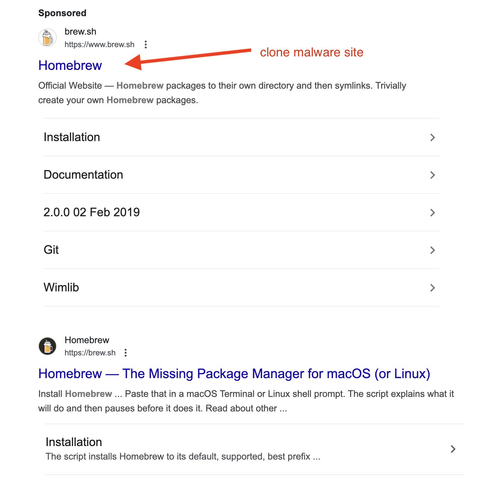
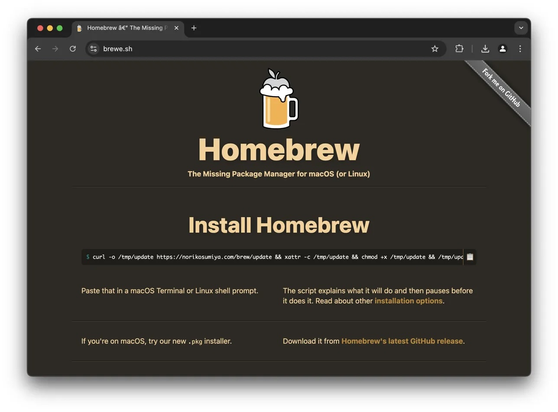
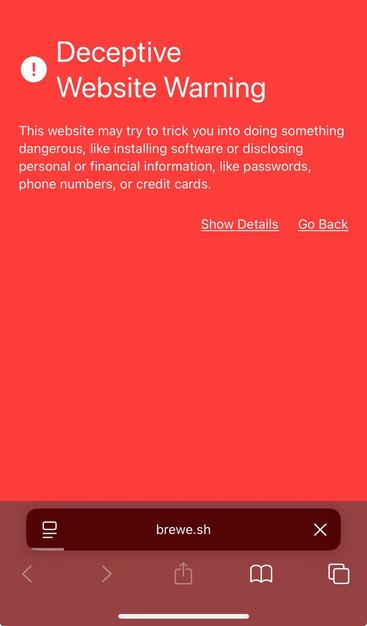
Developers, please be careful when installing Homebrew. Google is serving sponsored links to a Homebrew site clone that has a cURL command to malware. The URL for this site is one letter different than the official site.
Note: Google allows the ad sponsors to specify an URL that will be displayed on the ad (original brew.sh here), but the click takes you to the malware domain brewe.sh.