https://overeducated-redneck.net/blurgh/netbsd-chroot-isolation.html
https://overeducated-redneck.net/blurgh/netbsd-chroot-isolation.html
Process Isolation on NetBSD with chroot(2)
Mainboard: Micronics Spitfire
CPU: Pentium II 233 MHz
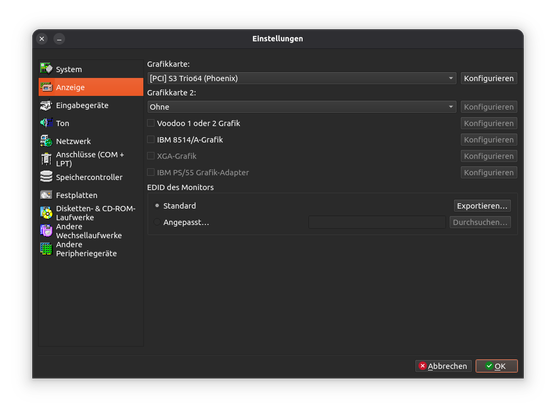
Graphics card: S3 Trio64
Network card: RTL8139
#86box #retrohardware #retrocomputing #oldhardware #emulation #snac #snac2 #netbsd #openbsd
I'm slowly getting myself back to having a personal website.
First blog post is up. Trying to write an intro post felt weird, so I just wrote a technical article. It's about how I set up the chroot that caddy and anubis run in on the server (running #NetBSD 10.1):
https://overeducated-redneck.net/blurgh/netbsd-chroot-isolation.html
Just added another sensor to #sysinspect — "procnotify".
In this very short demo: as long as a new process is "bash" (use "zsh", LOL), #sysinspect SIGKILLs it.
Key points:
1. procnotify detects a new process
2. a model is getting triggered (in this case just a process killer)
Currently:
Native: #linux, #netbsd
Others: external fallback path.
@pheonix A |d|i|g|i|t|a|l| DNARD prototype running #NetBSD/shark, C-news and (mgetty+sendfax with a 28.800bps Telefone modem).
Maybe the modem is slightly older.
If we leave computing: a LCD weather station with an additional 433 Mhz coupled outside temperature/humidity sensor might beat it; SWMBO inherited it from her father who had it several years before. His bedroom lamp, ca. 1970s, is in ours now. An #POTS phone from 7/1990 on my desk (connected via an #VOIP adapter to my #Asterisk)
While writing my article, it became clear to me how much responsibility — and especially experience — is required to touch areas like UVM or NPF inside NetBSD.
I’ve learned a lot over the past weeks. But I’m also honest enough to say: I don’t yet have the depth of experience needed to modify those subsystems responsibly.
So I made a conscious decision.
I’ve created a new experimental branch for secmodel_jail / jailctl / jailmgr that is strictly additive:
- No changes to existing kernel code paths
- No UVM hooks
- No NPF integration
- No hidden coupling between subsystems
It adds new code only.
The reason is simple: even without deep UVM or NPF integration, the security model already delivers significant practical value for me. And in this reduced, explicit form, the attack surface is clear and the audit scope sharply defined.
This feels like the right first alpha candidate: understandable, bounded, and reversible.
https://github.com/MatthiasPetermann/netbsd-src/tree/feature/jails-v1-ga
Please use the link in this toot to directly access the source repository
https://ioc.exchange/@Radio_Azureus/116103250251003244
#BSD #netBSD #Linux #openBSD #freeBSD #ghostBSD #OpenSource #userland #uitilities #programming #technology #reading
This is a direct link to the project's github page
https://github.com/littlefly365/Netbase
#BSD #netBSD #Linux #openBSD #freeBSD #ghostBSD #OpenSource #userland #uitilities #programming #technology #reading