Heute ist es einfach zu viel...
FunkSec’s FunkLocker Ransomware: mit Hilfe von AI zusammengestoppelt
https://any.run/cybersecurity-blog/funklocker-malware-analysis/
https://www.einnews.com/pr_news/854223893/any-run-exposes-funklocker-ai-generated-ransomware-threatens-global-organizations
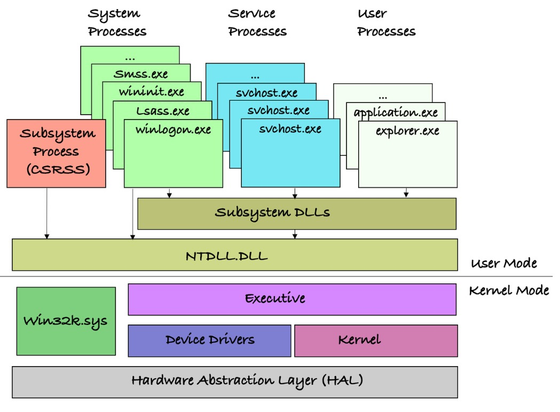
Rootkit-Variante FlipSwitch zielt auf den Linux-Kernel:
https://www.elastic.co/security-labs/flipswitch-linux-rootkit
DNS-Malware Detour Dog verbreitet Strela Stealer mithilfe von DNS-TXT-Einträgen:
https://blogs.infoblox.com/threat-intelligence/detour-dog-dns-malware-powers-strela-stealer-campaigns/
Und für Gockel-Nutzende gibt es auch eine frische Malware-Kampagne: MatrixPDF.
https://www.varonis.com/blog/matrixpdf
Aber das ist heute noch nicht alles!
Gewaltiges Adobe Analytics Datenleck. Wegen eines falsch konfigurierten API -Endpunktes flossen Daten an Dritte. Es beträfe 15 Millionen Nutzende in Nordamerika und Europa. Wie kann ein routinemäßiges Update zu einer solch massiven Datenpanne führen?
https://thedefendopsdiaries.com/adobe-analytics-data-leak-exposes-15-million-users-in-major-2025-breach/
#infosec #Ransomware #FunkLocker #Rootkit #flipswitch #Malware #DetourDog #matrixpdf #Dataleak #BeDiS