| Website | http://www.johndgeek.com |
| Location | Santa Clarita |
Johndgeek 🌎
- 19 Followers
- 10 Following
- 152 Posts
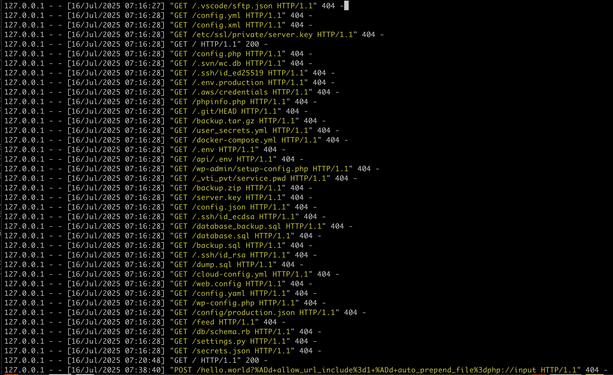
Attackers exploit a blind spot by hiding malware inside DNS records. This technique transforms the Internet DNS into an unconventional file storage system and distributes malware using dns records. Be careful and safe out there 😱 Almost nobody filters DNS. Another security nightmare.
Read more: Malware in DNS
https://dti.domaintools.com/malware-in-dns/
An important message for each of you. Please don't skip. It's very short. And please boost to get the word out. Everyone needs to know this...

one day you'll realize
General reminder:
The domain name putty.org is *NOT* run by the #PuTTY developers. It is run by somebody not associated with us, who uses the domain to interpose advertising for their unrelated commercial products. We do not endorse those products in any way, and we have never given any kind of agreement for PuTTY's name to be used in promoting them.
Please do not perpetuate the claim that putty.org is the PuTTY website. If anyone is linking to it on that basis, please change the link. The PuTTY website is https://www.chiark.greenend.org.uk/~sgtatham/putty/ and it always has been.
You can check this by downloading the source code, which cites that URL in many places (the README, the documentation, some strings in the actual code), or by using the "Visit Web Site" menu options in the official Windows binaries (the ones signed with my personal Authenticode certificate). The true PuTTY website is the one that PuTTY itself says it is.
Many search engines list putty.org above chiark. I don't know if this is due to active SEO on the part of the domain owner, or a heuristic in the rankings. Either way, don't believe them. It's not our site.
Perusing a paper paper for once I saw this advert for WhatsApp.
No I can believe the content of your message can not be read, but by using it, your address book is theirs, your messages sent/received are logged and you will be tracked wherever you are - and whatever you are buying.
That’s what they really want.
Go #Signal - it makes sense
Suspected Scattered Spider domains target everyone from manufacturers to Chipotle
Plus: Qantas makes contact with 'potential cyber criminal' While the aviation industry has borne the brunt of Scattered Spider's latest round of social engineering attacks, the criminals aim to catch manufacturing and medical tech companies — and even Chipotle Mexican Grill — in tjeor web, as…
#theregister #IT
https://go.theregister.com/feed/www.theregister.com/2025/07/08/suspected_scattered_spider_domains_target/
The open source Zapier alternative. Build workflow automation without spending time and money.