https://github.com/michelderooij/PIMfox-for-Entra #Entra
https://github.com/michelderooij/PIMfox-for-Entra #Entra
I'm currently trying to query Entra ID properties if a user.
The commands go like this:Connect-MgGraph -Scopes User.ReadWrite.All
This appeared to work and showed the welcome message.Get-MgUser -Filter "userprincipleName eq 'employeeemail@corpo.com'" | select -ExpandProperty EmployeeOrgData (real intuitive stuff).
This failed with the message:
Get-MgUser: The 'Get-MgUser' command was found in the module 'Microsoft.Graph.Users', but the module could not be loaded due to the following error: [Could not load file or assembly 'Microsoft.Graph.Authentication'... Assembly with same name already loaded.So I did some looking, ran
Get-Module, sure enough Authentication is loaded, tried running Remove-Module but that didn't help whatever, searched it up and apparently the best way to fix this is to just reinstall the module. OK ffs whatever.Uninstall-Module Microsoft.Graph.You cannot Uninstall blah blah blah. Administrator rights are required.OK, close powershell. Reopen as admin user.Run
Start-Process powershell -verb runas to elevate.Get new window, run Uninstall command again.Module not foundheavy exhausted sigh
Open a new powershell window, but version 7 this time,
pwsh instead of powershell.Run Uninstall module, completes fine.
Run Install-Module, completes fine.
Run GetMgUser,
Authentication needed. Please call Connect-MgGraph.Run Connect-MgGraph.
Long pause.
InteractiveBrowserCredential authentication failed:There is no further output after the :The window is now frozen, normally it would open a browser window for login, but it hasn't done that. I cannot close the window, I cannot minimize it, I cannot cancel the command. There is no hidden window on the desktop. I tried to close it with TaskMgr but it failed because it's an admin session.
I'm just so tired and exhausted of interacting with this absolute garbage system, it's all fucking shit, Microsoft produces nothing of any quality any substance it's just endless trash.
#Microsoft #powershell #azure #Entra #msgraph
https://butterword.com/techcrunch-mobility-la-ia-fisica-entra-en-la-maquina-publicitaria/?feed_id=65452&_unique_id=696d49e0be783
Good article by Colin Turner 👌
"Customising Django Microsoft Entra ID Authentication"
https://www.piglets.org/blog/2025/12/24/customising-django-entra-id-authentication/
#oss #foss #python #django #entra #entraid #programming #devops #programmer #developer
A small python script to extract all related domains for a specific Office 365 tenant🕵️♂️
#infosec #cybersecurity #redteam #pentest #osint #azure #entra #cloud #opensource
Ik werk, zoals zovelen van jullie, voor een instelling die, terwijl een ander land zich klaarmaakt voor de grootste landverovering van europees grondgebied ooit, bezig is zijn volledige digitale infrastructuur en data over te dragen aan datzelfde land.
EN NIEMAND BINNEN DE INSTELLING STELT OOK MAAR EEN ENKELE VRAAG HIEROVER.
#azure #entra #office365 #microsoft #DigitaleSoevereiniteit #eu
En dat noemt zich #onderwijs
🚨 New research & tool release: OID-See - Giving Your OAuth Apps the Side-Eye
OAuth risk in Entra isn’t a table problem.
It’s a relationship problem.
After spending far too long staring at consent screens, Graph responses, and metadata that technically tells the truth while still being wildly misleading, I ended up building something I couldn’t find anywhere else:
OID-See - essentially BloodHound for OAuth in Entra.
It maps:
• OAuth apps & service principals
• Delegated scopes and app permissions
• Consent, assignments, and reachability
• Trust signals (and trust illusions)
• Persistence and impersonation paths
…into a graph-backed analysis model that lets you reason about what an app can actually become when chained, not just whether it looks risky in isolation.
Why this exists
I kept running into the same issues:
• “Verified publisher” isn’t always the signal we think it is
• Microsoft-shaped metadata can lull defenders into false trust
• offline_access ≠ impersonation, but does equal persistence
• Apps without assignment requirements are exposed by default
• Spreadsheets hide abuse paths - graphs expose them
So I stopped trying to answer “is this app bad?”
and started asking “what does this enable if it’s abused?”
What OID-See is (and isn’t)
✅ Graph-only by default (no token scraping, no SaaS, no data exfil)
✅ You run it yourself, get a JSON, analyse it locally
✅ Explainable scoring, externalised logic, no magic
❌ Not a CSPM replacement
❌ Not an EDR, SWG, or token replay tool
It’s about clarity, not control theatre.
📖 Blog (deep dive, philosophy, and war stories):
👉 https://cirriustech.co.uk/blog/oidsee/
🧰 Tool & source (v1.0.0):
👉 https://github.com/OID-See/OID-See/tree/v1.0.0
If you’re an Entra admin, cloud security engineer, or anyone who’s ever said
“it’s just a harmless SSO integration” - this one’s for you.
And yes… the name is intentional.
You probably should be giving your OAuth apps the side-eye. 👀
#Entra #AzureAD #OAuth #OIDC #IdentitySecurity #SecurityResearch #AttackSurface #Graph #BloodHound #OIDSee
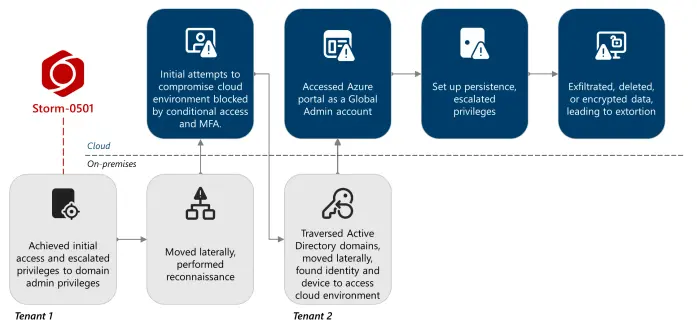
Storm-0501’s evolving techniques lead to cloud-based ransomware - https://www.redpacketsecurity.com/storm-0501-s-evolving-techniques-lead-to-cloud-based-ransomware/
#threatintel
#Storm-0501
#cloud-based ransomware
#hybrid cloud
#Entra ID / Azure AD
#Azure security
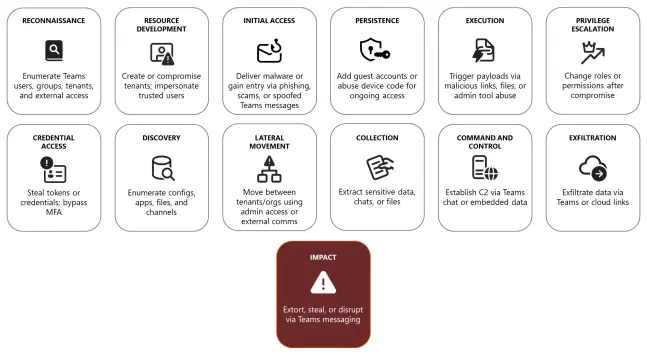
Disrupting threats targeting Microsoft Teams - https://www.redpacketsecurity.com/disrupting-threats-targeting-microsoft-teams/
#threatintel
#Microsoft Teams security
#Threat landscape
#Defender for Endpoint
#Entra ID / identity protection
#Attack surface reduction
Storm-0501’s evolving techniques lead to cloud-based ransomware - https://www.redpacketsecurity.com/storm-0501-s-evolving-techniques-lead-to-cloud-based-ransomware/
#threatintel
#Storm-0501
#cloud-based ransomware
#hybrid cloud
#Entra ID / Azure AD
#Azure security