Post-quantum encryption!
@rosenpass is presenting their work at #NGIForum25 on how they - already now - are building post-quantum encryption for the VPN @wireguardvpn
Much interesting..
Post-quantum encryption!
@rosenpass is presenting their work at #NGIForum25 on how they - already now - are building post-quantum encryption for the VPN @wireguardvpn
Much interesting..
FOSS scaling challenges:
@renchap: Scaling technology is easy. Scaling the other parts, like trust and safety, is hard. NGI funds the tech. Need to have funding for scaling other parts.
Ali Gonzalez: We are looking for public investment, not VC.
@ldubost: Goal is to grow product revenue alongside grant funding. One funds dev, one funds non-dev needs.
@kora: Need to ask where do we want to grow? When growth directions arent aligned with standard growth paths, funding can be hard.
Panel on NGI impact stories from grantees
Martin Schanzenberger shared TalDir, enabling the "PayPal use case" for @Taler
@renchap shared quote posts and the decentralized content discovery features coming to @Mastodon
@ldubost shared how NGI funding brought stability to the funding for professional developers and credibility to @CryptPad
@kora shared Rosenpass.eu, a post-quantum-secure add-on for WireGuard
Ali Gonzalez shared @decidim to digitally engage citizens in governance
“I measure all software by its ability to support peace and democracy.” —@kora, answering their prior audience question about what the moonshot goal should be
I think I found the first use of AIs that would actually interest me: A lemma search engine.
You input a semi-formal lemma in whatever grammar and the search engine spits out papers and other resources that use, prove, or otherwise relate to the lemma.
Our paper
"Agile, post-quantum secure cryptography in avionics"
was just released in open access! :D
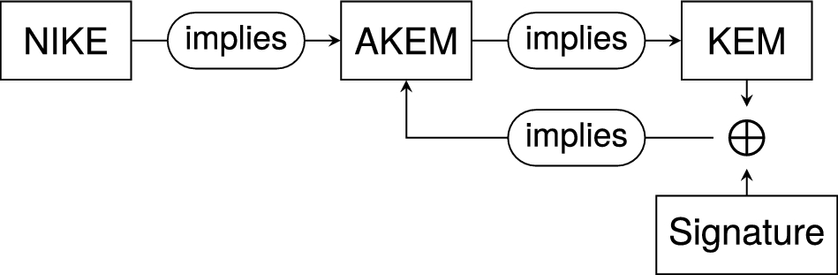
To introduce a post-quantum-secure encryption scheme specifically for use in flight-computers, we used avionics’ module-isolation methods to wrap a recent encryption standard (HPKE-Hybrid Public Key Encryption) within a software partition. This solution proposes an upgrade to HPKE, using quantum-resistant ciphers (Kyber/ML-KEM and Dilithium/ML-DSA) redundantly alongside well-established ciphers, to achieve post-quantum security. Because cryptographic technology can suddenly become obsolete as attacks become more sophisticated, “crypto-agility”—the ability to swiftly replace ciphers—represents the key challenge to deployment of software like ours. Partitioning is a crucial method for establishing such agility, as it enables the replacement of compromised software without affecting software on other partitions, greatly simplifying the certification process necessary in an avionics environment. Our performance measurements (Sect. 5) provide initial evidence that both the memory and cpu performance characteristics of this solution are suitable for deployment in flight-computers. Performance measurements show a memory use of 5 MB of RAM and under 200 KB of stack usage for encryption, compared to a baseline implementation without any encryption; decryption is much more lightweight (under 300 KB RAM overhead, under 100 KB of stack requirement overhead). Generally, the post-quantum algorithms benchmarked where faster than their pre-quantum alternatives; due to the use of hybrid security this leads to a performance overhead of just about 90% compared to the pre-quantum only variant. The implementations benchmarked are optimized for CPU-performance and alternative, lower quality implementations showed much more modest memory requirements, leading us to conclude that there is much room for optimization, targeting use-case specific tradeoffs between memory use and performance.