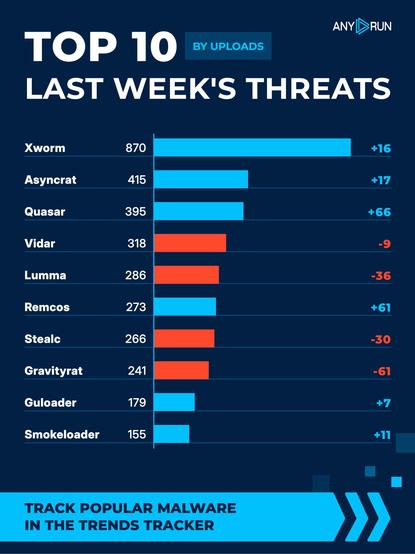
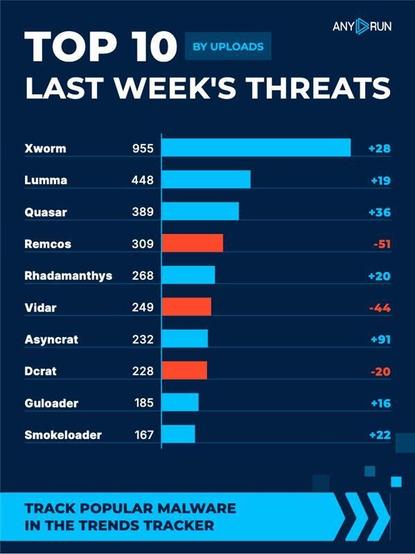
Top 10 last week's threats by uploads 🌐
⬆️ #Xworm 870 (854)
⬆️ #Asyncrat 415 (398)
⬆️ #Quasar 395 (329)
⬇️ #Vidar 318 (327)
⬇️ #Lumma 286 (322)
⬆️ #Remcos 273 (212)
⬇️ #Stealc 266 (296)
⬇️ #Gravityrat 241 (302)
⬆️ #Guloader 179 (172)
⬆️ #Smokeloader 155 (144)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=081225&utm_content=linktoregister#register