Malware Analysis and Reverse Engineering Enthusiast.
Ricardo Alves
- 18 Followers
- 21 Following
- 50 Posts
Malware Analysis and Reverse Engineering Enthusiast.
New blog post!
🧮 Ints Aren’t Integers and Floats Aren’t Real
Some musings on x86 flags, the CMP instruction, floating point quirks, and why 0.1 + 0.2 might actually break a bridge 🌉
Also: CTF fun, more TPM stuffssess, and a reminder that breaking stuff on purpose is still the best way to learn 🧨
Read here: https://dreaming-of-dragons.blogspot.com/2025/07/ints-arent-integers-and-floats-arent.html
#assembly #ctf #floatingpoint #reversing #linux #cybersecurity #infosec
New blog post up 🕵️♂️
🧅 Playing With Bits: Of Malware Labs, Steganography and Narnia
A peek into hiding data in images, setting up a simple but safe malware lab, and revisiting the OverTheWire Narnia wargame 🧙♂️
Read here: https://dreaming-of-dragons.blogspot.com/2025/06/playing-with-bits-of-malware-labs.html
#malwareanalysis #steganography #ctf #reversing #cybersecurity #linux #hacking
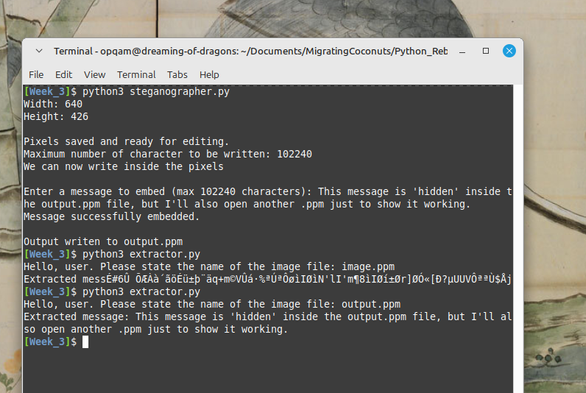
🛠️ Built a couple of small Python tools:
One writes hidden messages into .ppm images using basic steganography.
The other extracts those messages back out.
It’s just a proof of concept—but feel free to explore or reuse if you're curious.
More details coming in my next blog post.
Just wanted to give a quick heads-up.
Happy poking. 🔍🐚
📎 You can grab them here:
https://github.com/OPQAM/MigratingCoconuts/tree/master/Python_Rebuild/Week_3
Playing with the least significant bits of my weekend
🐅 Experimenting with steganography — hiding messages inside simple image and sound files.
I’m building a Python script to embed and extract hidden data, mostly to better understand binary manipulation and file formats. 🕵️♂️
Beats working out at the gym.
So it goes. Part I
🧩 Been poking at eval() and exec() in Python — they're deceptively powerful. One stray input and you're one __import__ away from a shell.
Remote Code Execution (RCE) isn’t just old news — it’s still real, still nasty in the wrong hands.
🌲 Python’s ASTs let you trace what a script really does without running it — but just one layer of obfuscation, and they fall apart.
Small tools, deep cuts. Keep digging.
New Blog Post: Why Won’t You Power Off?
Linux wouldn’t shut down my ThinkPad x260.
❌ It wasn’t heat.
❌ It wasn’t ACPI.
✅ It was the TPM.
🛠️ Troubleshooting recap
⚙️ BIOS tweaks
☕ Real fix that worked
🔗 https://dreaming-of-dragons.blogspot.com/2025/05/why-wont-you-power-off.html
✉️ Ever opened an email and felt like... someone knew?
A friend of mine was on vacation when a client emailed her — and later followed up with:
"I know you opened our email. Can you please reply?"
She hadn’t replied. Just opened the email.
So... how did they know?
You might want to learn more about the spy pixel.
It's cool stuff, I promise:
👉 How a Spy Pixel Crashed Into My Friend's Vacation
🔗 https://dreaming-of-dragons.blogspot.com/2025/04/how-spy-pixel-crashed-into-my-friends.html
🔊 "Securing Your Website (Part 2): Cloudflare Tunnels, WAF Traps, and More Hands-On Security"
So, after setting up Cloudflare Tunnels to bypass my ISP restrictions and adding some basic WAF rules, I kept digging some more into Cloudflare's security features.
📌 Automating tunnel restarts with systemd
📌 Testing custom WAF rules to trap bots.
📌 Experimenting my own rules for loopholes.
👉 https://dreaming-of-dragons.blogspot.com/2025/03/securing-your-website-part-2-cloudflare.html
💻 Today was a doozy.
WORK!
🔍 Next up?
Tomorrow, I’ll be publishing Part 2 of my blog post on WAF rules, Cloudflare tunneling, and setting up a nice home server.
It’s actually pretty easy (mostly after it's done).
Don’t be afraid to make dumb mistakes. You’re definitely not alone. 😅