Microsoft Teams tactics, malware connect Black Basta, Cactus ransomware
New research has uncovered further links between the Black Basta and Cactus ransomware gangs, with members of both groups utilizing the same social engineering attacks and the BackConnect proxy malware for post-exploitation access to corporate networks.
Happy Monday everyone!
Today's #readoftheday is brought to you by Trend Micro and they share their findings related to #BlackBasta and #CactusRansomware adding a piece of malware known as #BackConnect to their toolbox.
The report states "The BackConnect malware is a tool that cybercriminals use to establish and maintain persistent control over compromised systems. Once infiltrated, it grants attackers a wide range of remote control capabilities, allowing them to execute commands on the infected machine. This enables them to steal sensitive data, such as login credentials, financial information, and personal files."
Behaviors (MITRE ATT&CK):
Initial Access - TA0001:
Phishing: Spearphishing Voice - T1566.004 - The attackers conducted an email bombing campaign then contacted the victim posing as "IT Support" or "HelpDesk".
Command and Control - TA0011:
Remote Access Software - T1219 -
The attackers used QuickAssist to access the victim's environment once they were successfully social engineered.
Lateral Movement - TA0008:
Remote Services: SMB/ Windows Admin Shares - T1021.002 -
Remote Services: Windows Remote Management - T1021.006
The attackers leveraged both SMB, shared folders, and WinRM for lateral movement.
Go check out the rest of the technical details! Enjoy and Happy Hunting!
Black Basta and Cactus Ransomware Groups Add BackConnect Malware to Their Arsenal
https://www.trendmicro.com/en_us/research/25/b/black-basta-cactus-ransomware-backconnect.html?&web_view=true
Intel 471 Cyborg Security, Now Part of Intel 471 #ThreatIntel #ThreatHunting #ThreatDetection #HappyHunting
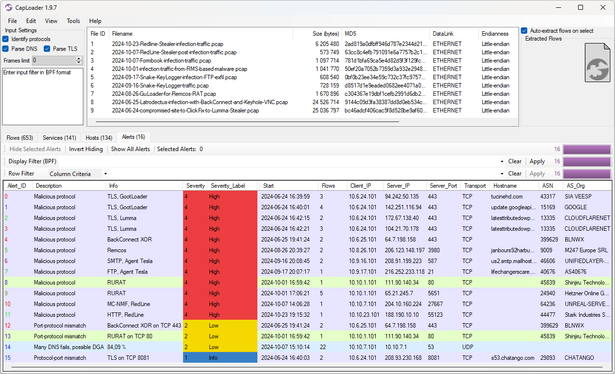
CapLoader wasn’t designed as an alternative to a traditional NIDS, but the Alerts tab often gives a VERY good overview of the malicious traffic. Here’s a screenshot of CapLoader’s alerts for some recent PCAP files from malware-traffic-analysis.net.
#Lumma #GootLoader #AgentTesla #RURAT #Remcos #RedLine #BackConnect
https://netresec.com/?b=23B6bcd
CapLoader 1.9.6 Released
CapLoader now detects even more malicious protocols and includes several new features such as JA4 fingerprints, API support for sharing IOCs to ThreatFox and OSINT lookups of malware families on Malpedia. The new CapLoader 1.9.6 release also comes with several improvements of the user interface, for[...]
Quick #malware analysis: #ICEDID variant with #BACKCONNECT, #ANUBIS #VNC, #COBALTSTRIKE & #SCREENCONNECT pcap from 2023-10-18
Thanks to
@malware_traffic
for sharing this #pcap!
More details:
https://blog.securityonion.net/2023/11/quick-malware-analysis-icedid-variant.html
Attacker launches #BackConnect C2 on #IcedID infected machine and starts a reverse VNC session. The VNC session is used to download #CobaltStrike binary http64.exe from 85.209.11.48 and save it as “http.exe”. Cobalt Strike beacon is then executed from the command line.
For more details and the original #pcap file, see @malware_traffic’s toot here:
https://infosec.exchange/@malware_traffic/111267554603030001
Brad (@malware_traffic@infosec.exchange)
Attached: 4 images From a post I wrote for my employer at https://www.linkedin.com/posts/unit42_icedid-backconnect-anubisvnc-activity-7121114100046168064-TDqK and https://twitter.com/Unit42_Intel/status/1715348477809402118 2023-10-18 (Wednesday): #IcedID forked variant infection with #BackConnect, #AnubisVNC, #CobaltStrike and #ScreenConnect. I saw "hands on keyboard" using ScreenConnect approximately 95 minutes after the initial infection. IOCs posted to Github at https://github.com/PaloAltoNetworks/Unit42-timely-threat-intel/blob/main/2023-10-18-IOCs-from-IcedID-forked-variant-with-VNC-and-Cobalt-Strike.txt #pcap of the infection and the associated malware/artifacts are available at https://www.malware-traffic-analysis.net/2023/10/18/index.html
This #IcedID #BackConnect C2 server keeps telling the bot to sleep for 60 seconds. This goes on for 3 hours. No reverse shell, no VNC, no file manager 😿
HELLO #TA577, IT’S TIME TO WAKE UP!!
🖥️ #VNC desktop graphics
🐀 #njRAT transfers and screenshots
🧊 #IcedID reverse VNC graphics
⌨️ #IcedID reverse VNC keylog
📂 #BackConnect file uploads
https://netresec.com/?b=23A41e6
NetworkMiner 2.8.1 Released
I am happy to announce the release of NetworkMiner 2.8.1 today! This new release brings a VNC parser to NetworkMiner, so that screenshots, keystrokes and clipboard data can be extracted from unencrypted VNC traffic. NetworkMiner 2.8.1 additionally includes parsers for command-and-control (C2) protoc[...]