Organisers of the annual Virus Bulletin conference.
Virus Bulletin
- 2.5K Followers
- 57 Following
- 1.9K Posts
Organisers of the annual Virus Bulletin conference.
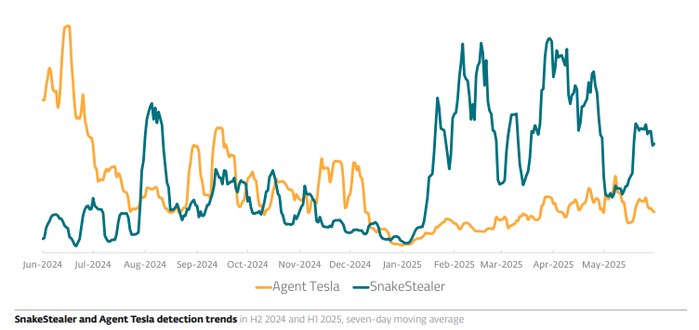
The threat actors behind Agent Tesla have reportedly lost access to the servers with the malware’s source code. A successor appeared almost immediately – another #MaaS threat, known as #SnakeStealer or #SnakeKeylogger, has claimed the number one spot.
Recommended as a suitable replacement directly in Agent Tesla’s Telegram channel, SnakeStealer now takes up almost a fifth of all infostealer detections registered by ESET telemetry. Between H2 2024 and H1 2025, its detections more than doubled.
If you want to find out more information about this changing of the guard in the infostealer threat landscape, head on over to #ESETThreatReport: https://welivesecurity.com/en/eset-research/eset-threat-report-h1-2025
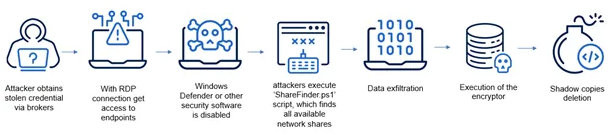
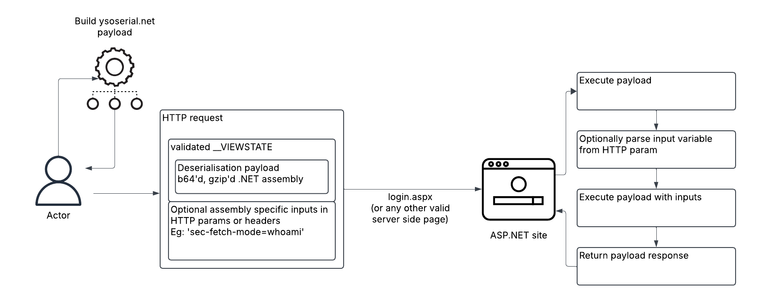
🚨 Fake 7-Zip installer exfiltrates Active Directory files.
A #malicious installer disguised as 7-Zip steals critical Active Directory files, including ntds.dit and the SYSTEM hive, by leveraging shadow copies and exfiltrating the data to a remote server.
🥷 Upon execution, the #malware creates a shadow copy of the system drive to bypass file locks and extract protected files without disrupting system operations.
🎯 It then copies ntds.dit, which contains Active Directory user and group data, and SYSTEM, which holds the corresponding encryption keys.
The malware connects to a remote server via SMB using hardcoded credentials. All output is redirected to NUL to minimize traces.
👨💻 #ANYRUN Sandbox makes it easy to detect these stealthy operations by providing full behavioral visibility, from network exfiltration to credential staging, within a single interactive session.
🔍 See analysis session: https://app.any.run/tasks/7f03cd5b-ad02-4b3a-871f-c31ac0f5dc15/?utm_source=mastodon&utm_medium=post&utm_campaign=fake_7zip&utm_term=090725&utm_content=linktoservice
This technique grants the attacker full access to ntds.dit dump, allowing them to extract credentials for Active Directory objects and enables lateral movement techniques such as Pass-the-Hash or Golden Ticket.
🚀 Analyze and investigate the latest malware and #phishing threats with #ANYRUN.
#ExploreWithANYRUN
How does Russia’s Sandworm unit exploit pirated software to target Ukraine?
Join Arda Buyukkaya from EclecticIQ at VB2025 in Berlin to uncover how cyber operations can turn everyday behaviour into large-scale threats.
📅 Sept 25 | 09:30–10:00 | Green Room
Find out more about this talk 👉 https://tinyurl.com/e9anehex
👾 #Ducex is a packer used by #Triada trojan. It stands out due to:
🔹 Native code
🔹 Encrypted functions & strings
🔹 Self-debugging
🔹 Signature checks
🔹 Frida & Xposed detection
👨💻 Read our technical analysis to see how it works: https://any.run/cybersecurity-blog/ducex-packer-analysis/?utm_source=mastodon&utm_medium=post&utm_campaign=ducex_analysis&utm_term=080725&utm_content=linktoblog