Wietze
@wietze@infosec.exchange
- 100 Followers
- 21 Following
- 42 Posts
Video demo to play with ArgFuscator -- the super cool research and utility from @wietze to obfuscate command-lines to try and evade AV or EDR detection 😎 And to test your rules if any of these crazy looking commands fly under the radar! https://youtu.be/6-Gbv0h7m1I
#HuntingTipOfTheDay: you know how to spot/decode Base64 or XOR in PowerShell… but what about SecureString? This AES-based encryption is native to PowerShell; attackers have been seen to use this for PowerShell obfuscation.
🔍 Hunt for known SecureString decoding commands
More on this technique : https://www.wietzebeukema.nl/blog/powershell-obfuscation-using-securestring
#HuntingTipOfTheDay: Stuck in vi/vim? Open a reverse shell to exit remotely 🙃
Not just a joke - you can make vi/vim run arbitrary commands, not all methods to do so are well detected.
🔍 Hunt for child processes of vi(m), especially those that are rare in your environment.
#HuntingTipOfTheDay: there are numerous open-source projects listing cyber threats. Some of these have directly ingestible indicators, which can be very helpful when threat hunting. How about:
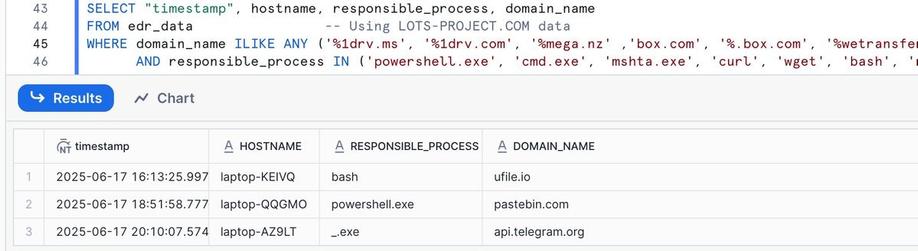
🔵 lots-project.com + LOLBINs
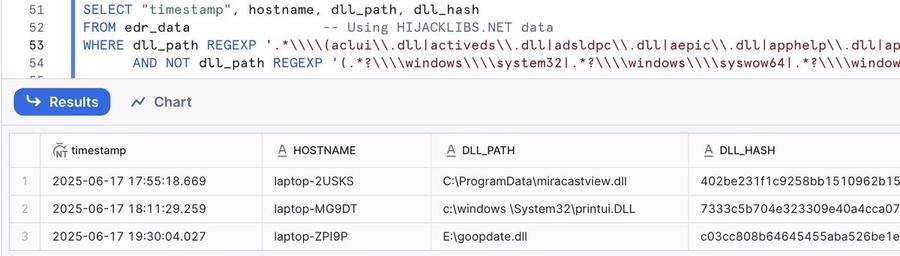
🟠 hijacklibs.net + DLL write events
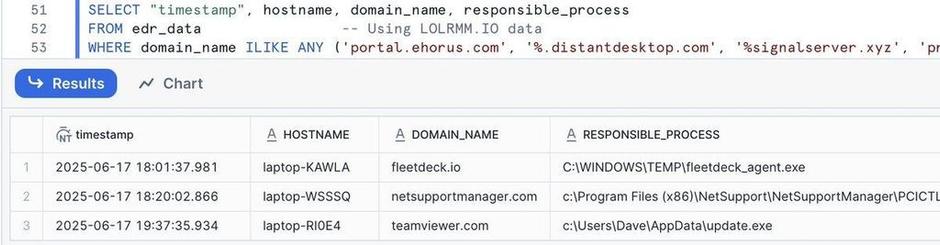
🟢 lolrmm.io + DNS requests
🔵 lots-project.com + LOLBINs
🟠 hijacklibs.net + DLL write events
🟢 lolrmm.io + DNS requests
#HuntingTipOfTheDay: AppleScript via osascript is still a popular way for infostealers to get credentials/escalate access. Although some (poorly coded) updaters use this ""legitimately"", hunting for osascript referencing password dialogs might surface behaviour of interest.
#HuntingTipOfTheDay: USB worms are still a thing - often the initial infection happens when a user clicks a malicious shortcut on a USB device. See if you can correlate executions with .LNK files on remote drives to find possible badness.
#HuntingTipOfTheDay: proxy execution via ComputerDefaults.exe by setting this registry key; as it auto-elevates, it also allows for UAC bypass (!).
🔴 Executing parent is usually explorer.exe, making detection harder
🔍 Hunt for reg changes to this key
👉 https://lolbas-project.github.io/lolbas/Binaries/ComputerDefaults/
🔴 Executing parent is usually explorer.exe, making detection harder
🔍 Hunt for reg changes to this key
👉 https://lolbas-project.github.io/lolbas/Binaries/ComputerDefaults/
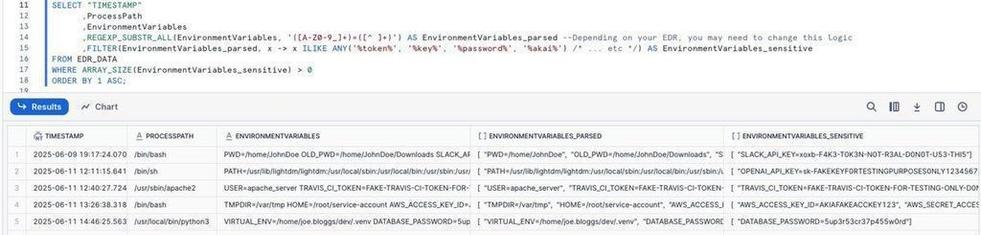
#HuntingTipOfTheDay: Florian is right.
🌩️ Cloud creds often linger in Environment Variables, especially on servers/dev machines
🟠 One compromised endpoint could thus lead to a full cloud breach
🔍 Hunt for exposed tokens - if you can see it, so could an attacker (well, kinda)
https://infosec.exchange/@cyb3rops@bird.makeup/114669259417132788
#HuntingTipOfTheDay: @oddvarmoe of @trustedsec shows how you can run a full C2 implant from Outlook - just setting a few registry keys does the trick.
Any activity concerning these registry keys should be considered suspicious.
Full story here: https://youtu.be/7MDHhavM5GM
#HuntingTipOfTheDay: TCC on macOS can be bypassed by triggering Electron apps' Node.js interface to run arbitrary commands
⚡ By using a Launch Daemon, you can leverage all the app's TCC permissions
🔍 Hunt for processes with ELECTRON_RUN_AS_NODE env var and unusual command lines
Read more: https://afine.com/threat-of-tcc-bypasses-on-macos/