⚠️ Change your Steam Password ⚠️
89,000,000 usernames, passwords, and 2-step verification codes have been leaked.
After changing your password, you may wish to reset your 2-step code too.
⚠️ Change your Steam Password ⚠️
89,000,000 usernames, passwords, and 2-step verification codes have been leaked.
After changing your password, you may wish to reset your 2-step code too.
If you do not use a password manager, now is a good time to consider using one. Here are two (2) that are outside Us Jurisdiction.
Heylogin, located in Germany, Europe https://www.heylogin.com
Note: This password manager is tied to your hardware.
pCloud, located in Switzerland / Bulgaria, Europe https://www.pcloud.com/pass.html
Note: Use a VPN when first signing up to ensure your data is saved on their Europe Servers. You can see a copy of the documentation here: https://docs.pcloud.com
I believe in keeping it easy and simple.
A person is smart, but people are dumb and do dumb things. That includes losing or breaking their devices, not making regular backups, and needing to sync over multiple devices.
There is wisdom to what you say, but the cloud is easier and safe for most people.
@Linux for offline password managers KeePass and its variants are great.
@Linux Please, for God's sake: never, ever consider any cloud-based password manager!
Use a local FOSS like KeePassXC with optional Syncthing/NextCloud/... share.
@LawChan @anokasion@hidamari.apartments @gamingonlinux
Sorry, I don't see anything.
If anything was leaked -- anything -- I would advise people to still change everything. If you want to take the risk, that's your call, but I see no harm in being cautious and changing everything as a precaution.
Even if this were someone's idea of a joke and turned out to be a false flag, I would still suggest people review their security.
If anything was leaked -- anything -- I would advise people to still change everything. If you want to take the risk, that's your call, but I see no harm in being cautious and changing everything as a precaution.
Even if this were someone's idea of a joke and turned out to be a false flag, I would still suggest people review their security.
If anything was leaked -- anything -- I would advise people to still change everything. If you want to take the risk, that's your call, but I see no harm in being cautious and changing everything as a precaution.
Even if this were someone's idea of a joke and turned out to be a false flag, I would still suggest people review their security.
It may be total BS, but I would still side with caution. There is no harm in being cautious and changing your password.
@Linux @fristi https://www.varonis.com/blog/data-breach-response-times and let's not forget that companies do take their time on announcing breaches...
I've posted a notice like this, and people came for me just for this still not being confirmed... As if it's a bad thing to be cautious about our own security.
Called nothing -- It was confirmed by Steam. https://steamcommunity.com/games/593110/announcements/detail/533224478739530146
@lancercryptid @koimoa @fristi @kura
And I would STILL say, change your password. -- WHY?
If you obtain enough expired codecs, you can estipulate (learn the algorithm) and create valid ones. - It is why you're always told by everyone, do not share your codes (including your old ones).
Lmao - If that is true, you should rethink your security.
That is easy -- Disable it and re-enable it. You'll have the option to generate new recovery codes.
@Linux Valve denies it, and said they don't use twilio (the service that was said to have been involved in the leak).
Moreover, the guy who put out the news has considerably downplayed it in the last few hours. It is possible that there was never any leak.
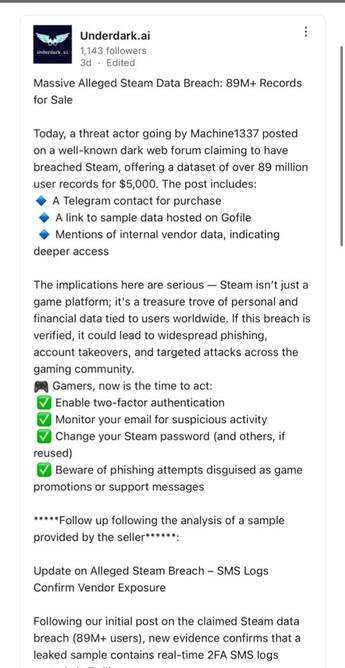
It's been debunked, valve confirmed they don't even use the company that is said to be hacked (a SMS 2FA company) and the source of it all is an AI company's LinkedIn post that itself looks AI made itself I mean, $5000 for 89 MILLION steam accounts? Come on. Just have Steam Guard and you're good. [contains quote post or other embedded content]
Folks, there is 0 evidence that Steam passwords have been breached. Unless and until credible evidence occurs, please do NOT urge people to change their login credentials and please do NOT boost other people's toots doing the same. Creating unjustified anxiety about a non event does a disservice to us all. Please boost for visibility.
@Linux Looks like it's probably just 2FA info -- specifically SMS 2FA numbers -- that got leaked probably. If anyone is using SMS 2FA, they definitely should do something about it.
I won't disagree that changing passwords just to be on the safe side is a good idea though. I disagree with those who so adamantly insist that even though there is evidence of a breach of some kind we should just ignore it just because it's not immediately showing signs of including passwords.
It is not incorrect -- It was confirmed by Steam.
https://steamcommunity.com/games/593110/announcements/detail/533224478739530146
Thanks for the heads up!
Changing my password was made extremely difficult by the way. I use steamguard-cli and ente Auth for 2FA but steam insisted on sending me a code to the app. I had to jump through many hoops to end up at email verification again.
The 2FA had to be fully removed before I could change my pw 😅
I would STILL recommend everyone change their passwords and reset their 2-step codes. -- Why?
If you obtain enough expired codecs, you can estipulate (learn the algorithm) and create valid ones.
That said, thanks for providing a creditable source, confirming the leak.