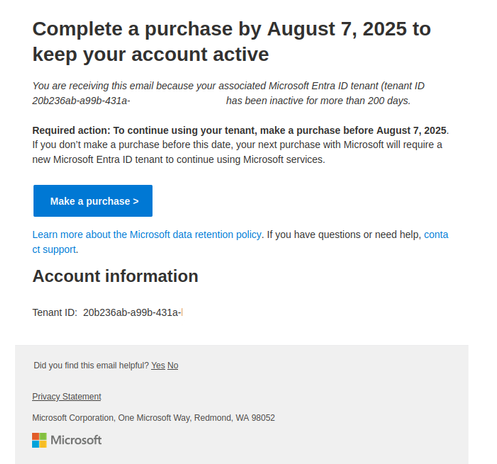
I recently received an email that at first glance appeared to be a well-crafted phishing message, warning that my Microsoft Entra ID was going to expire in a month if I didn't make a purchase. The only piece of information in the message was my supposed Entra ID.
After checking with Microsoft it appears this automated message is legitimate, and it is in reference to a Microsoft Teams trial account I created for a day and then abandoned. But apart from the Entra ID, which isn't mentioned in any prior communications from Microsoft, there is zero context for the user.
How hard would it be for Microsoft to include just a tiny bit more information in each message? Like, "Hey, this message is about an account created 5 years ago, for Teams" or something. Otherwise these marketing messages train users to fall for phishing scams.
 🌻
🌻