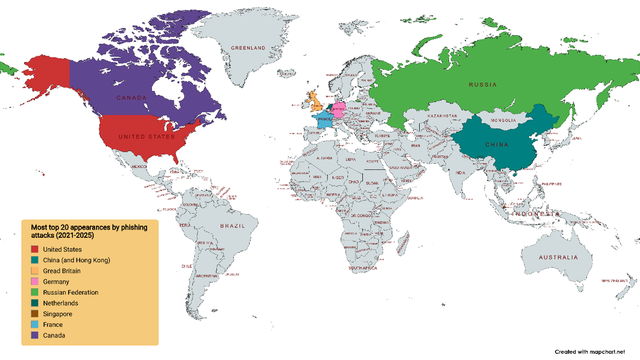
Phishing in the 2020s: Where in the World Are Phishing Pages Hosted?
In this post, we look at the top countries where phishing pages have been hosted. Teaser: Of the thirty-two countries that have appeared in the top twenty over a 5-year period, ten have appeared every year.
https://interisle.substack.com/p/phishing-in-the-2020s-where-in-the
#phishing #hosting #cybercrime #ASN
subscribe: https://interisle.substack.com/subscribe