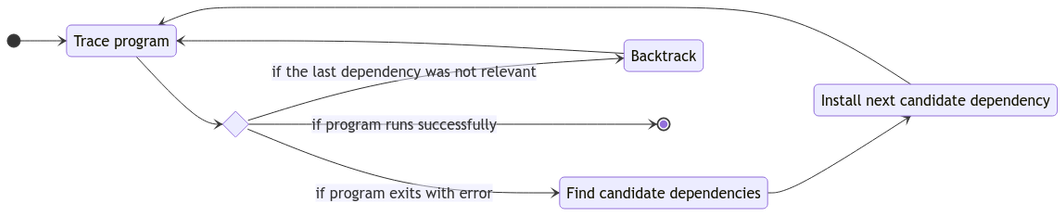
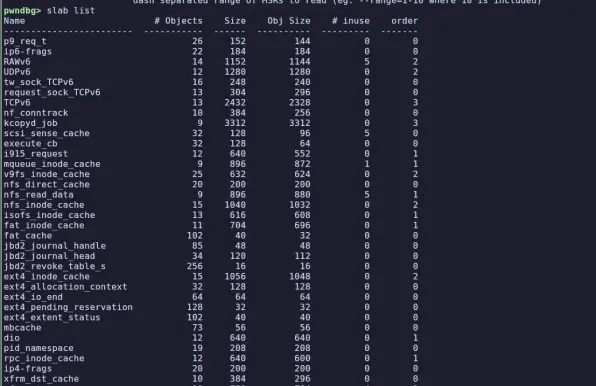
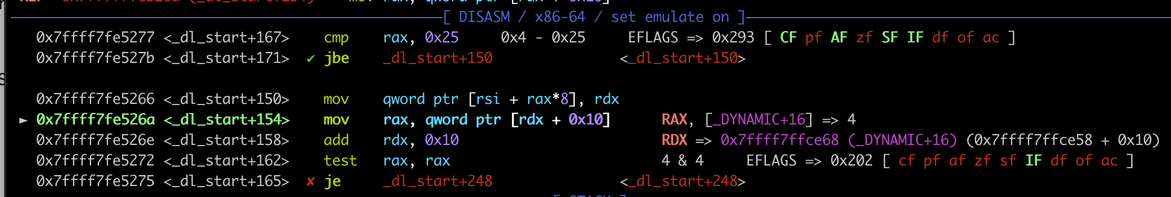
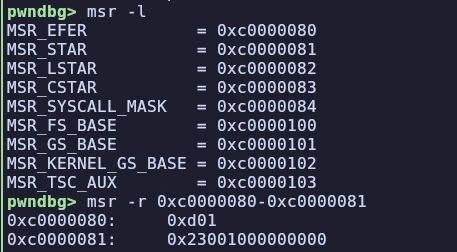
"Failed to compile: missing dependency" sound familiar?
Whether you're building open-source software or running mystery binaries, our new tool, Deptective automatically discovers the packages you need for successful execution.
Read the blog: https://blog.trailofbits.com/2025/07/08/investigate-your-dependencies-with-deptective/
Another tool in our software supply chain security arsenal. Try Deptective: https://github.com/trailofbits/deptective