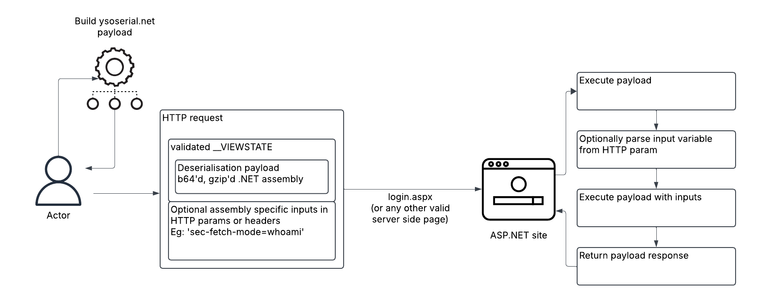
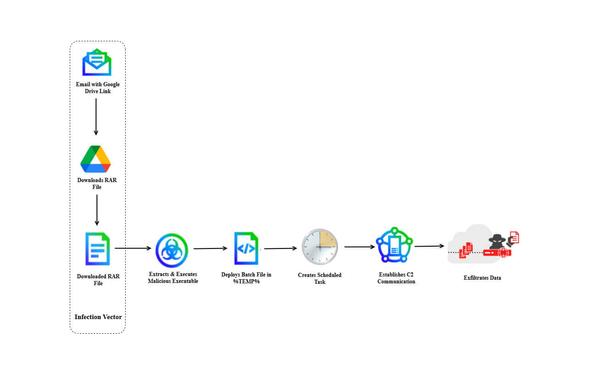
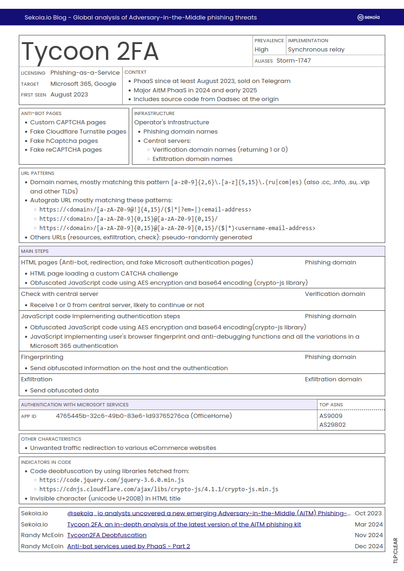
How does Russia’s Sandworm unit exploit pirated software to target Ukraine?
Join Arda Buyukkaya from EclecticIQ at VB2025 in Berlin to uncover how cyber operations can turn everyday behaviour into large-scale threats.
📅 Sept 25 | 09:30–10:00 | Green Room
Find out more about this talk 👉 https://tinyurl.com/e9anehex