| Website | https://www.zerodayinitiative.com/ |
| Research | https://www.zerodayinitiative.com/blog |
| Pwn2Own | https://www.youtube.com/c/ZeroDayInitiative |
Trend Zero Day Initiative
@thezdi@infosec.exchange
- 2K Followers
- 7 Following
- 1,021 Posts
Trend Zero Day Initiative™ (ZDI) is a program designed to reward security researchers for responsibly disclosing vulnerabilities.
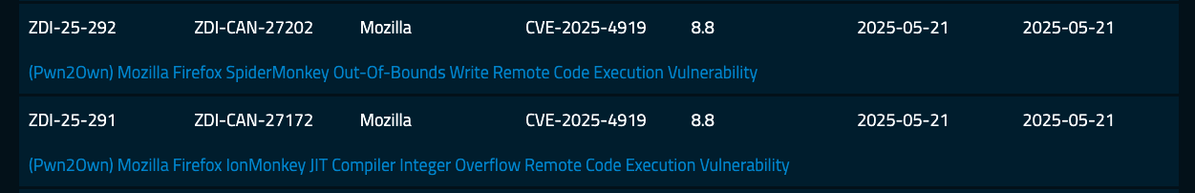
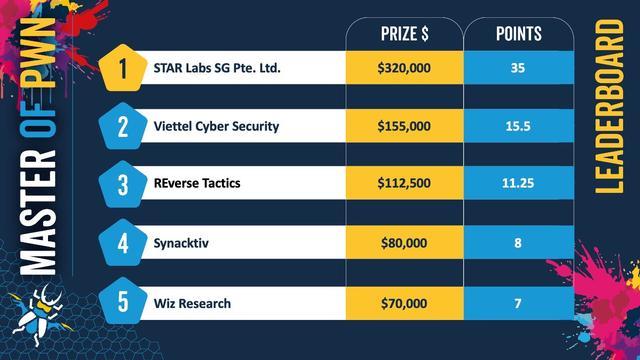
Pwn2Own Berlin 2025 comes to a close. We awarded $1,078,750 for 28 unique 0-days. Congrats to STAR Labs SG for winning Master of Pwn with $320,000. Thanks to @offensive_con for hosting, and thanks to all who participated. Can't wait to see you next year! #Pwn2Own #P2OBerlin
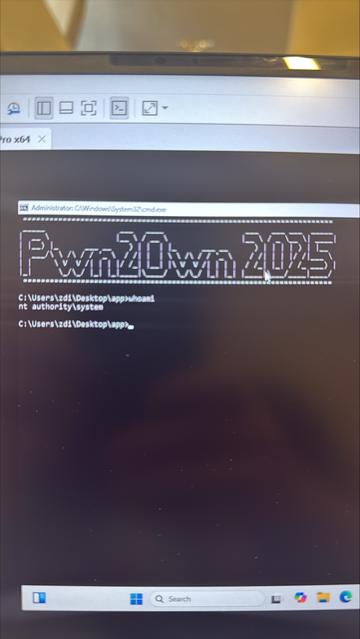
Our final entry for @Pwn2Own Berlin has been confirmed as a win! Miloš Ivanović (https://infosec.exchange/@ynwarcs) used a race condition bug to escalate privileges to SYSTEM on Windows 11. His fourth-round win nets him $15,000 and 3 Master of Pwn points.
Nice! #Pwn2Own newcomer Miloš Ivanović (https://infosec.exchange/@ynwarcs) successfully demonstrated his privilege escalation on #Windows 11. He heads off to the disclossure room to discuss how he did it. #P2OBerlin
A successful collision! Corentin BAYET from Reverse Tactics used 2 bugs to exploit ESXi, but the Use of Uninitialized Variable bug collided with a prior entry. His integer overflow was unique though, so he still earns $112,500 & 11.5 Master of Pwn points. #Pwn2Own
Confirmed!! Dung and Nguyen (@MochiNishimiya) of STARLabs used a TOCTOU race condition to escape the VM and an Improper Validation of Array Index for the Windows privilege escalation. They earn $70,000 and 9 Master of Pwn points. #Pwn2Own
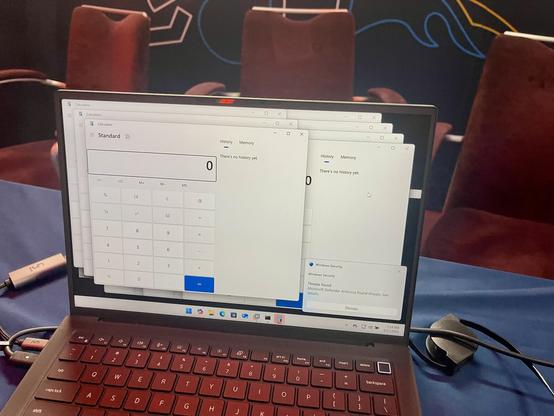
Sweet! Corentin BAYET (@OnlyTheDuck) from @Reverse_Tactics barely needed a second to demonstrate his exploit against VMware ESXi. He heads off to the disclosure room to provide the details of his work. #Pwn2Own #P2OBerlin
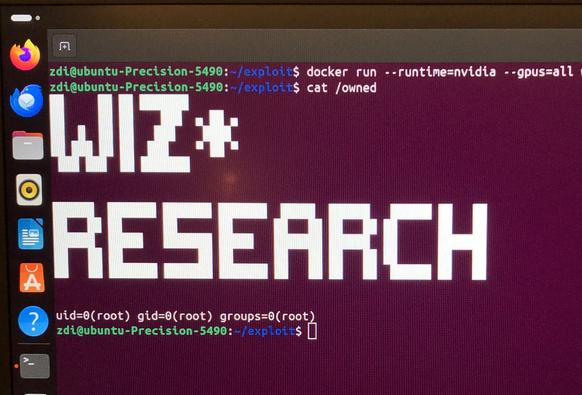
Amazing! Nir Ohfeld and Shir Tamari of Wiz Research used a External Initialization of Trusted Variables bug to exploit the #NVIDIA Container Toolkit. This unique bug earns them $30,000 and 3 Master of Pwn points.