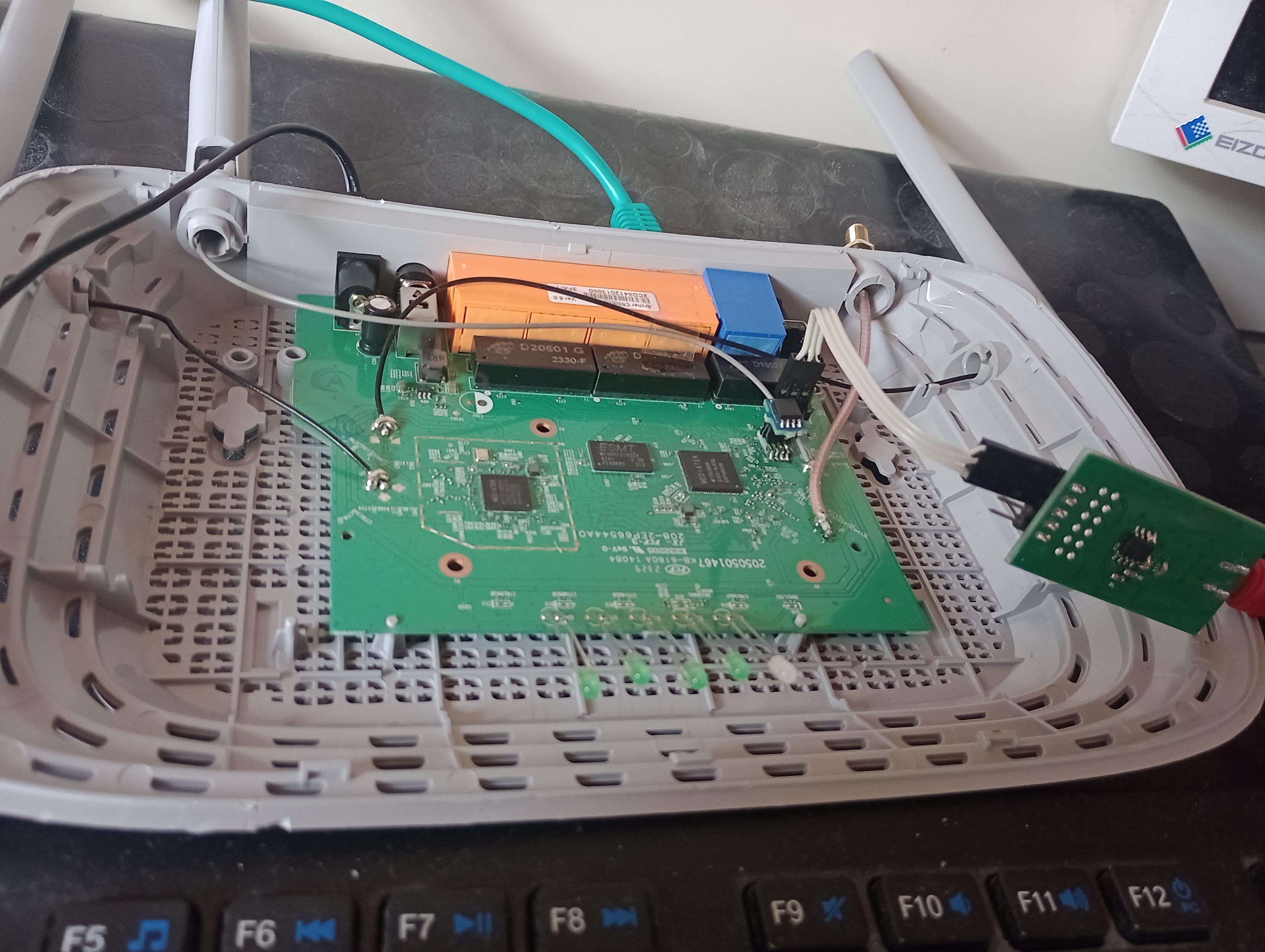
I have been having fun with a #reverseengineering #sidequest seeing if I can get root access to a Tenda 4G185 MiFi device which runs Linux and is based on ZTE ZX297520V3. Inspired by @ge0rg Sadly the standard exploits seem to have been patched (no injections through the web interface) but I did manage to get serial access but can't seem to login despite everything pointing to the password being 'admin'.
I've managed to get it into a special debug mode called AMT mode, it has opened up 3 serial ports over usb, the first seems to use a protocol called AMT, the device has run a binary called `zte_amt` - I've never come across this and searches bring up Android Multi Tool or a lot of Intel AMT stuff which I don't think is correct - has anyone come across this protocol?
There is a suggestion there might also be #adb might be running as well so I'm going to focus on that for now