RossMadness
- 19 Followers
- 61 Following
- 767 Posts
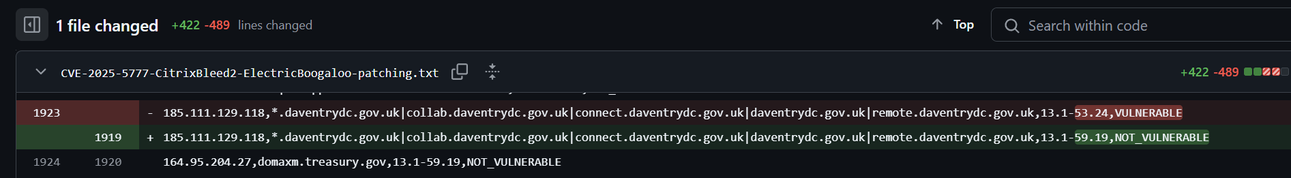
With the #CitrixBleed2 patch data I publish it's possible to view the history on Github for each new scan and see when hosts change from vuln to patched.
It's proving incredibly effective at getting orgs to patch. I tried private notifications via HackerOne and such for CitixBleed1 in 2023 and it took months to get orgs to patch. Putting the data public brings accountability for orgs who later get breached - so there's a rush to patch.
It's definitely interesting and may need a scale out.
And from the WTAF dept, quite a bombshell from ProPublica today:
"Microsoft is using engineers in China to help maintain the Defense Department’s computer systems — with minimal supervision by U.S. personnel — leaving some of the nation’s most sensitive data vulnerable to hacking from its leading cyber adversary, a ProPublica investigation has found."
"The arrangement, which was critical to Microsoft winning the federal government’s cloud computing business a decade ago, relies on U.S. citizens with security clearances to oversee the work and serve as a barrier against espionage and sabotage."
"But these workers, known as “digital escorts,” often lack the technical expertise to police foreign engineers with far more advanced skills, ProPublica found. Some are former military personnel with little coding experience who are paid barely more than minimum wage for the work."

A Little-Known Microsoft Program Could Expose the Defense Department to Chinese Hackers
The Pentagon bans foreign citizens from accessing highly sensitive data, but Microsoft bypasses this by using engineers in China and elsewhere to remotely instruct American “escorts” who may lack expertise to identify malicious code.
stop using twitter.
there are no more excuses.
get your news and your cti elsewhere.
the only reason the news and cti vendors stay on twitter is because you, the audience, are still there.
so leave.
take your clicks and your eyeballs to another platform.
it will make them leave.
dont wait for the critical mass to form
BE THE CRITICAL MASS
your body is a vote.
choose wisely.
@Richard_Littler Even if they were just trying to absorb info, they can't do it like that. Having info summarized for you means you don't absorb it. That's why we spend so much time explaining, solving problems, taking notes...
They think they're inventing "general intelligence" when they don't understand how their own brain works even on a surface, basic level.