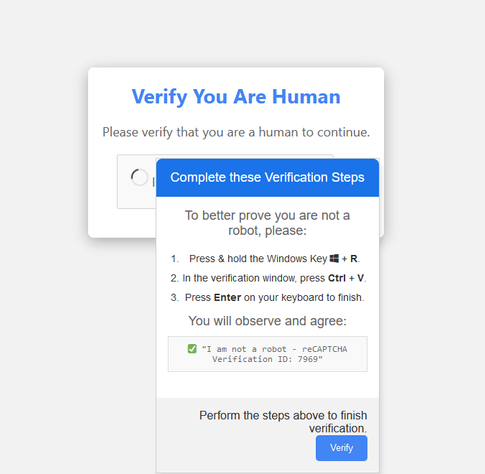
My first introduction to @dgl was finding https://dgl.cx/2023/09/ansi-terminal-security on my own and then being surprised he was a co-worker!
I got to sit down with him and chat about the recent git CVE he discovered and a lot more in our recent podcast episode.
If you don't have time for that, here's 5 minutes on the vulnerabililty specifically, cut from that interview: https://youtu.be/XZHxE3iWPMU



 Eckhofer
Eckhofer