The previous Monday, @troyhunt the creator of @haveibeenpwned made another stop on his Have I Been Pwned Alpine Grand Tour, visiting countries like Germany, France, Italy, and Switzerland to discuss his work. Several Zurich user groups were fortunate to hear him speak on various topics and join him for drinks afterward. His presentation covered his experience testifying before the U.S. Congress, some of the most significant breaches tracked on the platform, and insights into how Have I Been Pwned operates
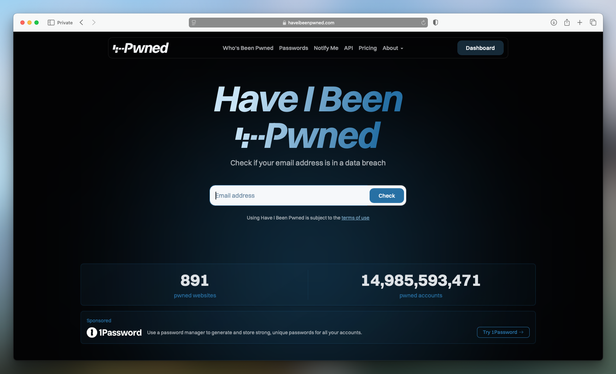
After discovering that the data is accessible via the API and noticing the lack of a visualization tool, I dedicated a few evenings to building haveibeenpwned.watch. This single-page website processes and presents data on leaks from Have I Been Pwned, with daily updates.
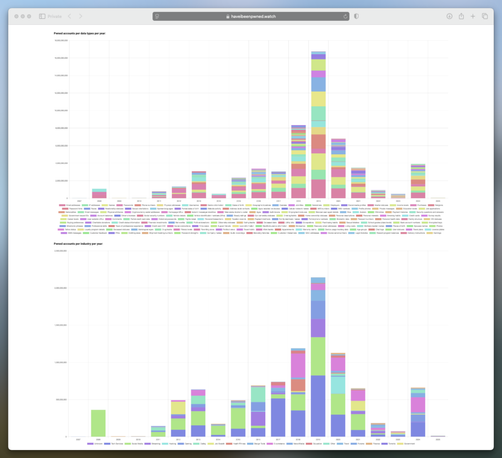
The site provides details on the total number of recorded breaches, the number of unique services affected, and the total accounts compromised. Charts break down the data by year, showing the number of breaches, affected accounts, average accounts breached per year, accounts by data type, and accounts by industry. Additionally, tables highlight the most recent breaches, the most significant ones, and the services with the highest number of compromised accounts.
Though simple, the website can be a useful resource for use cases like strategic security planning, cybersecurity sales, risk assessment, or simply tracking trends in the security landscape.
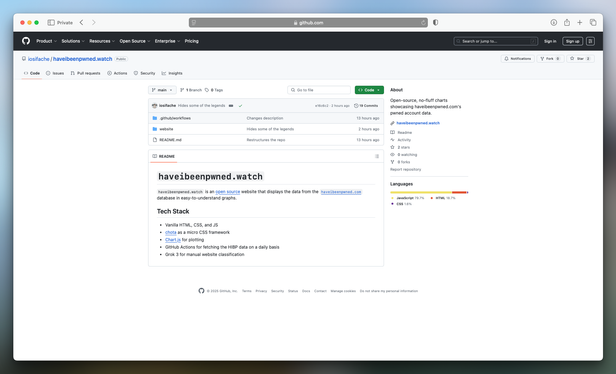
The website is open source, with its repository hosted on GitHub.
Feel free to share any feedback or submit a pull request if you’d like to contribute.
Troy, thank you for hosting these in-person talks and for creating this essential service that the internet relies on!
[1] https://haveibeenpwned.watch
[2] https://github.com/iosifache/haveibeenpwned.watch