https://www.inside-digital.de/news/sonnensteuer-fuer-pv-anlagen-soll-kommen-alle-besitzer-sollen-zahlen
#solarpunk #klimakatastrophe #lobbyismus #fossillobby
@BlumeEvolution
#Professor of computer stuff; occasionally wires up lecture halls at Hamburg University of Applied Sciences (#HAWHamburg) and reports on commuting adventures by #train between #Oldenburg and #Hamburg.
Reposts random nerd and politics stuff in German or English. Posts are being deleted after 3 months.
| Website | https://lins.me |
| PeerTube | https://tube.lins.me |
So ihr Lieben,
Dobrindt hat genug Leute, die in der Lage wären, die Zahlen korrekt darzustellen. Das ist keine Unfähigkeit, das ist Propaganda.
Daher ist mal wieder Tortendiagrammzeit:
(Gibt es Zahlen über, rechtsextreme Körperverletzungsdelikte und linksextreme Körperverletztungsdelikte? Da würde ich gern mal ein Diagramm dazu machen. Falls du Zahlen dazu hast, her damit. - Falls nicht bitte boosten)
@shortridge While working tech support, I got a call on a Monday. Some VPNs which had been working on Friday were no longer working. After a little digging, we found the negotiation was failing due to a certificate validation failure.
The certificate validation was failing because the system couldn’t check the certificate revocation list (CRL).
The system couldn’t check the CRL because it was too big. The software doing the validation only allocated 512kB to store the CRL, and it was bigger than that. This is from a private certificate authority, though, and 512kB is a *LOT* of revoked certificates. Shouldn’t be possible for this environment to hit within a human lifespan.
Turns out the CRL was nearly a megabyte! What gives? We check the certificate authority, and it’s revoking and reissuing every single certificate it has signed once per second.
The revocations say all the certificates (including the certificate authority’s) are expired. We check the expiration date of the certificate authority, and it’s set to some time in 1910. What? It was around here I started to suspect what had happened.
The certificate authority isn’t valid before some time in 2037. It was waking up every second, seeing the current date was after the expiration date and reissuing everything. But time is linear, so it doesn’t make sense to reissue an expired certificate with an earlier not-valid-before date, so it reissued all the certs with the same dates and went to sleep. One second later, it woke up and did the whole process over again. But why the clearly invalid dates on the CA?
The CA operation log was packed with revocations and reissues, but I eventually found the reissues which changed the validity dates of the CA’s certificate. Sure enough, it reissued itself in 2037 and the expiration date was set to 2037 plus ten years, which fell victim to the 2038 limitation. But it’s not 2037, so why did the system think it was?
The OS running the CA was set to sync with NTP every 120 seconds, and it used a really bad NTP client which blindly set the time to whatever the NTP server gave it. No sanity checking, no drifting. Just get the time, set the time. OS logs showed most of the time, the clock adjustment was a fraction of a second. Then some time on Saturday, there was an adjustment of tens of thousands of seconds forward. The next adjustment was hundreds of thousands of seconds forward. Tens of millions of seconds forward. Eventually it hit billions of seconds backwards, taking the system clock back to 1904 or so. The NTP server was racing forward through the 32-bit timestamp space.
At some point, the NTP server handed out a date in 2037 which was after the CA’s expiration. It reissued itself as I described above, and a date math bug resulted in a cert which expired before it was valid. So now we have an explanation for the CRL being so huge. On to the NTP server!
Turns out they had an NTP “appliance” with a radio clock (i.e, a CDMA radio, GPS receiver, etc.). Whoever built it had done so in a really questionable way. It seems it had a faulty internal clock which was very fast. If it lost upstream time for a while, then reacquired it after the internal clock had accumulated a whole extra second, the server didn’t let itself step backwards or extend the duration of a second. The math it used to correct its internal clock somehow resulted in dramatically shortening the duration of a second until it wrapped in 2038 and eventually ended up at the correct time.
Ultimately found three issues:
• An OS with an overly-simplistic NTP client
• A certificate authority with a bad date math system
• An NTP server with design issues and bad hardware
Edit: The popularity of this story has me thinking about it some more.
The 2038 problem happens because when the first bit of a 32-bit value is 1 and you use it as a signed integer, it’s interpreted as a negative number in 2’s complement representation. But C has no protection from treating the same value as signed in some contexts and unsigned in others. If you start with a signed 32-bit integer with the value -1, it is represented in memory as 0xFFFFFFFF. If you then use it as an unsigned integer, it becomes the value 4,294,967,296.
I bet the NTP box subtracted the internal clock’s seconds from the radio clock’s seconds as signed integers (getting -1 seconds), then treated it as an unsigned integer when figuring out how to adjust the tick rate. It suddenly thought the clock was four billion seconds behind, so it really has to sprint forward to catch up!
In my experience, the most baffling behavior is almost always caused by very small mistakes. This small mistake would explain the behavior.
Generative KI versaut mir das @ct_Magazin
Seit einiger Zeit findet man in c't weniger Nerd-Illustrationen und auch seltener die traditionell albern gestellten Aufmacherfotos mit Redakteuren statt Fotomodels.
Stattdessen heißt es nun "Bild: KI, Collage c't". Die KI-Bilder sind... okay. Hinnehmbar. Gut genug. Meh. Aber mehr auch nicht.
Da abonniert man seit Jahrzehnten ein Magazin, weil es Inhalte und Haltung über bloßes Füllmaterial stellt und dabei seine Autoren bekanntermaßen vernünftig behandelt. Und nun signalisiert der Verlag dem Leser, dass Gebrauchs-Illustration und -Fotografie für die Redaktion kein Geld mehr wert sind, denn die generative KI macht es ja preiswerter. Somit weiß ich: Für die Redaktion sind Aufmacherbilder nur Füllmaterial, wo es sich nicht lohnt, jemand für sein (foto)grafisches Handwerk zu beauftragen.
Wenn Inhalte also nur Füllmaterial sind, muss ich nun das gleiche langfristig für Texte in der c't erwarten. Denn parallel "experimentiert" man schon mit KI-generierten Texten in der Rubrik "Techstage", sorry, "bestenlisten" im Heise Newsticker.
Interne Unterlagen: Die BReg stellt sich im EU-Ministerrat gegen die geplante Anti-Korruptionsrichtlinie - zusammen mit Österreich und Ungarn
That story about an AI startup collapsing after it turned out to be 700 Indian developers in a Trenchcoat? It was a made up story by a crypto guy that became clickbait, published unchecked by tech media everywhere. Read the real story behind Builder.ai here: https://blog.pragmaticengineer.com/builder-ai-did-not-fake-ai/
1/3
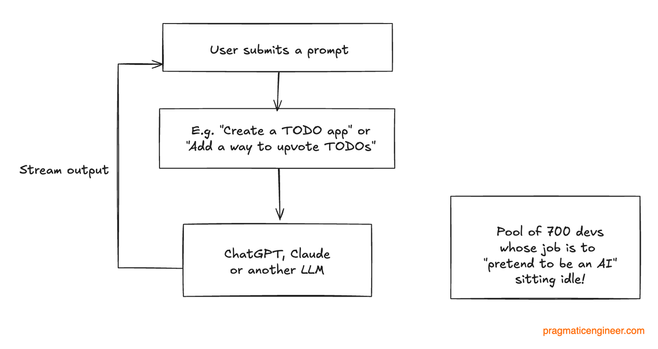
The claim that the AI startup “faked AI” with hundreds of engineers went viral – and I also fell for it, initially. The reality is much more sobering: Builder.ai built a code generator on top of Claude and other LLMs; it did not build a so-called “Mechanical Turk.”