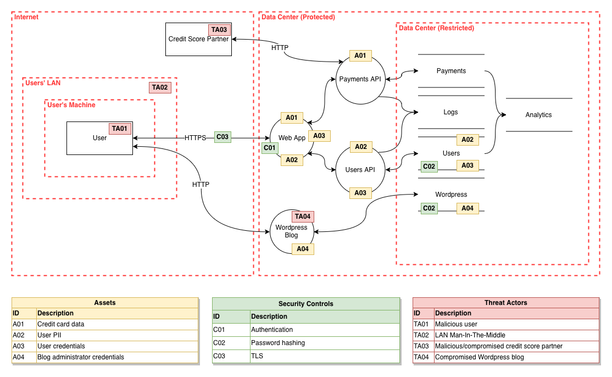
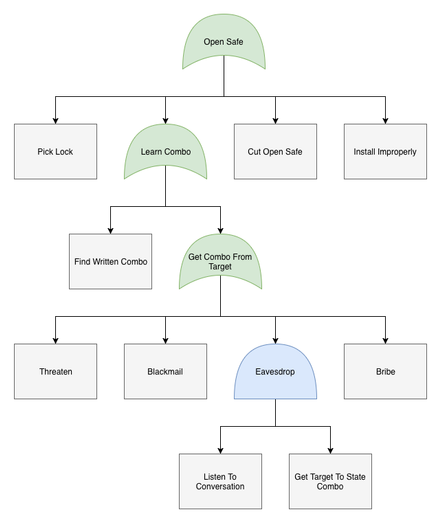
Threat modeling: the future of cybersecurity or another buzzword⎥Derek Fisher
This Youtube interview was with Derek Fisher. Derek is a speaker on various cybersecurity topics, and author of “The Application Security Handbook.”. Derek probes the value of threat modeling in securing apps.
Some takeaways are:
* Difficulties encountered by large enterprises
* How automation helps
* How practical experience and a technical background trumps certifications