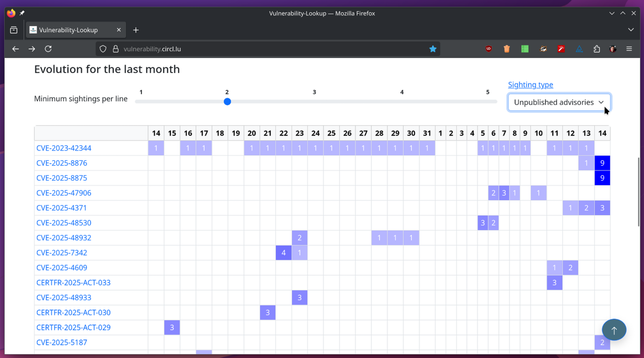
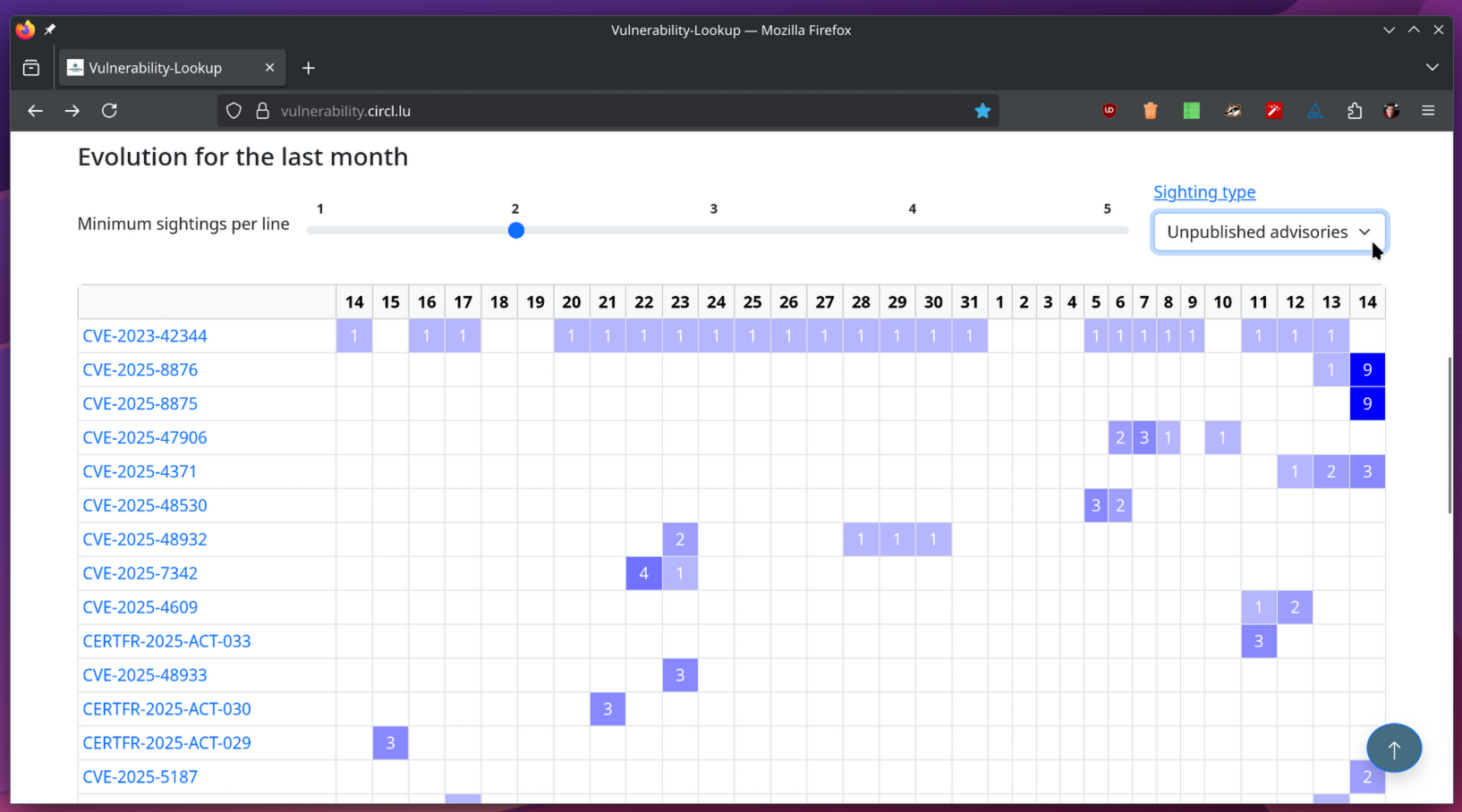
BCP-04 Draft Preparation - Work-group session 25/08/2025 - Luxembourg
- 128 bytes including the prefix recommendation.
- ID format (7-bit character sets versus UTF).
- Assignment and allocation for same vulnerabilities.
#gcve #cve #opensource #cybersecurity
Thanks to for the feedback
GCVE BCP-04 drafting - Recommendations and best practices for ID allocation
BCP-04 Draft Preparation - Work-group session 25/08/2025 - Luxembourg Following discussions in a standard work-group with the GCVE board regarding the recommended size of GCVE identifiers, it was agreed that no strict size limit will be enforced (similar to the flexibility of URIs). However, a recommendation is provided. The recommendation is to use identifiers of up to 128 bytes including the prefix. Another discussion point in the work-group concerned the use of non–7-bit character sets. Som...