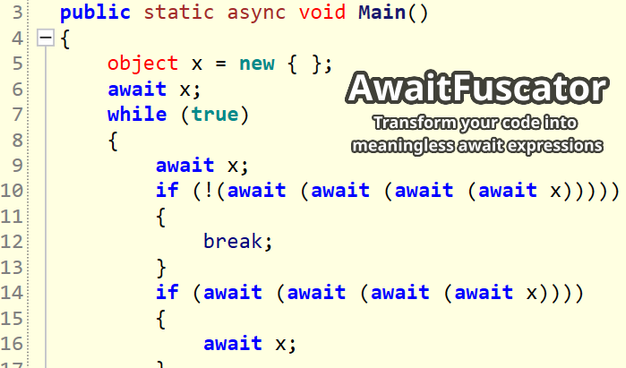
After #flareon11 challenge 7, I got inspired to build tooling for #dotnet Native AOT reverse engineering.
As such, I built a #Ghidra Analyzer that can automatically recover most .NET types, methods and frozen objects (e.g., strings).
👉https://blog.washi.dev/posts/recovering-nativeaot-metadata/