The story of how I first got into Open Source in the early 1990s is now up here: https://maintaine.rs/bagder
(but yeah, it wasn't actually named "Open Source" until 1998 so before that we just shipped freely available code)
The story of how I first got into Open Source in the early 1990s is now up here: https://maintaine.rs/bagder
(but yeah, it wasn't actually named "Open Source" until 1998 so before that we just shipped freely available code)
More views on #curl vulnerabilities
https://daniel.haxx.se/blog/2025/07/10/more-views-on-curl-vulnerabilities/
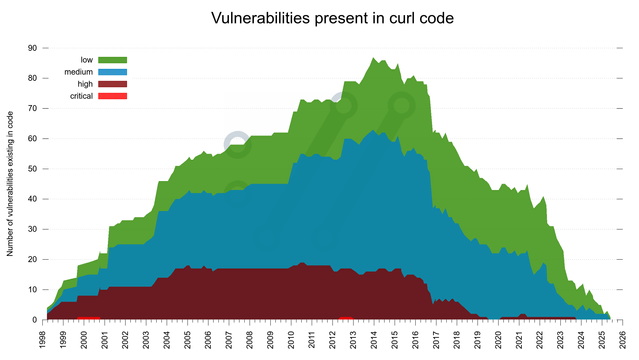
This is an intersection of two of my obsessions: graphs and vulnerability data for the curl project. In order to track and follow every imaginable angle of development, progression and (possible) improvements in the curl project we track and log lots of metadata. In order to educate and inform users about past vulnerabilities, but also … Continue reading more views on curl vulnerabilities →
Whoa: Weston, the reference compositor for #Wayland, supports multiple physical independent mice at the same time! 😀
"New mouse, who dis?"
(See toot later in the thread for how to set this up!)
The Wayback project, a X11 compatibility layer that allows running X11 desktop environments using Wayland, is now hosted by FreeDesktop.org.
https://linuxiac.com/wayback-becomes-part-of-freedesktop-org-ecosystem/
I believe Citrix may have made a mistake in the patching instructions for CitrixBleed2 aka CVE-2025-5777.
They say to do the instructions on the left, but they appear to have missed other session types (e.g. AAA) which have session cookies that can be stolen and replayed with CitrixBleed2. On the right is the CitrixBleed1 instructions.
The net impact is, if you patched but a threat actor already took system memory, they can still reuse prior sessions.
Tell anybody you know at Citrix.