Shoutout to @h0wdy for this write up! They looked at just how easy it was to pwn telemessage SGNL:
https://www.labs.greynoise.io/grimoire/2025-07-16-checking-the-scope-of-cve-2025-48927/
About Me
I’m Niel, a father at first, working as a Cloud Security Specialist and drive my own business doing penetration tests and Security advisories.
My Interests:
programming
Photography
Mobile Platforms
Security
Travelling
| Sec1 Security | https://sec1.dk |
| Mastodon | @nieldk |
| Signal | NielDK.07 |
Shoutout to @h0wdy for this write up! They looked at just how easy it was to pwn telemessage SGNL:
https://www.labs.greynoise.io/grimoire/2025-07-16-checking-the-scope-of-cve-2025-48927/
I learned something new today—threat actors are using AWS Lambda URLs for C2. Lambda is an ephemeral serverless function service from AWS. They have different URL endpoints in the different AWS regions. One example is: <uniquename>.lambda-url.ap-southeast-1.on[.]aws
Something you may want to hunt for. #cybersecurity #threatintel
From: @VirusBulletin
https://infosec.exchange/@VirusBulletin/114856549151470198
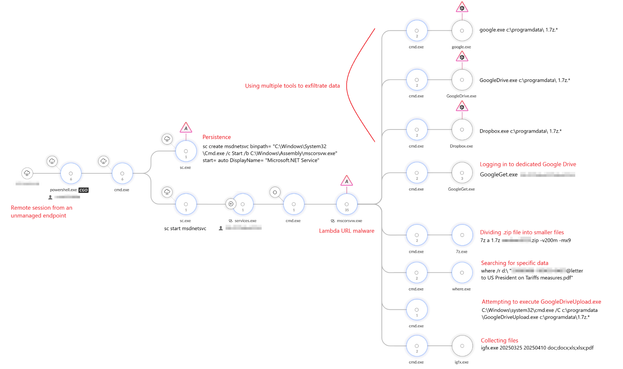
Attached: 1 image Palo Alto Networks' Lior Rochberger looks into a cluster of suspicious activity targeting governmental entities in Southeast Asia. The threat actors behind this campaign use the HazyBeacon Windows backdoor, which leverages AWS Lambda URLs as C2 infrastructure. https://unit42.paloaltonetworks.com/windows-backdoor-for-novel-c2-communication/
Distributed denial of service slop attacks (DDoSSA)
I have this work in progress slide for a talk I might do soon
New, at KrebsOnSecurity.com: Marko Elez, a 25-year-old employee at Elon Musk's Department of Government Efficiency (DOGE), has been granted access to sensitive databases at the U.S. Social Security Administration, the Treasury and Justice departments, and the Department of Homeland Security. So it should fill all Americans with a deep sense of confidence to learn that Mr. Elez over the weekend inadvertently published a private key that allowed anyone to interact directly with more than four dozen large language models (LLMs) developed by Musk's artificial intelligence company xAI.
https://krebsonsecurity.com/2025/07/doge-denizen-marko-elez-leaked-api-key-for-xai/
#encrypt your harddisk
This post-sanction migration from aezadns[.]com to aeza-dns[.]net nameservers continues.
(Aeza was sanctioned due to offering overwhelming support for ransomware operations.)
General reminder:
The domain name putty.org is *NOT* run by the #PuTTY developers. It is run by somebody not associated with us, who uses the domain to interpose advertising for their unrelated commercial products. We do not endorse those products in any way, and we have never given any kind of agreement for PuTTY's name to be used in promoting them.
Please do not perpetuate the claim that putty.org is the PuTTY website. If anyone is linking to it on that basis, please change the link. The PuTTY website is https://www.chiark.greenend.org.uk/~sgtatham/putty/ and it always has been.
You can check this by downloading the source code, which cites that URL in many places (the README, the documentation, some strings in the actual code), or by using the "Visit Web Site" menu options in the official Windows binaries (the ones signed with my personal Authenticode certificate). The true PuTTY website is the one that PuTTY itself says it is.
Many search engines list putty.org above chiark. I don't know if this is due to active SEO on the part of the domain owner, or a heuristic in the rankings. Either way, don't believe them. It's not our site.
