I've started a blog to be able to share some projects I work on with my future self and curious others. It will mostly focus on stuff I do on my own time that might not be related to Blender. This site is still WIP, but two posts are up already.
Robert Gützkow
- 57 Followers
- 102 Following
- 98 Posts
Blender Studio has released its first game, DOGWALK, and it’s free! It was created by our incredible artists and developers using only open source tooling: Blender and the Godot Game engine.
https://store.steampowered.com/app/3775050/DOGWALK/
If you’d like to see more projects like this and/or want to browse the game source code, consider supporting the studio at studio.blender.org :)
CitrixBleed 2 update.
- Citrix have finally, quietly admitted exploitation in the wild -- by not commenting to press and then editing an old blog post and not mentioning it on their security update page.
- Orgs have been under attack from threat actors in Russia and China since June
- It's now under spray and pray, wide exploitation attempts.
https://doublepulsar.com/citrixbleed-2-situation-update-everybody-already-got-owned-503c6d06da9f
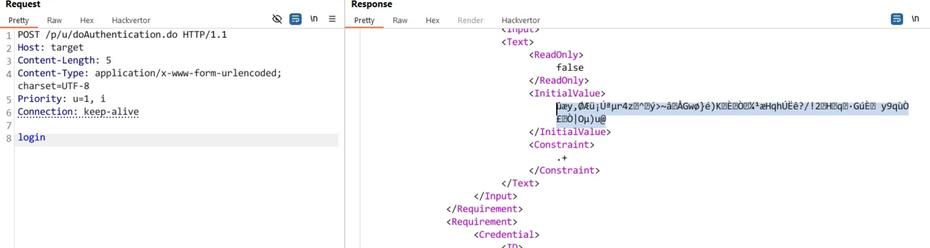
First exploitation details for CVE-2025-5777 - the Netscaler vuln - are out. https://labs.watchtowr.com/how-much-more-must-we-bleed-citrix-netscaler-memory-disclosure-citrixbleed-2-cve-2025-5777/
If you call the login page, it leaks memory in the response 🤣
I don’t want to specify too much extra technical info on this yet - but if you keep leaking the memory via requests, there’s a way to reestablish existing ICA sessions from the leaked memory.
DOGWALK will be officially released on July 11th, 17.00 CEST 🎉 join us then for our online release party!
Lots of frolicking in the snow and talking with artists, to be sure ☃️
#b3d #BlenderStudio #game #gamedev #OpenProject #DOGWALK
https://studio.blender.org/blog/dogwalk-release-date/
Have you worked on a cool project using Blender recently?
Share it at the upcoming Blender Conference 2025 in September! There’s one week left before the call for submissions closes. Check it out: https://conference.blender.org/2025/call-for-participation/ #b3d #bcon25
EU plant neues Massenüberwachungsgesetz mit Vorratsdatenspeicherung & Zwangs-Backdoors – jetzt ist noch Widerspruch möglich!
Hey Leute,
die EU plant gerade ein neues Gesetz zur Vorratsdatenspeicherung, das echt krass werden könnte. Es geht nicht nur um ein paar Verbindungsdaten, sondern darum, jeden Online-Dienst zur Überwachung zu verpflichten – also auch Messenger, Hosting-Anbieter, Webseiten usw.
Das Ganze läuft unter dem Titel:
„Retention of data by service providers for criminal proceedings“
Hier kann man bis zum 18. Juni 2025 Feedback abgeben: Have Your Say
Was ist geplant?
- Pflicht zur Datenspeicherung mit Identitätsbindung – also alles, was du online machst, muss auf dich zurückführbar sein.
- Sanktionen für Dienste, die keine Nutzerüberwachung einbauen – darunter könnten auch VPNs, selbstgehostete Sachen oder Open-Source-Projekte fallen.
- Backdoors in Geräte und Software – mit Hardwareherstellern soll zusammengearbeitet werden, um „gesetzlichen Zugriff“ zu ermöglichen.
- Auch kleine Anbieter betroffen – es geht ausdrücklich nicht nur um Meta, Google & Co.
Das Ganze basiert auf Empfehlungen einer „High Level Group“, deren Mitglieder komplett geheim gehalten werden. Patrick Breyer (Piraten/MEP) @echo_pbreyer hat nachgefragt – die EU hat ihm eine geschwärzte Liste geschickt.
Laut EDRi wurde die Zivilgesellschaft explizit ausgeschlossen. Lobbyismus deluxe.
Was kann man tun?
Einfach Feedback abgeben, geht in 2 Minuten.
Kurz schreiben, dass man gegen anlasslose Vorratsdatenspeicherung und Überwachung ist, reicht schon. Jeder Kommentar zählt.
Deadline ist der 18. Juni 2025, Mitternacht (Brüsseler Zeit).
Wäre gut, wenn wir aus der IT-Szene da nicht still bleiben. Das betrifft wirklich alle – Entwickler, Admins, SysOps, Hoster, ganz normale Nutzer.
Implementing stop-motion style animation for DOGWALK was fascinating.
We animated the characters on 2s (meaning 12 fps).
To make the movement sync up I made sure the animation blending & character rotation is matching that, instead of just using linear interpolation!