Dijkstra. Now there's a name I recognize, thanks to the hours spent getting my head around solving shortest path algorithms.

Digital Mark λ ☕️ 🔪 🙄 (@mdhughes@appdot.net)
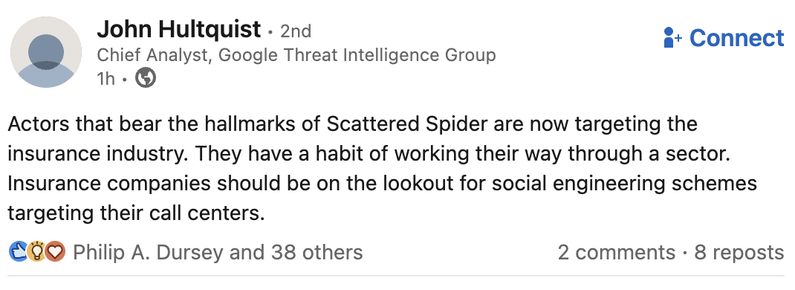
Attached: 1 image Structured Programming by O.-J. Dahl, E. W. Dijkstra, C. A. R. Hoare https://archive.org/details/Structured_Programming__Dahl_Dijkstra_Hoare/page/n1/mode/2up #programming I've read EWD's Discipline of Programming, which I assume contains a lot of this but refined? I don't always agree with EWD but he was worth "arguing" with.