Organisers of the annual Virus Bulletin conference.
Virus Bulletin
- 2.5K Followers
- 57 Following
- 1.9K Posts
Organisers of the annual Virus Bulletin conference.
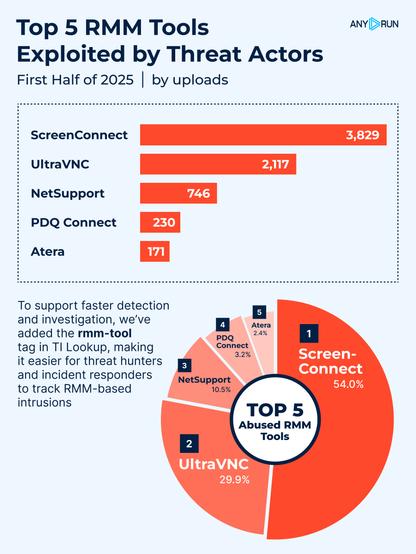
🚨 Top 5 Remote Access Tools Exploited by Threat Actors in the First Half of 2025.
⚠️ While legitimate and widely used by IT teams, Remote Monitoring and Management tools are increasingly used by threat actors to establish persistence, bypass defenses, and exfiltrate data.
In the first half of 2025, #ANYRUN observed a significant number of #malware samples leveraging known RMM software for #malicious access. Here are the 5 most frequently abused tools, along with analysis examples:
1️⃣ ScreenConnect – 3,829 sandbox sessions
https://app.any.run/tasks/3aa42d2e-8b91-4b8c-8bbb-e2b733194294/?utm_source=mastodon&utm_medium=post&utm_campaign=top_rmm&utm_term=020725&utm_content=linktoservice
2️⃣ UltraVNC – 2,117 sandbox sessions
https://app.any.run/tasks/1b7234a0-ab11-4301-a5e7-9e157acfad95/?utm_source=mastodon&utm_medium=post&utm_campaign=top_rmm&utm_term=020725&utm_content=linktoservice
3️⃣ NetSupport – 746 sandbox sessions
https://app.any.run/tasks/6740b646-2763-4969-9afe-31104dff0d81/?utm_source=mastodon&utm_medium=post&utm_campaign=top_rmm&utm_term=020725&utm_content=linktoservice
4️⃣ PDQ Connect – 230 sandbox sessions
https://app.any.run/tasks/05948d1c-3128-4daa-97e5-60dd9991c115/?utm_source=mastodon&utm_medium=post&utm_campaign=top_rmm&utm_term=020725&utm_content=linktoservice
5️⃣ Atera – 171 sandbox sessions
https://app.any.run/tasks/61e01084-e442-4bb7-a725-1667128573ce/?utm_source=mastodon&utm_medium=post&utm_campaign=top_rmm&utm_term=020725&utm_content=linktoservice
👨💻 To support faster detection and investigation, we’ve added the rmm-tool tag in TI Lookup, making it easier for threat hunters and incident responders to track RMM-based intrusions.
🔍 Explore recent RMM abuse cases in the last 180 days:
https://intelligence.any.run/analysis/lookup?utm_source=mastodon&utm_medium=post&utm_campaign=top_rmm&utm_content=linktoti&utm_term=020725#%7B%2522query%2522:%2522threatName:%255C%2522rmm-tool%255C%2522%2522,%2522dateRange%2522:180%7D%20
Analyze latest malware and #phishing threats with #ANYRUN 🚀 #ExploreWithANYRUN
Planning your Berlin adventure? ✨
We’ve put together a handy guide to help you make the most of your time in this amazing city, from travel information and public transport to local restaurants and must-see sights.
Come for VB2025, stay for Berlin!
Check out our Visiting Berlin page and start planning now 👉 https://tinyurl.com/4hvn7bcs