Happy Monday everyone!
Just got done reading an incredible article from ESET researchers describing an APT group that was long thought to be inactive alive in well! #FamousSparrow is a China-aligned APT group that has had no publicly documented activity since 2022 and was found using two previously undocumented versions of their backdoor, SparrowDoor. They used a mix of publicly available and custom tools for their attack ultimately leading to the deployment of SparrowDoor and ShadowPad (a privately sold backdoor). This report gets more and more interesting as you go so please go take the time to read it! Enjoy and Happy Hunting!
You will always remember this as the day you finally caught FamousSparrow
https://www.welivesecurity.com/en/eset-research/you-will-always-remember-this-as-the-day-you-finally-caught-famoussparrow/
Intel 471 Cyborg Security, Now Part of Intel 471 #ThreatIntel #ThreatHunting #ThreatDetection #HappyHunting #readoftheday
China-linked APT group #FamousSparrow (aka Salt Typhoon) has resurfaced, targeting the US and LATAM orgs with an upgraded version of #SparrowDoor malware.
Read: https://hackread.com/china-famoussparrow-apt-americas-sparrowdoor-malware/
Chinese #FamousSparrow hackers deploy upgraded #malware in attacks
Famous Sparrow APT Group: Enhanced Cyber Arsenal and Global Threats
https://thedefendopsdiaries.com/famous-sparrow-apt-group-enhanced-cyber-arsenal-and-global-threats/
#famoussparrow
#aptgroup
#cyberespionage
#shadowpad
#cybersecurity
Hey #CyberSecurity pros! 👋 Ready to dive into the latest threats and breaches making headlines?
Our latest blog post is packed with need-to-know info to keep you ahead of the curve.
🗞️ https://opalsec.io/daily-news-update-thursday-march-27-2025-australia-melbourne/
Here's a quick rundown of what's inside:
🕵️♂️ FamousSparrow's Return: The Chinese government-backed hacking group is back, targeting organizations in North America. Important distinction: ESET insists on tracking them separately from Salt Typhoon. Remember to prioritize TTPs and IOCs/IOAs accordingly!
🗄️ RedCurl's Ransomware Twist: This corporate espionage group is now deploying "QWCrypt" ransomware, targeting Hyper-V servers. Phishing emails with malicious IMG attachments are the initial attack vector.
😬 StreamElements Data Breach: A third-party service provider suffered a breach, exposing data of 210,000 customers.!
🏛️ NSW Court System Data Theft: Sensitive documents, including AVOs, were stolen from the NSW Online Registry website. This could have serious consequences for victims of domestic violence.
👨🎓 NYU Website Defacement: A hacker compromised NYU's website, leaking personal data of over 1 million students. Even with good intentions, the collateral damage is unacceptable.
💰 Defense Contractor Fined: MORSE Corp will pay millions for failing to meet federal cybersecurity requirements. Third-party risk management is crucial!
🤖 Atlantis AIO Automates Credential Stuffing: This new platform automates credential stuffing attacks against 140 online services. Stay vigilant against brute force attacks!
🚨 Chrome Zero-Day Exploited: Google patched a zero-day vulnerability exploited in espionage campaigns targeting Russian organizations. Keep your browsers updated!
👦 UK Warns of 'Com Networks': The UK's NCA is warning of a growing threat from online networks of teenage boys who are "dedicated to inflicting harm and committing a range of criminality." A very worrying trend that we need to be aware of.
Ready for the full scoop? Read the full blog post here 👉 https://opalsec.io/daily-news-update-thursday-march-27-2025-australia-melbourne/
#Cybersecurity #InfoSec #DataBreach #Ransomware #ThreatIntelligence #DataPrivacy #ZeroDay #FamousSparrow #RedCurl #StreamElements #NSWCourts #NYU #MORSECorp #AtlantisAIO #Chrome #ComNetworks #SecurityNews #CybersecurityThreats #InfoSecurity #CyberAttack #DataSecurity #PrivacyMatters #Vulnerability #Cybercrime #ThreatActor #ESET #SaltTyphoon #NIST #ZeroTrust #SaltTyphoon #CriticalInfrastructure

Daily News Update: Thursday, March 27, 2025 (Australia/Melbourne)
Audio Summary: Thursday, March 27, 2025 (Australia/Melbourne)0:00/292.1521× Chinese ‘FamousSparrow’ Hackers Resurface The Chinese government-backed hacking group FamousSparrow, thought to be dormant since 2022, has allegedly been targeting organisations in the U.S., Mexico, and Honduras. ESET researchers discovered suspicious activity on a U.S. trade
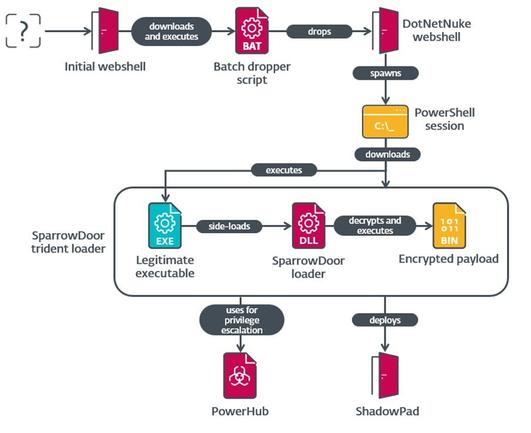
While helping the 🇺🇸 company remediate the compromise, we discovered FamousSparrow’s toolset hidden within the network. It included two previously undocumented versions of the group’s flagship backdoor, #SparrowDoor, one of them modular.
Both of these versions are a significant improvement over the older ones, especially in terms of code quality and architecture, implementing parallelization of time-consuming commands.
This campaign is also the first documented time that FamousSparrow used #ShadowPad, a privately sold modular backdoor known to only be supplied to threat actors affiliated with China.
IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/famoussparrow
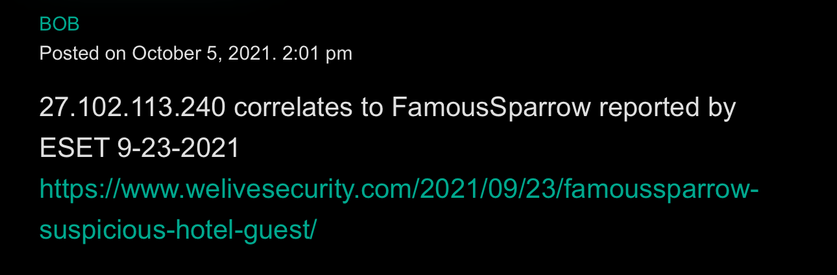
Looks #FamousSparrow’s link to #GhostEmperor is an IP address shared between the two groups (used around the same time)
Comment found on https://securelist.com/ghostemperor-from-proxylogon-to-kernel-mode/104407/
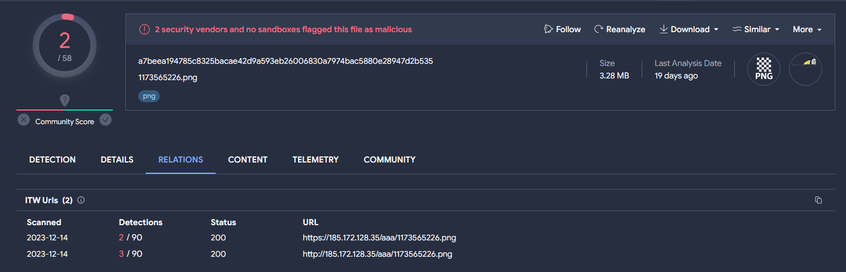
Surprised no one's looked into a7beea194785c8325bacae42d9a593eb26006830a7974bac5880e28947d2b535 yet
It's a few weeks old now
Might be related to #FamousSparrow ?
ITW https://185.172[.]128.35/aaa/1173565226.png