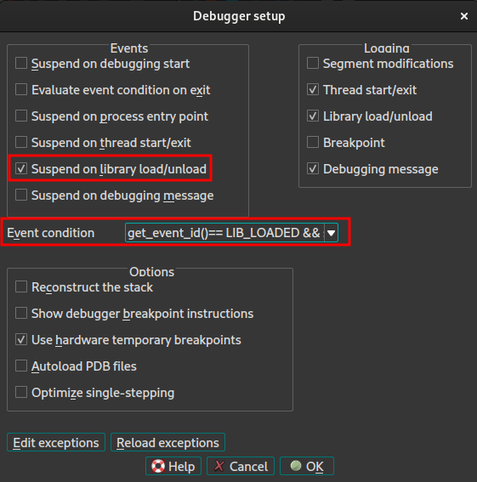
#mlget has been updated - your 1 stop shop for finding malware across different services!
Grab an updated copy at https://github.com/xorhex/mlget/releases/tag/v3.4.2
Happy to add additional services if folks know of more!
Some services I no longer have access to for testing - see the Alt text for more info.