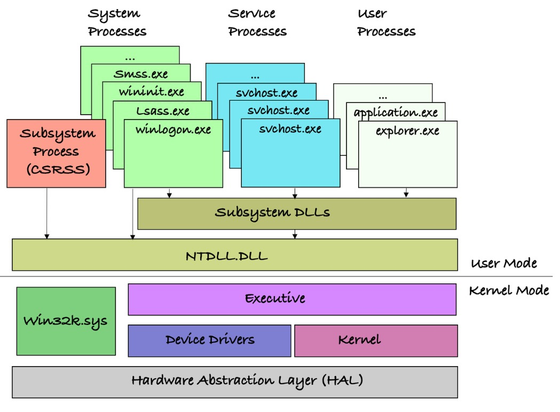
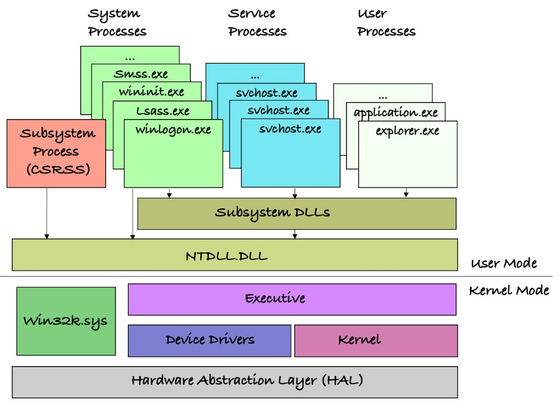
#SonicWall releases #SMA100 #firmware update to wipe #rootkit #malware
SonicWall SMA 100 devices are under threat from a stealthy malware that clings even after updates, stealing sensitive credentials. Could your network be at risk? Dive into this unfolding security saga.
#overstepmalware
#sonicwall
#rootkit
#firmwareupdate
#cybersecurity
#unc6148
#ransomware
#cve202440766
#networksecurity
#threatintel
DeerStealer Malware Campaign: Stealth, Persistence, and Rootkit-Like Capabilities
Pulse ID: 68d242461771a35fa568a2d6
Pulse Link: https://otx.alienvault.com/pulse/68d242461771a35fa568a2d6
Pulse Author: Tr1sa111
Created: 2025-09-23 06:46:30
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#CyberSecurity #InfoSec #Malware #OTX #OpenThreatExchange #Rootkit #bot #Tr1sa111
DeerStealer Malware Campaign: Stealth, Persistence, and Rootkit-Like Capabilities
DeerStealer is a sophisticated information-stealing malware that targets a wide range of user and system data. It employs deception techniques, persistence mechanisms, and rootkit-like capabilities to evade detection and maintain stealth on compromised systems. The malware uses signed executables, legitimate DLLs, and multi-stage execution to perform its malicious activities. It establishes persistence through scheduled tasks and employs auto-elevated COM objects to bypass User Account Control. DeerStealer's adaptive design allows it to switch C2 servers and use obfuscated files for effective data exfiltration. The malware is actively sold and supported through dark-web forums and Telegram channels, posing a significant threat to both individuals and organizations.
Pulse ID: 68ce938ae34f725fce8b67a4
Pulse Link: https://otx.alienvault.com/pulse/68ce938ae34f725fce8b67a4
Pulse Author: AlienVault
Created: 2025-09-20 11:44:10
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#CyberSecurity #InfoSec #Malware #OTX #OpenThreatExchange #RAT #Rootkit #SMS #Telegram #bot #AlienVault
Fantastic Rootkits: And Where to Find Them:
+ part_1: https://www.cyberark.com/resources/all-blog-posts/fantastic-rootkits-and-where-to-find-them-part-1
+ part_2: https://www.cyberark.com/resources/all-blog-posts/fantastic-rootkits-and-where-to-find-them-part-2
#rootkit #windows #cybersecurity #malware #arm #informationsecurity
Fantastic Rootkits: And Where to Find Them:
+ part_1: https://www.cyberark.com/resources/all-blog-posts/fantastic-rootkits-and-where-to-find-them-part-1
+ part_2: https://www.cyberark.com/resources/all-blog-posts/fantastic-rootkits-and-where-to-find-them-part-2
#rootkit #windows #cybersecurity #malware #arm #informationsecurity
"Fantastic rootkits and where to find them"
Decent mini blog series #windows #rootkit
https://www.cyberark.com/resources/all-blog-posts/fantastic-rootkits-and-where-to-find-them-part-1
https://www.cyberark.com/resources/all-blog-posts/fantastic-rootkits-and-where-to-find-them-part-2
BIOS Problem with Installing Ubuntu #boot #systeminstallation #bios #reset #rootkit
@Uair Yeah, I also remember #MagicLantern, tho #Carnivore was a #Rootkit if I'm not mistaken...
Granted, the #NRO literally put #USA202 aka. #MENTHOR4 next to #Thuraya-2...
- Again: Cold OSINT...
Inside the Kimsuky Leak: How the 'Kim' Dump Exposed North Korea's Credential Theft Playbook
A data breach attributed to a North Korean-affiliated actor known as "Kim" has provided new insights into Kimsuky (APT43) tactics and infrastructure. The actor's operations focus on credential-based intrusions targeting South Korean and Taiwanese networks, utilizing Chinese-language tools and infrastructure. The leaked data includes bash histories, phishing domains, OCR workflows, compiled stagers, and rootkit evidence, revealing a hybrid operation between DPRK attribution and Chinese resource utilization. The actor demonstrated sophisticated credential harvesting techniques, including targeting South Korea's Government Public Key Infrastructure (GPKI) and reconnaissance of Taiwanese government and academic institutions. The leak exposes the evolution of DPRK cyber capabilities and highlights the complex attribution challenges in modern nation-state cyber operations.
Pulse ID: 68bea37d4c7b1bb28149b407
Pulse Link: https://otx.alienvault.com/pulse/68bea37d4c7b1bb28149b407
Pulse Author: AlienVault
Created: 2025-09-08 09:35:57
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#Chinese #CredentialHarvesting #CyberSecurity #DPRK #DataBreach #Government #ICS #InfoSec #Kimsuky #Korea #NorthKorea #OTX #OpenThreatExchange #Phishing #RAT #RCE #Rootkit #SouthKorea #UK #bot #AlienVault