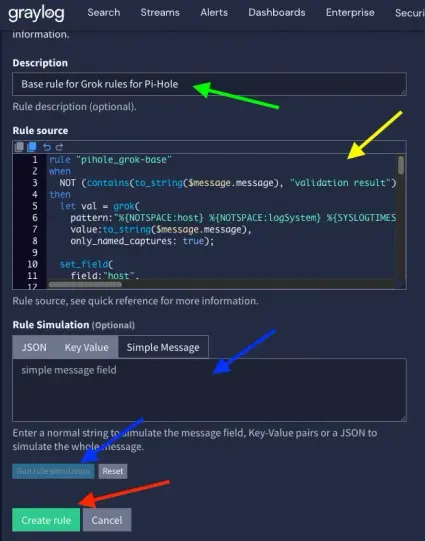
New blog post coming tomorrow (Thursday). After the success and almost viral post about Atomic Red Team, it’s time to use histograms to analyse data and find repetition and silence.
Here’s the Atomic Red Team post:
https://threathunter-chronicles.medium.com/logwatchers-zenit-02-simulating-attacks-with-atomic-red-team-d9071d42eaeb
#cybersecurity #threathunting #threatdetection #loganalysis #incidentresponse #mvpbuzz #blog