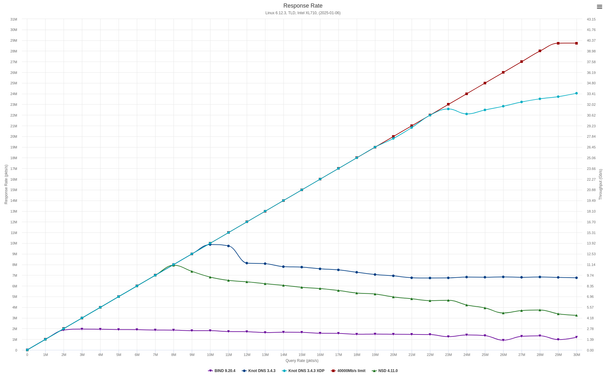
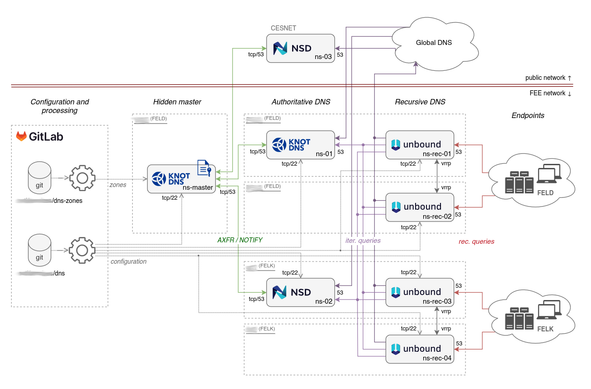
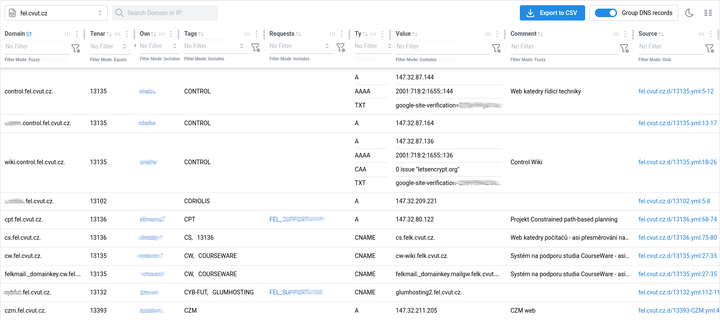
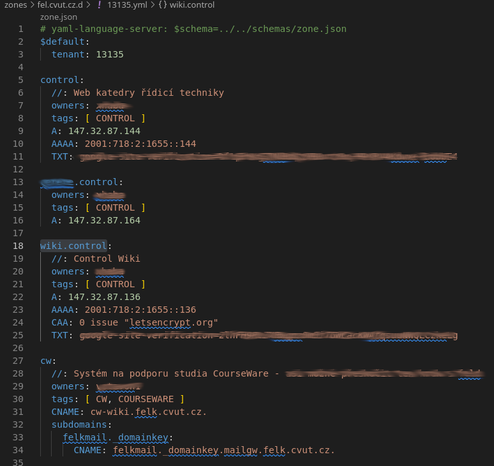
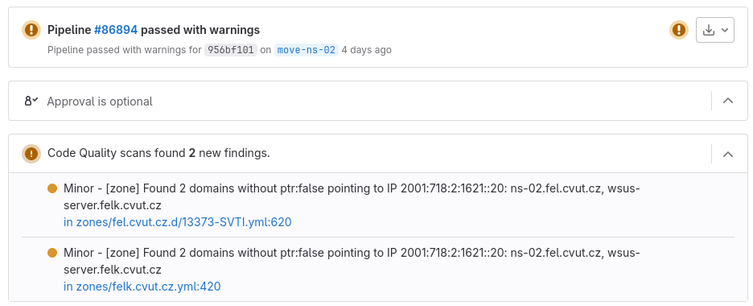
I just wrote a self-hosted #dyndns server using #knotdns, #bottle for the update server (https PUT), and a #python client to detect IP changes. It's running on #AlpineLinux, the code is minimal and it only uses packages that are in the Alpine repos. Full #IPv4 and #IPv6 support, you can use either or both.
Why? It's a cool project, and IMHO every dyndns clients and services I tried were bad, insecure, or both.