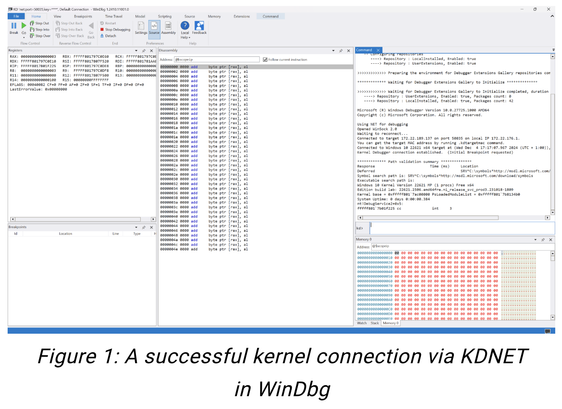
Our new Testing Handbook section on snapshot fuzzing helps security engineers test software that's traditionally difficult to analyze, such as kernel components and antivirus, where a single crash can take down the entire system.
Snapshot fuzzing captures memory and register states at critical execution points, allowing security engineers to:
- Test thousands of code paths without time-consuming system restarts
- Ensure fully deterministic testing where the same input always produces the same result
- Eliminate unreproducible crashes by starting each test from identical states
-Easily track code coverage and detect failures in emulated environments
In this section, we provide step-by-step instructions for building custom harnesses, fuzz campaigns, and more using What the Fuzz (wtf), an open-source snapshot-based fuzzer.
https://blog.trailofbits.com/2025/04/09/introducing-a-new-section-on-snapshot-fuzzing-for-kernel-level-testing-in-the-testing-handbook/