Video interview joined by Dahvid Schloss (the WMD course developer at @JustHackingHQ ! 🤩) who shows off some of the basics of Windows malware development, from a standard shellcode loader to a more evasive dropper 😎 https://youtu.be/izf8ptPVh2g
John Hammond
@JohnHammond@infosec.exchange
- 6.4K Followers
- 96 Following
- 378 Posts
Hacker. Friends. Cybersecurity Researcher.
Learning Active Directory Certificate Service hacking-- with @Shikata! Starting with ESC8 using unauthenticated PetitPotam & Responder, we relay hashes to CA to get a certificate as the domain controller. This is the first video in an ADCS mini-series 😜 https://youtu.be/tYxJMr8jAgo
Big BIG thanks to @specopssoftware for sponsoring this video and their continued support of the channel! Protect your organization with stronger passwords, and continuously scan and block over FOUR BILLION breached passwords with Specops Software! https://jh.live/specops
Hunting for phishing kits, keying off a simple Telegram API request used to exfiltrate info to Telegram bots! Safari ride showcase of Microsoft login lures, Facebook, and more -- then we "make our own" to see them in action 🤪 https://youtu.be/sSuAKE7gjBM
Big thanks to @FlareSystems for sponsoring this video and their continued support of the channel! Track data on the dark web and manage threat intelligence for your exposed attack surface with Flare -- try a free trial and see what info is out there: https://jh.live/flare
Chatting with mah fwend and co-worker @JonnyJohnson_ to learn all about Event Tracing for Windows, and some super cool projects he has been working on: a lightweight and custom "toy EDR" JonMon and ETWInspector to help with Windows telemetry research! https://youtu.be/BNWAxJFL6uM
Playing with Windows Sandbox, following the recent reports of APT10 subgroup "MirrorFace" using it intentionally to execute malware without the watchful eye of antivirus or EDR -- because it's in a VM 😜 Shared folders still give access to the filesystem: https://youtu.be/O20WhmCspqo
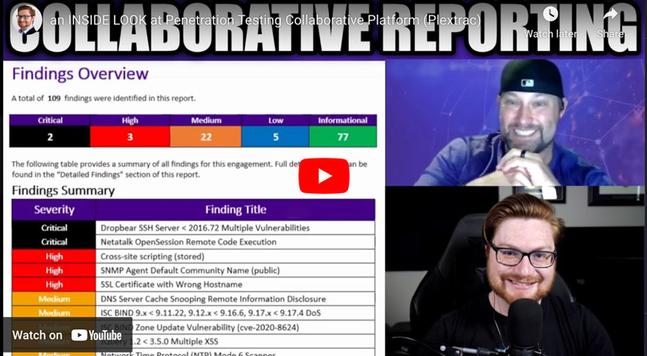
Big big thanks to @PlexTrac for sponsoring this video and their continued support of the channel! Save time and effort on pentest reports with PlexTrac's premiere reporting & collaborative platform: https://jh.live/plextrac-530 😎
Following the recent UNC6032 writeup from Mandiant with the stupid but clever "Unicode space padded filenames" trick for malware, I recorded an even more stupid video to recreate that in bad PowerShell code and then make a crappy Sigma rule to detect it 🙂 https://youtu.be/aj3uBl9hFxY
Big thanks to @Antisy_Training for sponsoring this video and their continued support of the channel! Check out their training material including their Pay Forward What You Can offering! https://jh.live/antisyphon
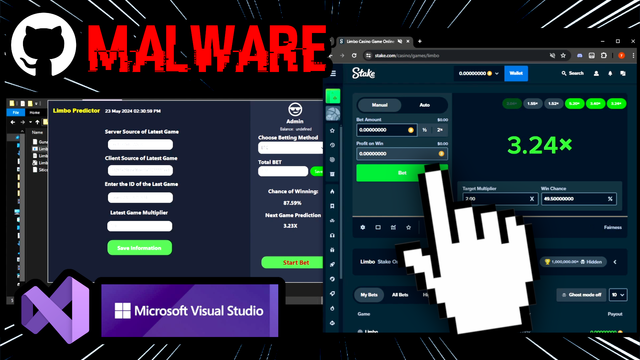
Exploring a backdoored Github repository abusing .suo deserialization, so just opening a Visual Studio solution file runs malware- then a PowerShell script pulls further payloads from social media... and we stumble onto the actor actively preparing more!👀 https://youtu.be/pw0xSFEnowk