Professional: DFIR / Incident Management lead
Volunteer: Search & Rescue specialist, CERT trainer, Parrot handler
Amateur: Cello & Guitar
(was: 0xMatt on twitter)
| Twitter: | 0xMatt |
| Website: | foofus.com |
| Keybase: | amuse |

Professional: DFIR / Incident Management lead
Volunteer: Search & Rescue specialist, CERT trainer, Parrot handler
Amateur: Cello & Guitar
(was: 0xMatt on twitter)
| Twitter: | 0xMatt |
| Website: | foofus.com |
| Keybase: | amuse |
This is why now that I am in a career place that I can do so, I make a point to support foss.
Immich 'supporter level" license, paid adblock, etc.
@DefectiveWings I don't actually have a very smart house.
Roku + my TV has all its smart features turned off.
Nest cams (outside of the house).
I did enable Wi-Fi feature on my range and oven because that's an ADHD accommodation that will keep the house from burning down 😂
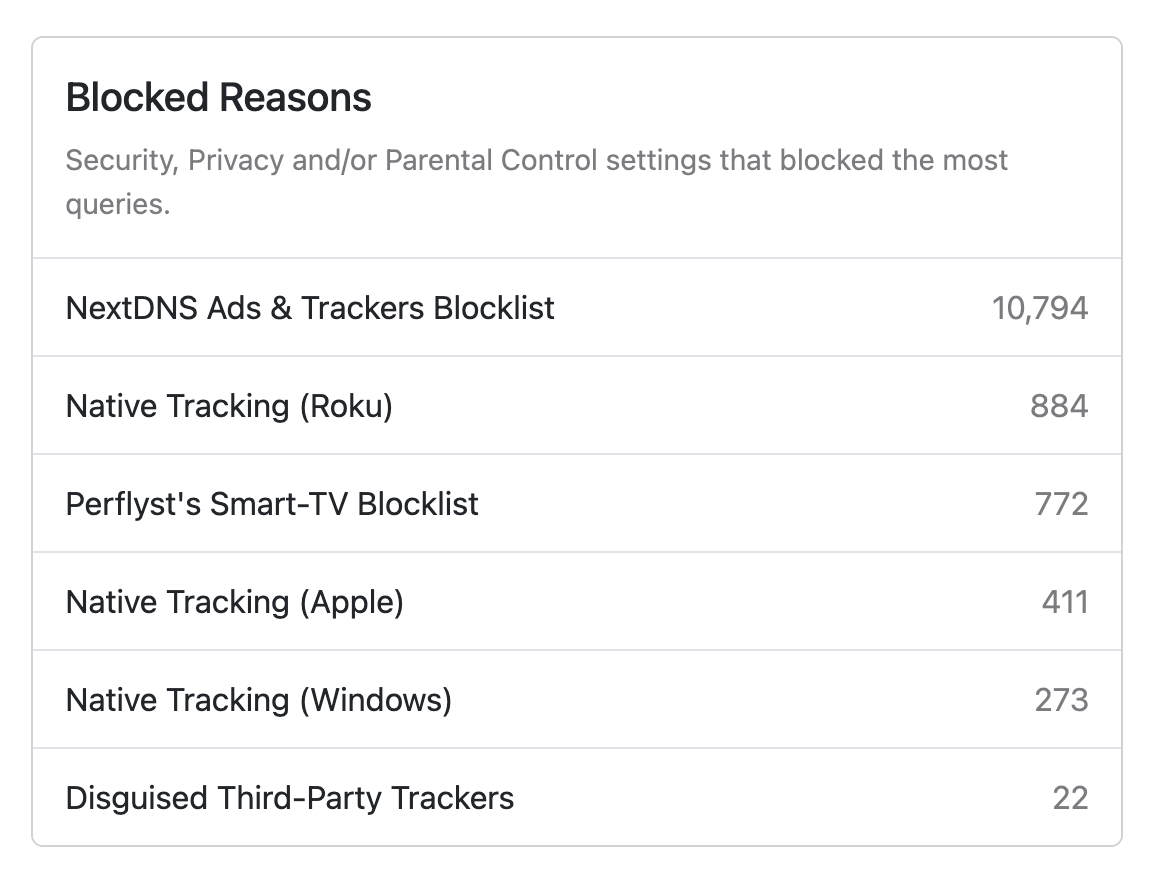
NextDNS has been a really great privacy decision. This is ONE day's traffic.
Yeah, I could do all this with Unbound and pushing local DoH servers and maintaining them, but even as much as I love running infrastructure, for $2 a month it's just too easy a win.
This NextDNS blocking UX feels like a trap.
It defaults to "on" and you have to either accept web censorship based on unknown third-party criteria OR essentially say "I DO want to see child abuse material".
It's the "Yes or no: do you still beat your wife?" of UX settings.
Dear streaming customer, as of $very_soon your streaming bundle, $things_you_like will no longer include $main_thing_you_like. To see that you'll need $different_tier.
We value your business, which is why we constantly renege on the deal we made with you.
- Every streamer ever
@bassthang I definitely didn't mean to imply unaudited access 😁
But this is a great use case. If the attacker potentially accessed pii, then you need your response team to access the pii so that they can notify people that their pii may have been accessed!
I was mulling over a principle of incident response today and wondered what others in my field might think.
Yes or no: "To operate effectively, incident responders need to be able to obtain at least the same level of access to a system as the attacker has potentially obtained."