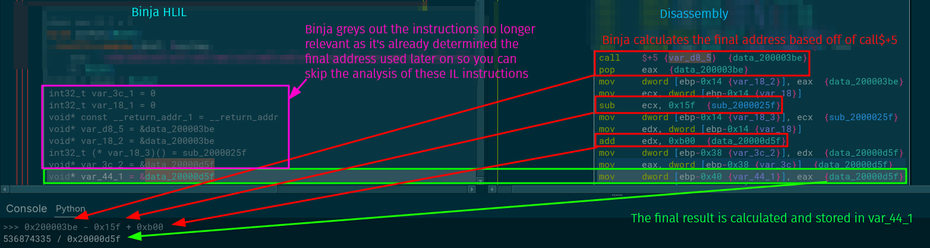
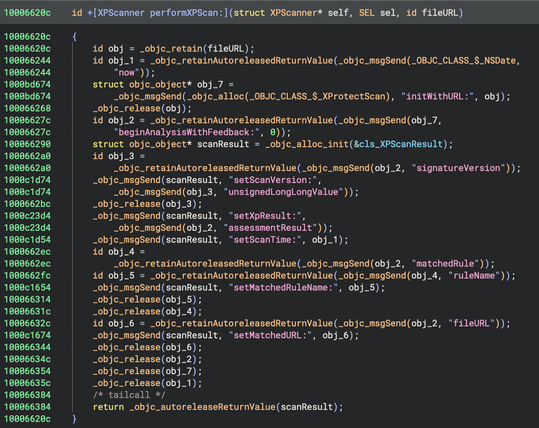
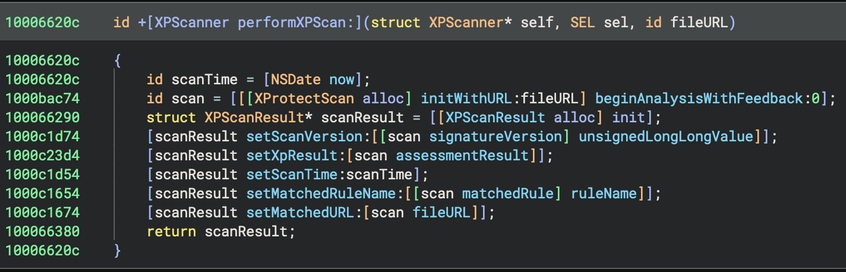
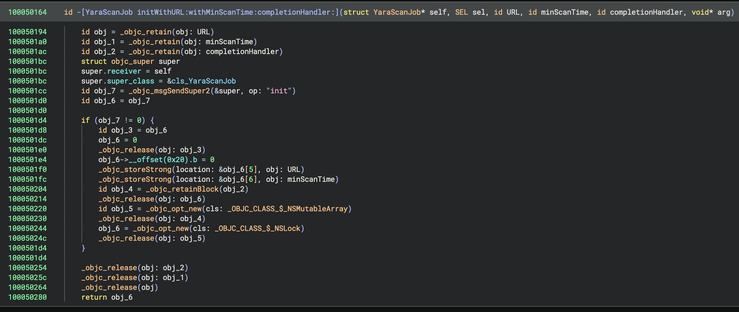
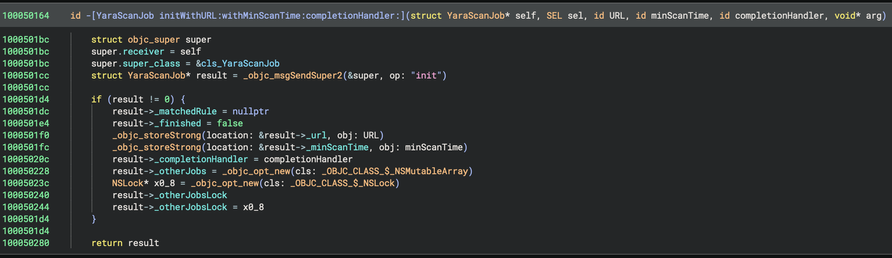
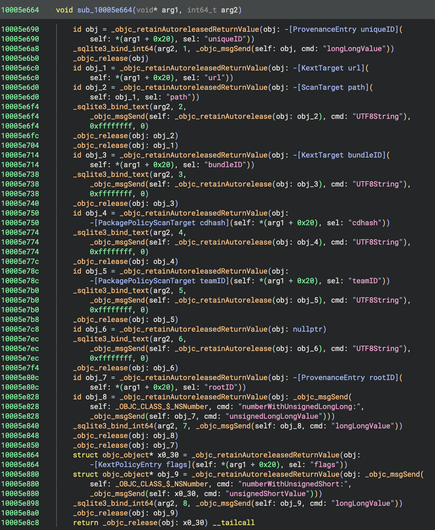
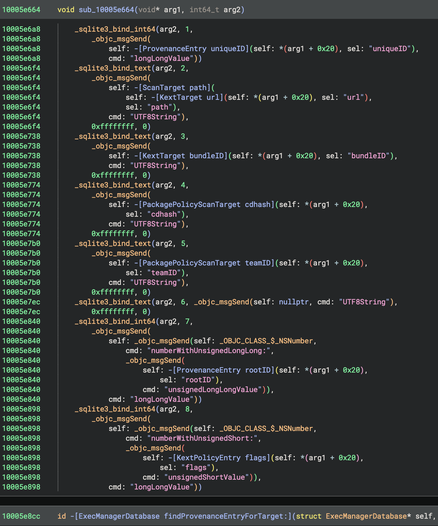
My PR to Binary Ninja to provide a “Pseudo Objective-C” representation of decompiled code was merged and is available in the latest 5.1-dev builds. For best results, use in conjunction with https://github.com/bdash/bn-objc-extras to hide Obj-C memory management noise and propagate more type information.
#binaryninja #reverseengineering #objectivec
https://social.bdash.net.nz/@mrowe/114468984084790336