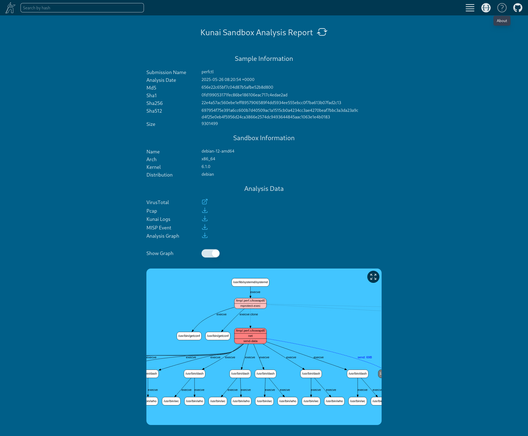
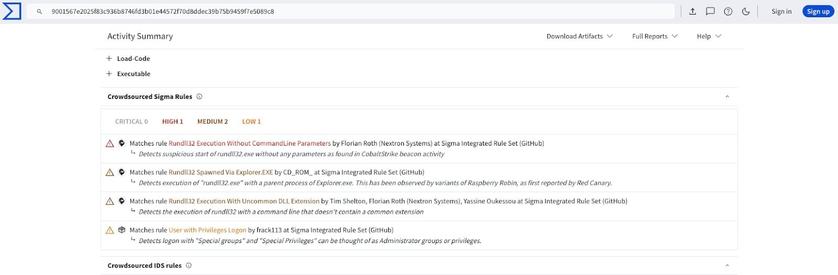
🎉 Just dropped a new Kunai release! 🎉
We've been working hard on some exciting new features and performance boosts that we can't wait for you to try out! Here's what's new:
New Features:
🔍 Track io_uring operations with new io_uring_sqe events!
📝 Get more context with parent command line information for execve and execve_script events.
🔎 Get information about matching filtering rules in final events.
🧪 Test your filters with ease using the new test command.
Improvements:
⚡ Experience performance boosts thanks to changes in the event matching engine and code refactoring.
Ready to dive in? Check out the full release notes here: https://github.com/kunai-project/kunai/releases/tag/v0.6.0
Don't hesitate to give Kunai a try and share your feedback! Let's make Kunai even better together!
#Linux #ThreatHunting #ThreatDetection #DFIR #DetectionEngineering #OpenSource