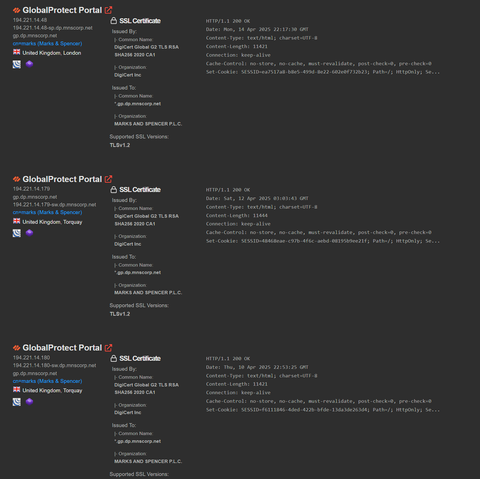
So from looking through their external services, it looks like M&S started containment between Sunday 20th-Tuesday 22nd of April.
They had inbound network activity from IPs associated with crimeware groups, but difficult to know which one due to shared infrastructure.
The Sunday Times today back up my toot about VPN access to M&S being shut down, saying a source at the company says remote access has been “scaled back”: https://www.thetimes.com/business-money/companies/article/marks-and-spencer-shuts-out-wfh-staff-after-cyberattack-q2wwcjzl3
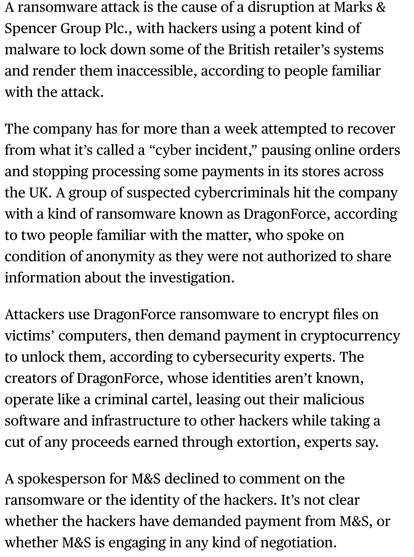
Additionally, the print version of The Telegraph says it is ransomware, citing somebody involved in containment. They say they believe they have locked the threat actor out of the network now and are working on restoration.
Marks and Spencer cyber incident = ransomware.
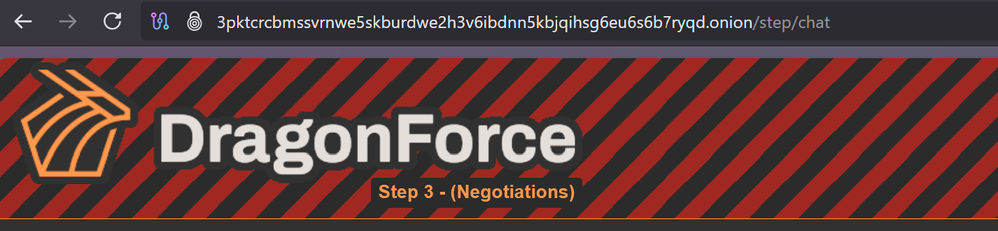
It's DragonForce ransomware cartel, they have encrypted their VMware ESXi clusters. Lines up with network traffic I saw.

Marks & Spencer breach linked to Scattered Spider ransomware attack
Ongoing outages at British retail giant Marks & Spencer are caused by a ransomware attack believed to be conducted by a hacking collective known as "Scattered Spider" BleepingComputer has learned from multiple sources.


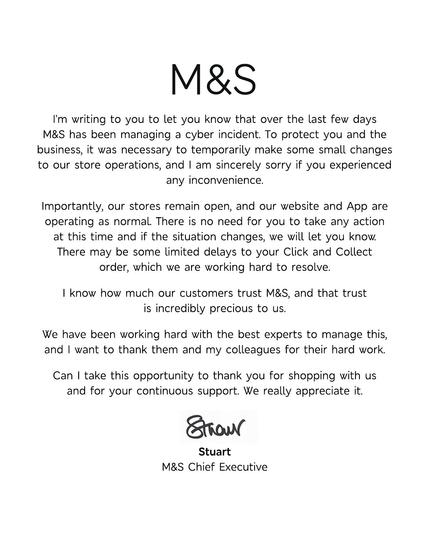
For the record, I think M&S external response so far has been pretty good. They probably should say ransomware themselves publicly, as it's their chance to control the narrative.
I dunno how that level of incident detail got out to media but I'm going to guess intelligence sharing, those circles are basically megaphones. The CISA model with Boeing for CitrixBleed worked better where CISA released findings, made it technical, boring and actionable.
Some M&S stores are apparently having stock problems. I popped around to my local M&S yesterday and asked - they said there's no forecasting system, so they are getting random goods delivery rather than stock refills.
randomized delivery queues, must feel like 1970ies in the gdr, where you never knew if there would be bread or plates for purchase after you waited 3h in the queue in front of the bakery.
Through the fire and flames!





 🇺🇦
🇺🇦