| Website | https://www.zerodayinitiative.com/ |
| Research | https://www.zerodayinitiative.com/blog |
| Pwn2Own | https://www.youtube.com/c/ZeroDayInitiative |
Trend Zero Day Initiative
@thezdi@infosec.exchange
- 2K Followers
- 7 Following
- 1,006 Posts
Trend Zero Day Initiative™ (ZDI) is a program designed to reward security researchers for responsibly disclosing vulnerabilities.
How China Is Building an Army of Hackers. With commentary from ZDI's Dustin Childs and footage from #Pwn2Own Automotive https://youtu.be/8kpnSb4yGR0?si=JxoohyErJkcRXZD5 via @YouTube

How China Is Building an Army of Hackers
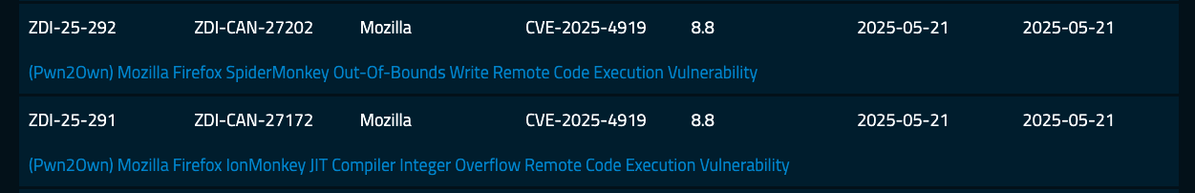
#Pwn2Own Berlin 2025 is complete! In total, we awarded $1,078,750 for 28 unique 0-days. Join Brian Gorenc and Dustin Childs as they recap the highlights (and some lowlights) from this year's event. https://youtu.be/G7McB7L7sIs #P2OBerlin

Wrapping Up Pwn2Own Berlin 2025
This was our first year having an AI category at #Pwn2Own, and we weren't sure what to expect. What we got was some great research across four different frameworks. https://youtube.com/shorts/OY64_WWa8vE #P2OBerlin
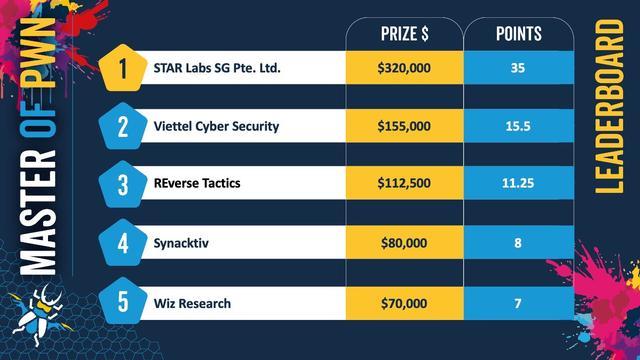
Pwn2Own Berlin 2025 comes to a close. We awarded $1,078,750 for 28 unique 0-days. Congrats to STAR Labs SG for winning Master of Pwn with $320,000. Thanks to @offensive_con for hosting, and thanks to all who participated. Can't wait to see you next year! #Pwn2Own #P2OBerlin
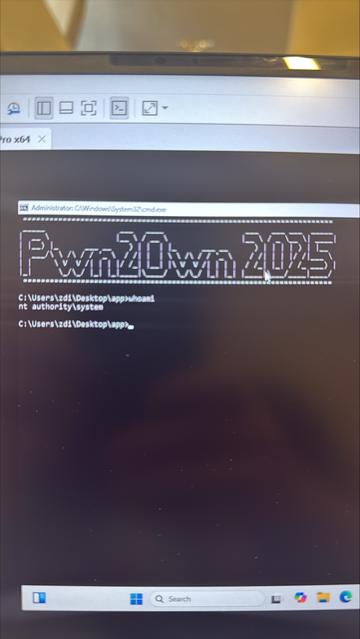
Our final entry for @Pwn2Own Berlin has been confirmed as a win! Miloš Ivanović (https://infosec.exchange/@ynwarcs) used a race condition bug to escalate privileges to SYSTEM on Windows 11. His fourth-round win nets him $15,000 and 3 Master of Pwn points.
Nice! #Pwn2Own newcomer Miloš Ivanović (https://infosec.exchange/@ynwarcs) successfully demonstrated his privilege escalation on #Windows 11. He heads off to the disclossure room to discuss how he did it. #P2OBerlin
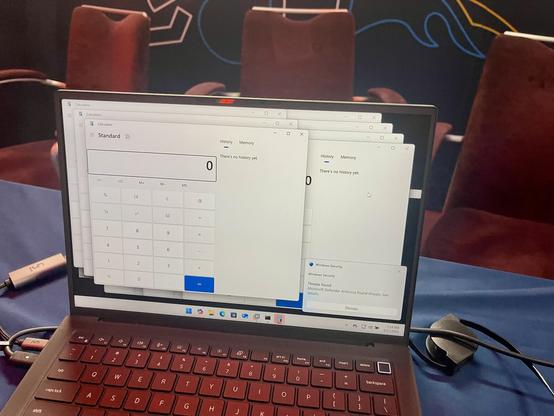
A successful collision! Corentin BAYET from Reverse Tactics used 2 bugs to exploit ESXi, but the Use of Uninitialized Variable bug collided with a prior entry. His integer overflow was unique though, so he still earns $112,500 & 11.5 Master of Pwn points. #Pwn2Own