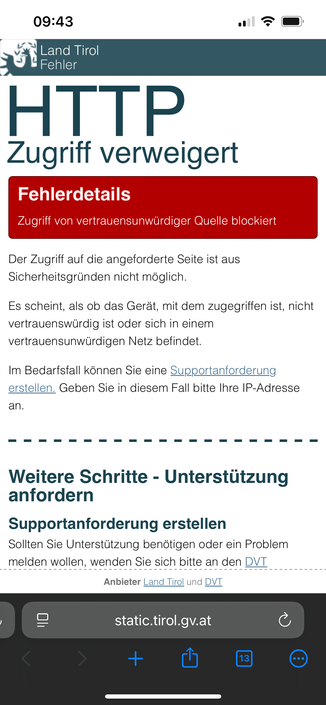
Update: I heard back from the people running the system. Apparently it isn’t a geoblock, but the specific IPs my requests were coming from were blocked because of abuse from that CDN (bunny.net). The error has been fixed. (Now I wonder if Fraenk hosts their stuff on Bunny.net, or if it’s the DNS resolver I am using 🤔)
Anyway, in the future, access to the warnings should be possible.
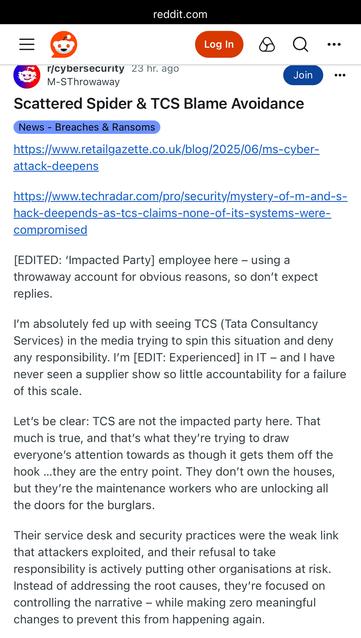
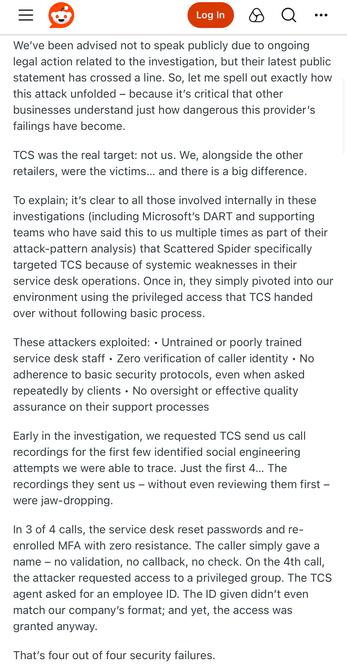
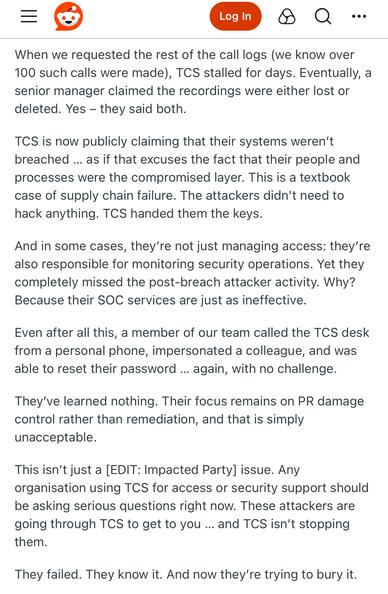
Also, they saw this toot and referenced it in their reply 😅.
https://infosec.exchange/@hacksilon/114765561556000011
Max Maass :donor: (@hacksilon@infosec.exchange)
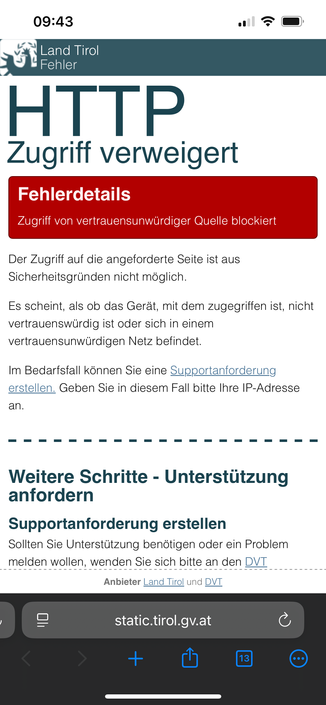
Attached: 1 image Today in #ITSecurity gone wrong: I am in Austria as a German. I just received a notification via cell broadcast about a fire in the area. The broadcast contains a URL - but this URL is only accessible from an Austrian IP address. My LTE roaming IP isn’t allowed. So… I guess I just suffocate because I have the wrong IP address, then? 😅