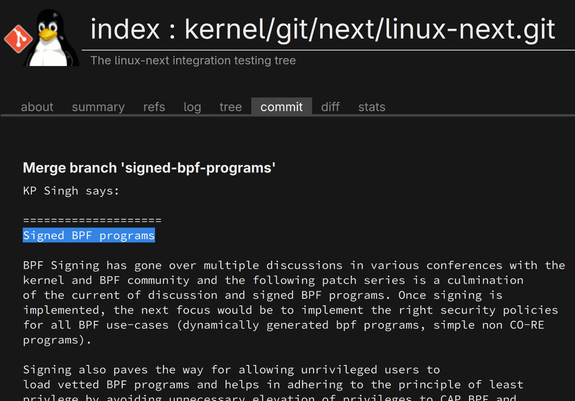
Support for signing #BPF programms has hit #Linux-next and thus is slated for inclusion in #kernel 6.18:
Quote from that merge commit: ""BPF Signing has gone over multiple discussions in various conferences with the kernel and BPF community and the following patch series is a culmination of the current of discussion and signed BPF programs. […]
Signing also paves the way for allowing unprivileged users to load vetted BPF programs and helps in adhering to the principle of least privlege […]""
See also the recent @lwn article "Possible paths for signing BPF programs": https://lwn.net/Articles/1031854/